Method and device for monitoring flow of virtual network
A technology of virtual network and traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
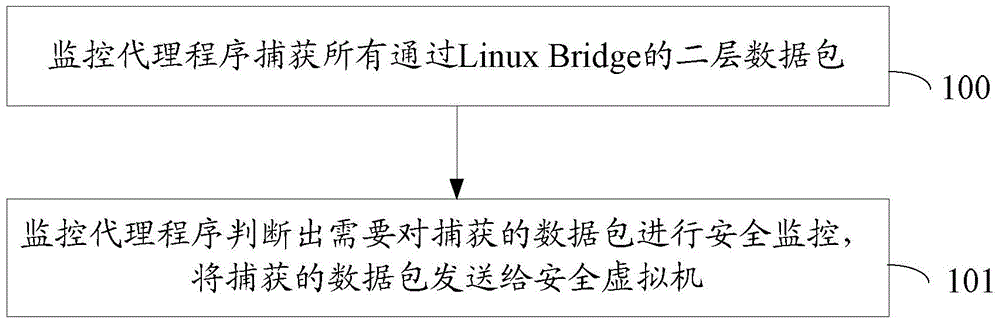
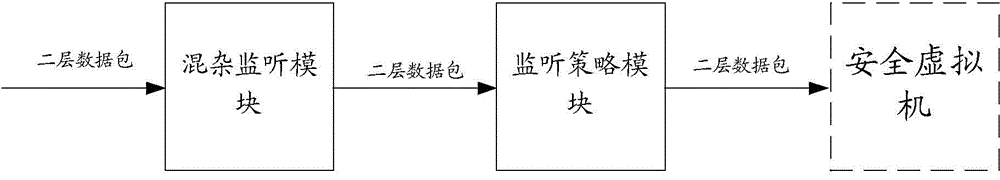
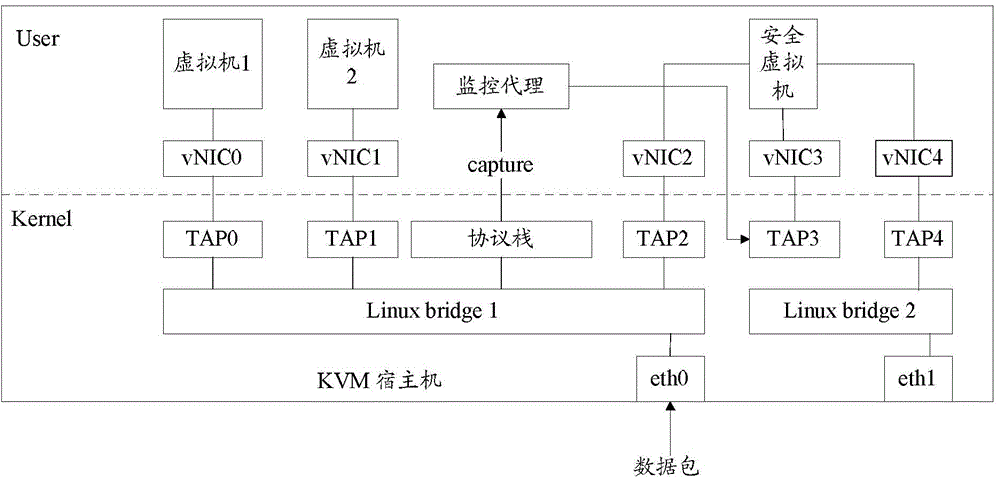
[0054] image 3 It is a schematic diagram of the deployment method of all related components and modules on the KVM host, such as image 3 As shown, the monitoring agent runs in the user state of the KVM host, and it uses the raw socket (RAWSocket) method to monitor the layer 2 data packets from LinuxBridge1.
[0055] When deploying a secure virtual machine, create virtual network devices such as LinuxBridge2, TAP2, TAP3, and TAP4 for the secure virtual machine, where TAP2 is connected to LinuxBridge1 where the business network is located to provide a management interface for the secure virtual machine; TAP3 is connected to vNIC3 is the packet capture port of the security virtual machine. The difference from other environments is that the data packets are written directly from the monitoring agent to the buffer of the TAP3 device. However, for the security virtual machine, this process is completely transparent and No modification is required; TAP4 is used for some security v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com