A Dynamic Hiding Method of Website Links Effectively Preventing Network Attacks
A website link and network attack technology, applied in transmission systems, electrical components, etc., can solve the problems of increasing the difficulty of user interaction with the website, unable to eliminate ticket grabbing, number swiping, and complexity, and achieve protection against hazards and service performance. , the effect of protecting against malicious code or malware, and preventing credential stuffing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
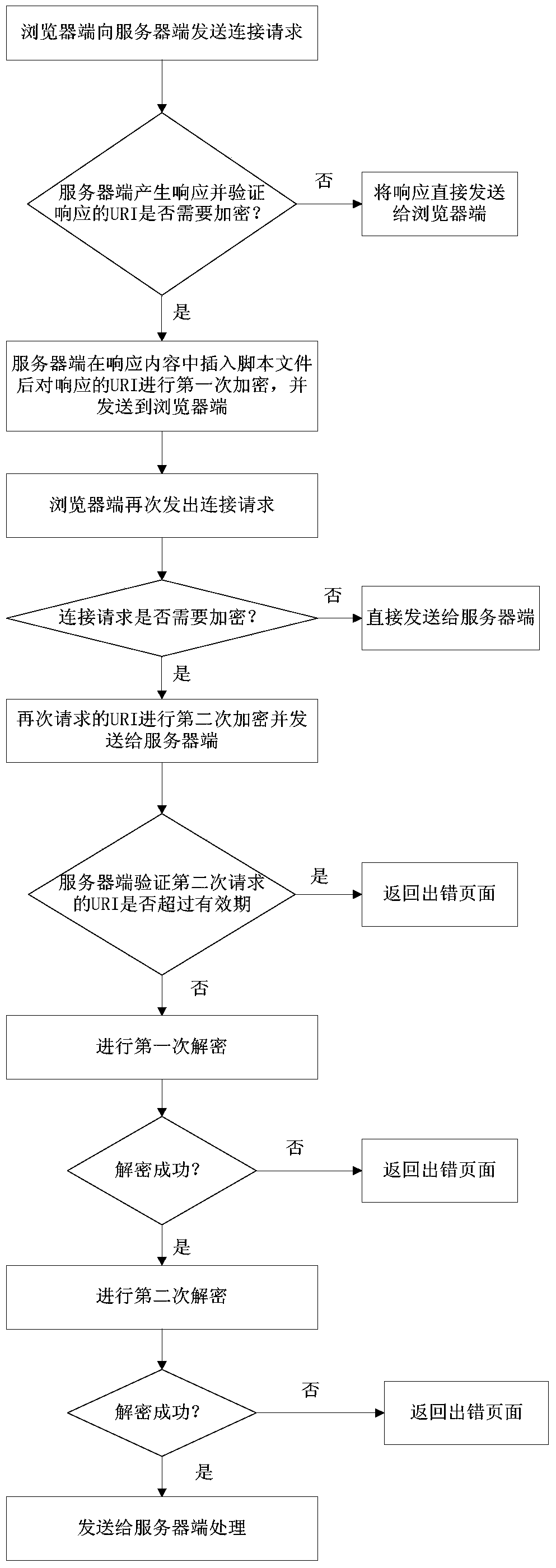
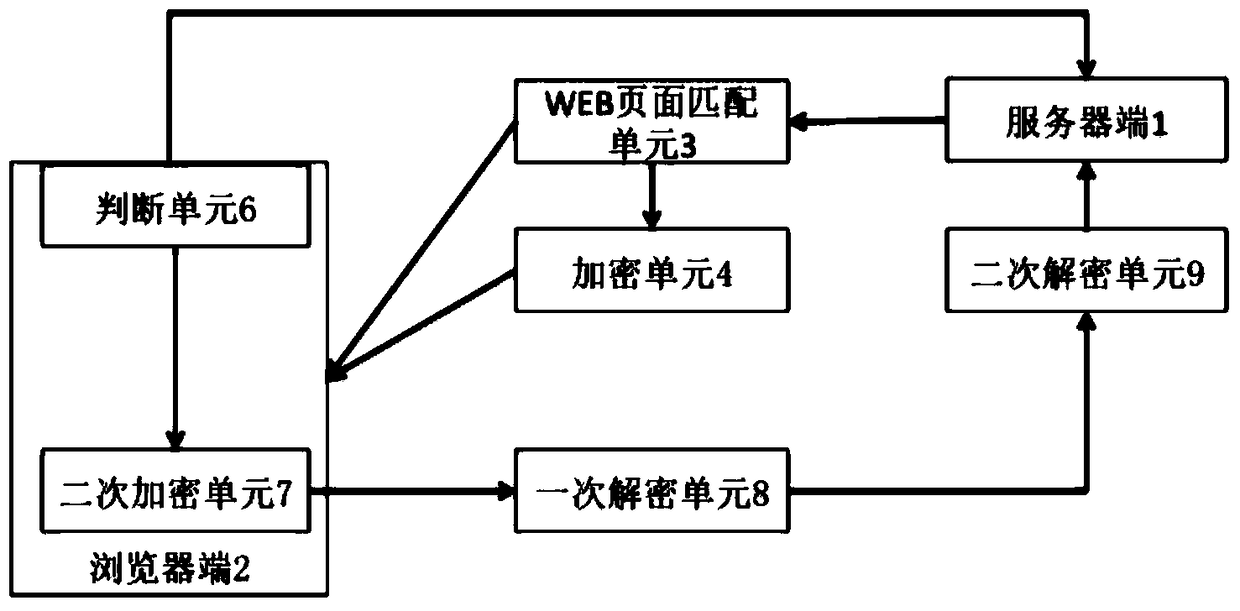
[0046] see figure 1 As shown in the schematic flow diagram, the WEB website link dynamic hiding method for effectively preventing network attacks of the present invention comprises the following steps:
[0047]Step S11, the browser sends a connection request to the server, which is the first step for the browser to interact with the server. This step can be the first time the browser tries to establish a connection with the server, or it can be that the browser has already connected with the website server A connection has been established, that is, staying on the webpage, but the connection between the browser and the server has been disconnected. When clicking a button on the website page again, such as the login button, the browser sends a connection request to the server.
