Method and device for identifying bad conversation
A technology of bad and call information, applied in the field of communication, can solve the problems of money being deceived and the inability to identify fraudulent phone calls, and achieve the effect of reducing trouble and loss and achieving high accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
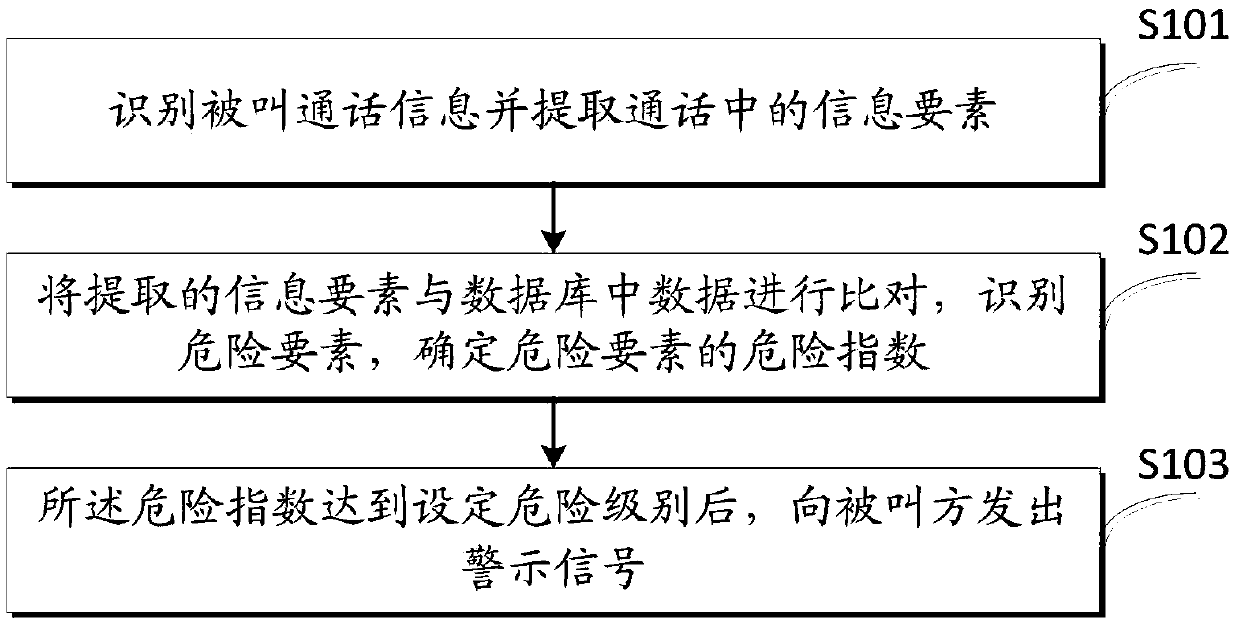
[0069] like image 3 As shown, the first embodiment of the present invention proposes a method for identifying bad calls, including:
[0070] S101, identifying the called call information and extracting information elements in the call content;
[0071] Specifically, when the mobile terminal receives the called call, it recognizes the information of the called call. The information of the called call includes the address of the calling number, the type of the calling voice, and the voice information key contained in the real-time voice topic information. Words, caller voiceprint feature information, topic type initiated by the caller, etc. The attribution of the calling number is identified according to the number segment of the calling number. The main voice type mainly refers to whether the calling is a manual call or a computer call. Through the intonation and audio of the caller's speech, it can be identified whether it is a computer voice or a manual voice. . The speec...
Embodiment 2
[0082] like Figure 4 As shown, the second embodiment of the present invention proposes a method for identifying bad calls, including:
[0083] S201, identifying the called call information and extracting information elements in the call content;
[0084] S202, comparing the extracted information elements with the data in the database, identifying the dangerous elements, and determining the risk index of the dangerous elements;
[0085] S203. After the risk index reaches a set risk level, send a warning signal to the called party;
[0086] S204. Take security measures to prevent damage from occurring.
[0087] Specifically, the security measures refer to actively taking measures to avoid losses, including disconnecting from the network, and not accepting requests from the machine to send information through the Internet, such as requests from the caller to send a verification code, or requests from the caller to send a bank account number. If it is judged that the content o...
