Method and device for detecting malicious website
A malicious website and detection method technology, applied in the computer field, can solve problems such as timely and effective, low detection efficiency of detection technology, limited auditors, etc., and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
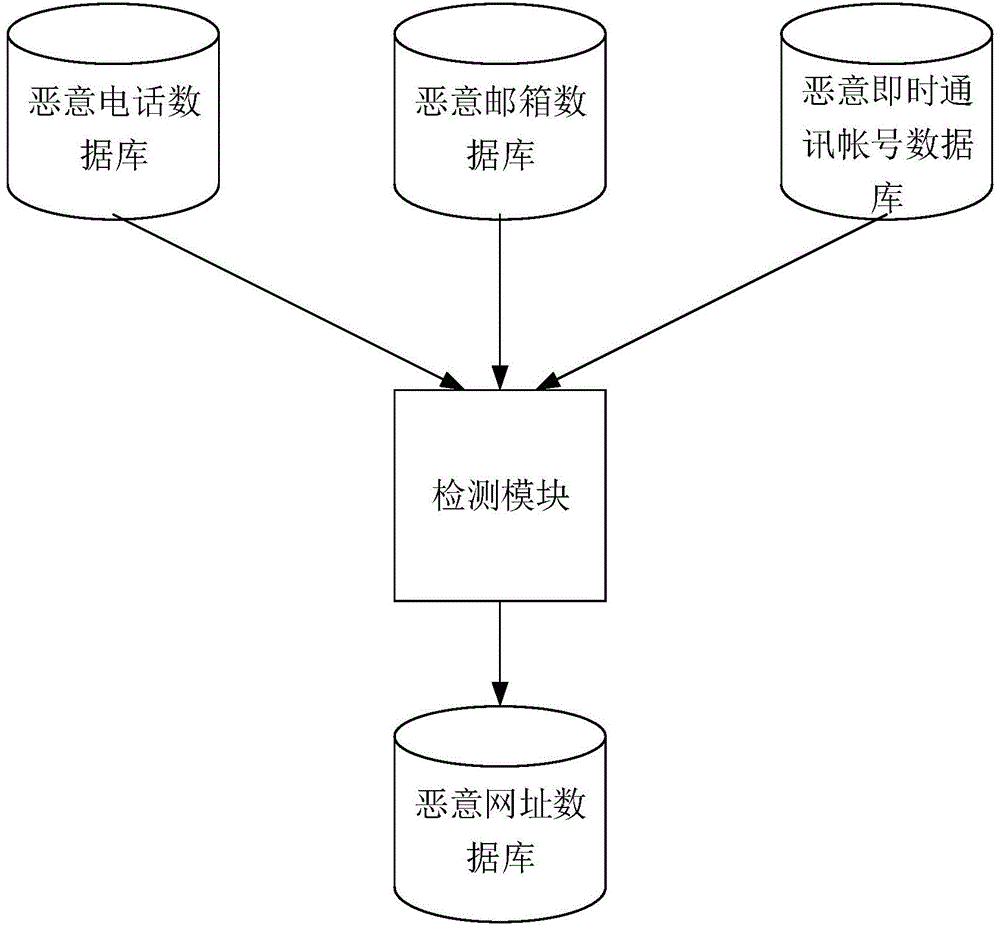
[0038] The malicious website detection method provided by the first embodiment of the present invention can be applied to a user terminal to realize the detection of malicious websites. User terminals can include such as image 3 The system architecture shown. like image 3 As shown, the system can be composed of a database of malicious contact information, a detection module and a database of malicious URLs.
[0039] Wherein, the malicious contact database may include, but is not limited to: a malicious phone database, a malicious email database, and a malicious instant messaging account database. The malicious call database stores the information and data of phone numbers determined to be malicious and fraudulent through various news releases, user reports, or collected through various tools and software, such as: through Tencent Mobile Manager, Sogou Number Link, Baidu Mobile Manager, 360 Mobile Malicious and fraudulent phone numbers collected by tool software such as De...
no. 2 example
[0053] Figure 5 It is a flow chart of the malicious website detection method provided by the second embodiment of the present invention. The malicious website detection method provided in this embodiment can be applied to a user terminal to detect malicious websites. like Figure 5 As shown, the malicious website detection method provided in this embodiment includes the following steps:
[0054] Step S21, obtaining the target URL of the target website, querying the database of malicious URLs, and obtaining target information data matching the target URL;
[0055] Information data of URLs determined to be malicious websites are stored in the malicious URL database. Specifically, the user terminal acquires the target website address of the target website to be visited included in the website access instruction triggered by the user, and queries the malicious website database for target information data matching the target website address.
[0056] Step S22, when the target ...
no. 3 example
[0069] Figure 7 It is a schematic structural diagram of a malicious website detection device provided in the third embodiment of the present invention. The malicious website detection apparatus provided in this embodiment can run in the user terminal 100, and is used for the malicious website detection method in the foregoing embodiments. like Figure 7 As shown, the malicious website detection device 30 includes: an extraction module 31 , an acquisition module 32 and a determination module 33 .
[0070] Wherein, the extracting module 31 is used to obtain the target webpage pointed to by the target URL of the target website to be visited, and extract the contact information in the target webpage;
[0071] An acquisition module 32, configured to query a database of malicious contact information, and obtain target information data matching the contact information in the target web page, the malicious contact information database stores information data of contact information ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com