Security energy efficiency monitoring terminal based on tamper-proof technology and monitoring method of security energy efficiency monitoring terminal
A monitoring terminal and anti-tampering technology, applied in signal transmission systems, instruments, etc., can solve the problems of malicious tampering of embedded software, inability to guarantee energy efficiency data security, etc., achieving good real-time performance, simplifying interface design, and reducing the burden.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
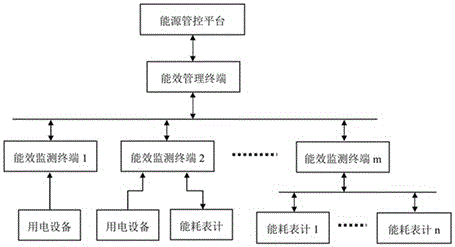
[0033] The invention provides a safe energy efficiency monitoring method and an energy efficiency monitoring terminal based on anti-tampering technology. On the one hand, the energy efficiency monitoring terminal is connected to various electrical equipment and energy consumption meters, and the energy consumption monitoring terminal reports the collected energy efficiency data, corresponding alarm information, and normal information to the management and control platform.
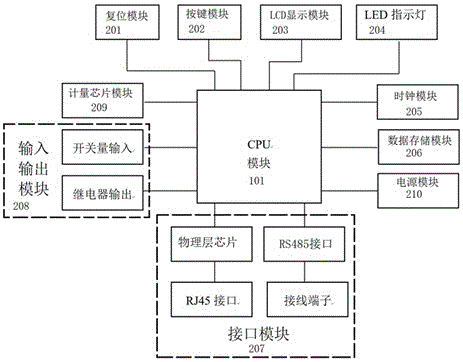
[0034] Among them, the security energy efficiency monitoring terminal based on anti-tampering technology is attached figure 1 As shown, it includes a CPU module 101, a reset module 201 connected to the CPU module, a key module 202, an LCD display module 203, an LED indicator light 204, a clock module 205, a data storage module 206, an interface module 207, an input and output module 208, and a measurement Chip module 209, and power module 210, it is characterized in that, described interface module compris...
Embodiment 2
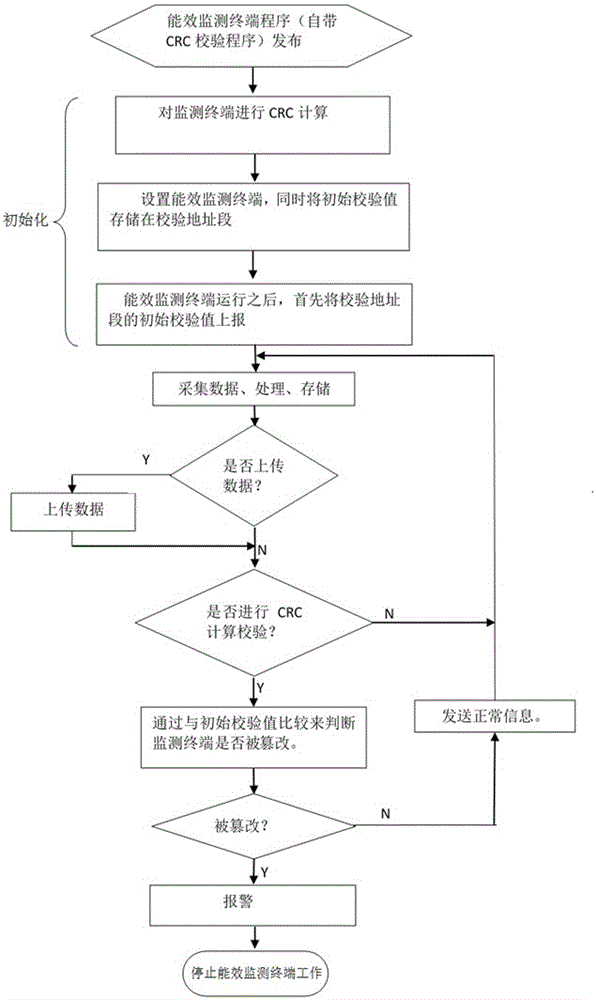
[0044] The monitoring terminal described in Embodiment 1 adopts a CRC calculation and verification algorithm and a corresponding comparison and judgment mechanism. In order to ensure that key information such as CRC calculation and verification address segments are not tampered with, and to ensure that the management and control platform can correctly determine whether the energy efficiency monitoring terminal is working safely, these key information are packaged in the form of library files during design. Developers can only obtain the information through the function interface, but cannot modify these key information.
[0045] At the same time, set the verification and judgment cycle in the third step to 1 second
[0046] In terms of hardware, in order to meet the needs of existing electrical equipment and meters connected to the RS485 field communication network, this embodiment further designs multiple interfaces such as RS232, RS485, RJ45, 4-20mA / 0-10V, etc. in the hardwa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com