[0048] Step S12, the server verifies whether the URI of the response needs to be encrypted, and if not, sends the URI of the response directly to the browser; otherwise, encrypts the URI requested by th...
Embodiment 2
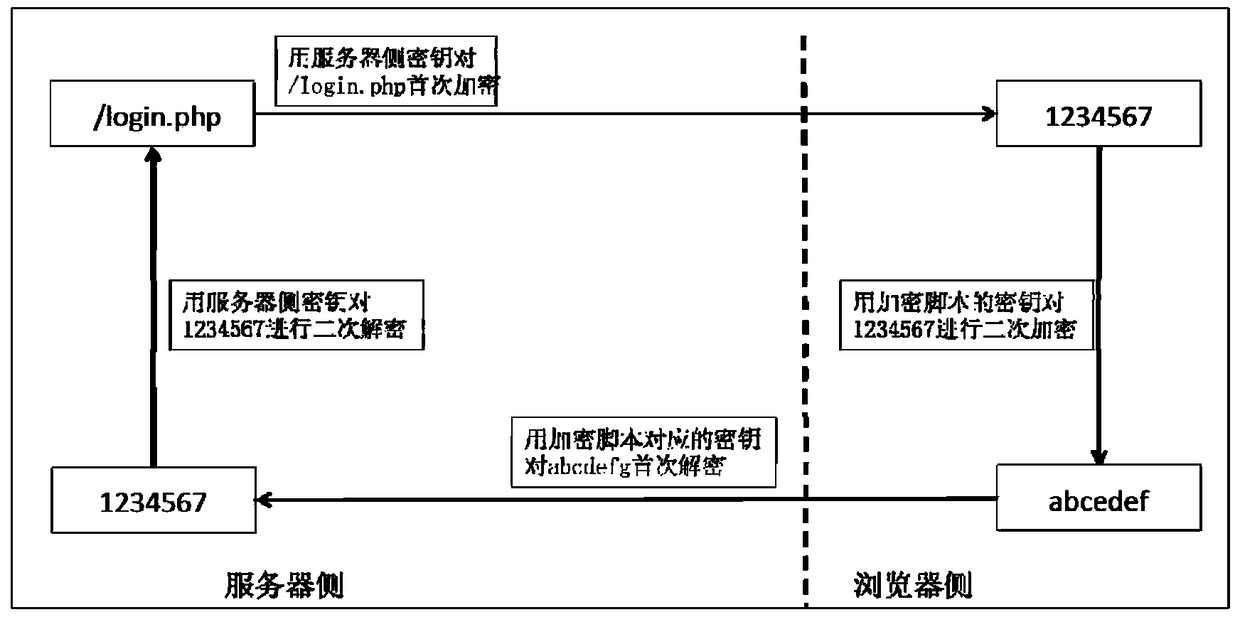
[0084] Next, the structure of the present invention will be further explained by taking the present invention applied to the 12306 website to solve ticket grabbing behavior as an example.
[0085] First, analyze the ticket grabbing behavior on the 12306 website. Various ticket grabbing software find several key URLs by analyzing the structure of the 12306 ticket buying website, and then use scripts to continuously check these key URLs. Submit parameters to achieve the purpose of automatic and programmatic ticket grabbing, and its efficiency is hundreds of times faster than that of general manual clicking on the website.
[0086] On the 2014 version of the 12306 website, the URLs of several key pages such as user login, ticket query, and order submission are as follows:
[0087] Request login page: https: / / kyfw.12306.cn / otn / login / init
[0088] Get verification code and check
[0089] Passcode: https: / / kyfw.12306.cn / otn / passcodeNew / getPassCodeNew? module=login&r and=sjrand& ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com