General surrogate key generation method for identity-based proxy cryptography method
A technology for generating a method and a surrogate key, applied in the field of information security, can solve the problems of increasing design cost and time overhead, reducing the security of the scheme, reducing security, etc., to improve convenience and security, and save computing costs and computational costs. small effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
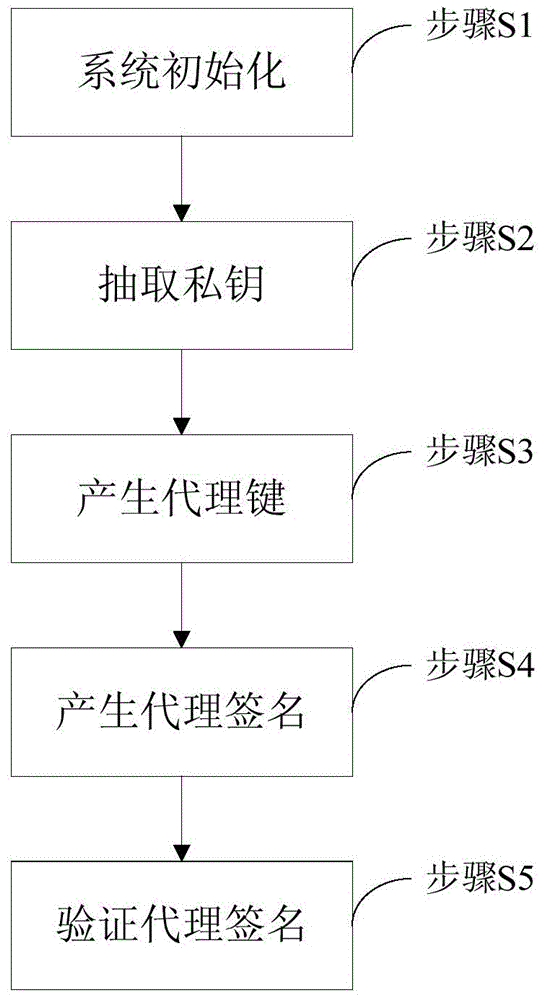
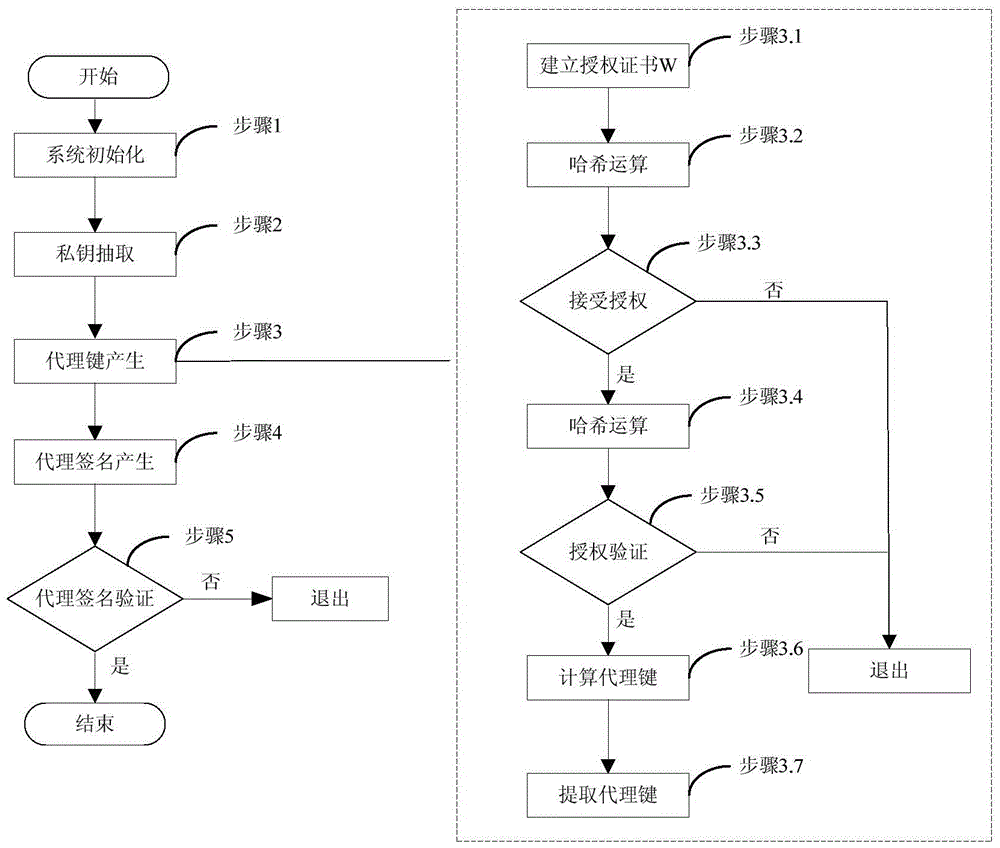
[0037] based on the following Figure 1 ~ Figure 3 , specifically explain the preferred embodiment of the present invention.
[0038] like figure 1 As shown, the present invention provides a general surrogate key generation method in the identity-based surrogate encryption method, and the general surrogate key generation method can be applied to any known identity-based cryptography method. The general surrogate key The generation method includes the following steps:
[0039] Step S101, the original operator O establishes the authorization certificate Warrant, and directly uses the authorization certificate Warrant as the proxy public key;
[0040] Among them, the authorization certificate Warrant includes the identity information of the original operator O, the identity information of the agent operator P, the content of the agent authorization, the date range, etc.;
[0041] Step S102, the original operator O uses the private key d of the original operator o Encrypt the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com