Anti-kernel-hook method based on address randomization
An address and kernel technology, applied in computer security devices, program/content distribution protection, instruments, etc., can solve problems such as high performance overhead, limited effect, and insufficient timeliness, to reduce performance overhead, enhance integrity and security, Effect of Kernel Protection Assurance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
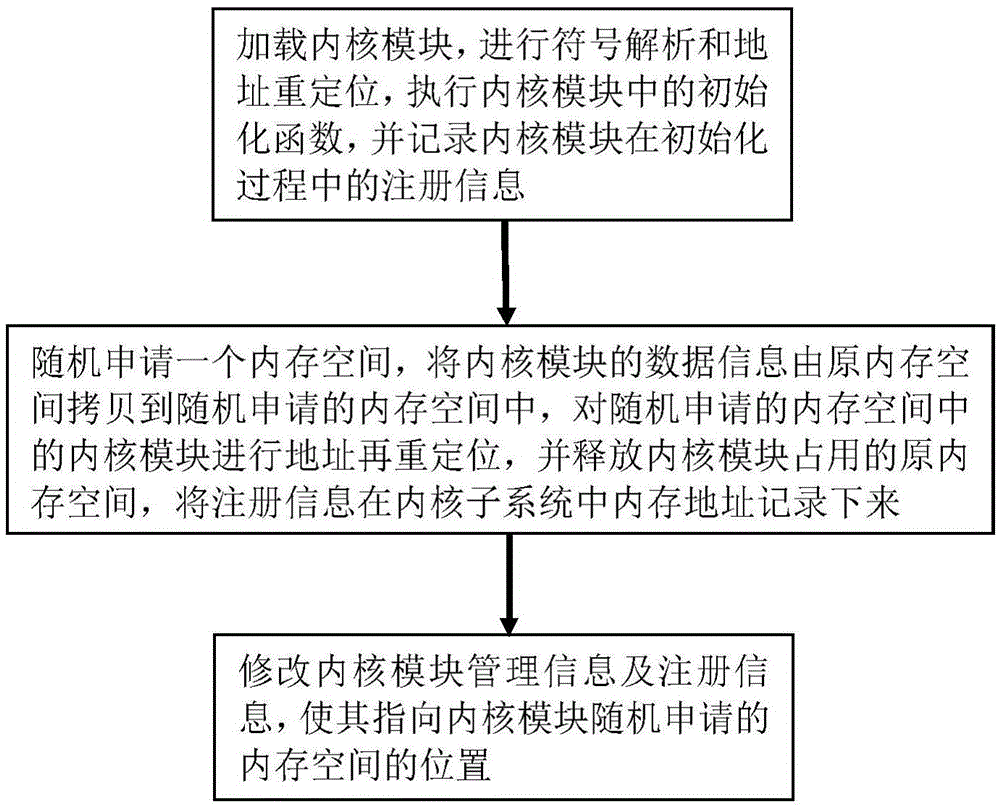
[0035] Example 1, see figure 1 As shown, an anti-kernel hooking method based on address randomization includes the following steps:
[0036] Step 1. Load the kernel module, perform symbol analysis and address relocation, execute the initialization function in the kernel module, and record the registration information of the kernel module during the initialization process. The memory space area occupied by the memory module includes the module initialization area and the module core area. After initialization, the module initialization area is released;
[0037] Step 2. Randomly apply for a memory space, copy the data information of the kernel module from the original memory space to the randomly applied memory space, relocate the address of the kernel module in the randomly applied memory space, and release the kernel module occupied In the original memory space, the registration information is recorded in the memory address of the kernel subsystem;
[0038]Step 3. Modify th...
Embodiment 2
[0039] Example 2, see Figures 1 to 3 As shown, an anti-kernel hooking method based on address randomization includes the following steps:
[0040] Step 1. Load the kernel module, perform symbol analysis and address relocation, execute the initialization function in the kernel module, and record the registration information of the kernel module during the initialization process. The memory space area occupied by the memory module includes the module initialization area and the module core area. After initialization, the module initialization area is released, which includes the following steps:
[0041] Step 1.1 Load the section information in the kernel module into the module initialization area and the module core area respectively. After the kernel module is initialized, the module initialization area is released, and the module core area resides in the memory space until the kernel module is unloaded;
[0042] Step 1.2 Convert the kernel module's own symbols and the exter...
Embodiment 3
[0053] Example three, participate in Figures 1 to 9 As shown, in conjunction with specific embodiment, the present invention is further described in further detail:
[0054] Load the kernel module in the normal way, perform symbol analysis and address relocation, execute the initialization function in the kernel module, complete the preparation of the kernel module, record the registration information of the kernel module during the initialization process, and the memory space area occupied by the kernel module Contains module_init and module_core. According to the section information in the module, the sections in the module are loaded into the module_init and module_core areas of the memory respectively. The section information of the module can be viewed through the tool readelf, where the sections whose names start with .init are loaded into In the module_init area of the memory, after the module initialization function is executed, the module_init area will be released...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com