Embodiment 3
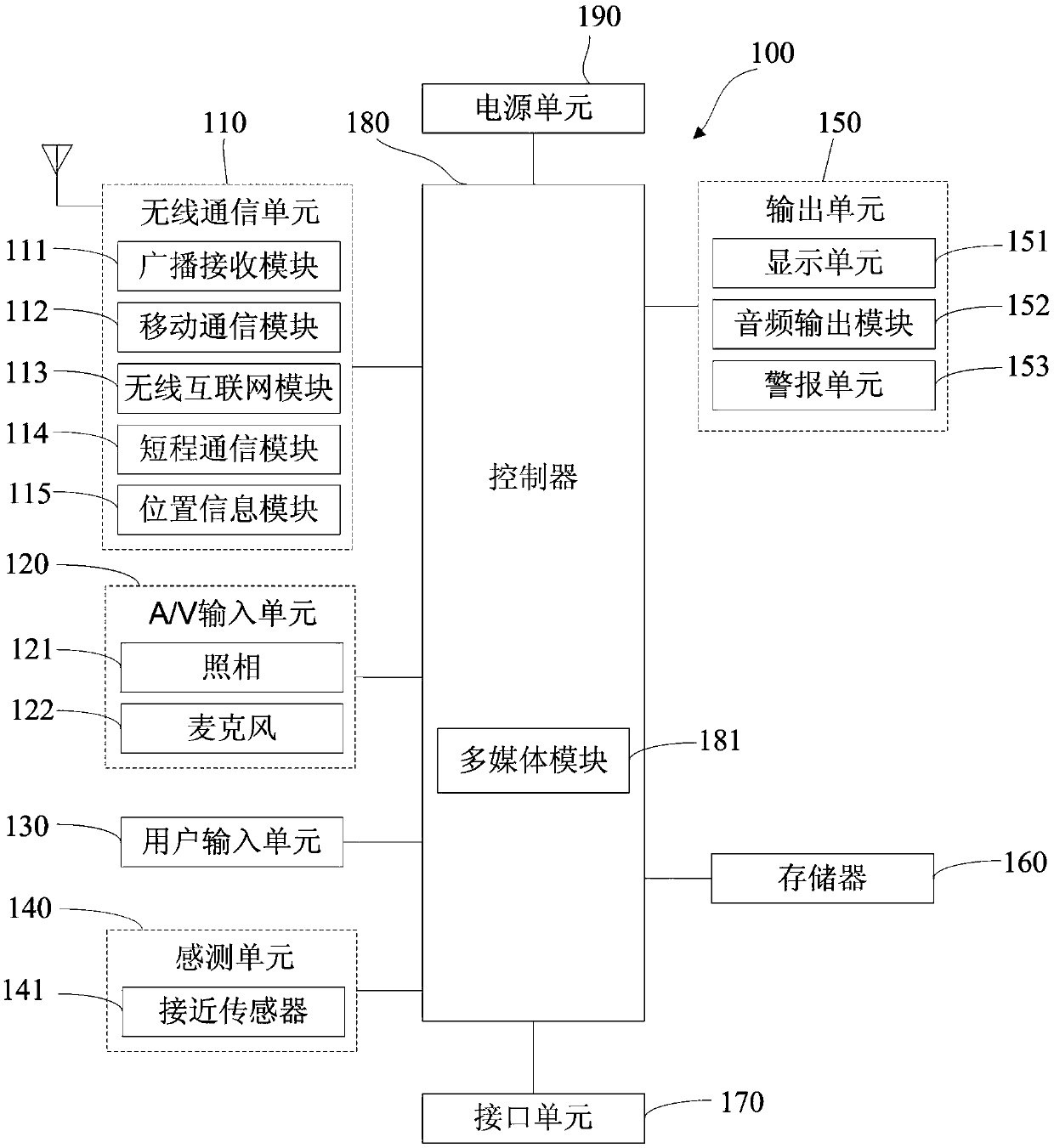
[0090] like Figure 5 As shown, the third embodiment of the present invention proposes a device for identifying bad calls, including: an identification and extraction unit 10 , a comparison unit 20 , and a warning unit 30 .
[0091] The identifying and extracting unit 10 is configured to identify the called call information and extract information elements in the call content.
[0092] Specifically, the identification and extraction unit 10 is as Figure 7 As shown, it includes a calling party identification and extraction subunit 11 and a called party identification and extraction subunit 12.
[0093] The calling party identification and extraction subunit 12 is set to: when the mobile terminal receives the called call, identify the information of the called call, the information of the called call includes, the calling number attribution, the type of calling voice, real-time The voice information keywords contained in the voice topic information, the caller's voiceprint fe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com