Identity authentication method and device
An identity authentication device and identity authentication technology are applied in the field of digital image processing and pattern recognition, which can solve the problems of poor anti-interference and low accuracy, and achieve the effects of enhanced anti-interference, easy implementation and improved accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the technical problems, technical solutions and advantages to be solved by the present invention clearer, the following will describe in detail with reference to the drawings and specific embodiments.
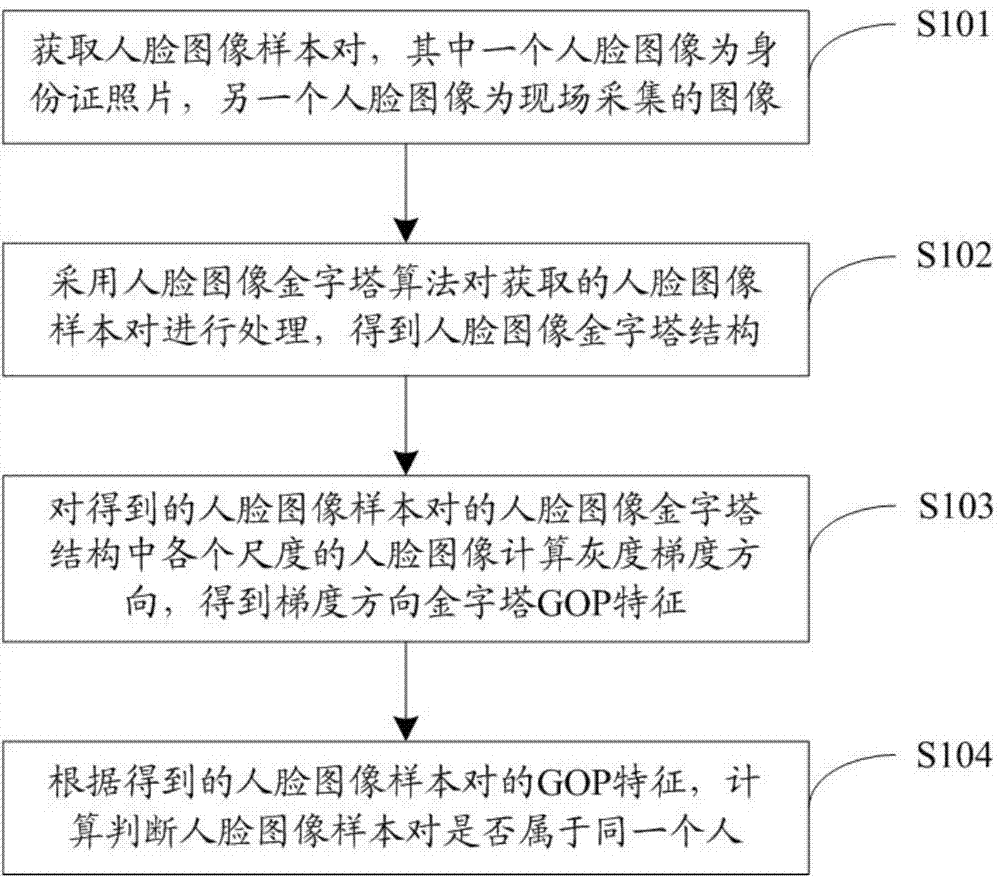
[0026] On the one hand, the present invention provides an identity authentication method, such as figure 1 shown, including:
[0027] Step S101: Obtain a face image sample pair, wherein one face image is a photo of an ID card, and the other face image is an image collected on site;
[0028] In this step, the images collected on site can be obtained by intercepting the collected video samples, or by taking pictures on site.
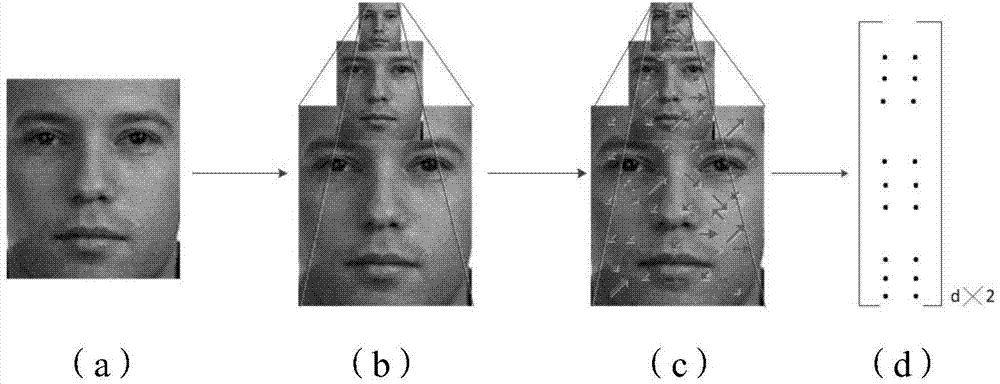
[0029] Step S102: using the face image pyramid algorithm to process the acquired face image sample pairs to obtain a face image pyramid structure;
[0030] In this step, the face image pyramid structure is used to represent the face image at multiple scales and resolutions. This algorithm can fully describe the features of the face...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com