Network-security-risk analysis method based on network node vulnerability and attack information
A network node and network security technology, applied in the field of network security, can solve problems such as inaccurate security risk analysis results and incomplete static information acquisition, so as to improve analysis capabilities, improve network risk analysis results, and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
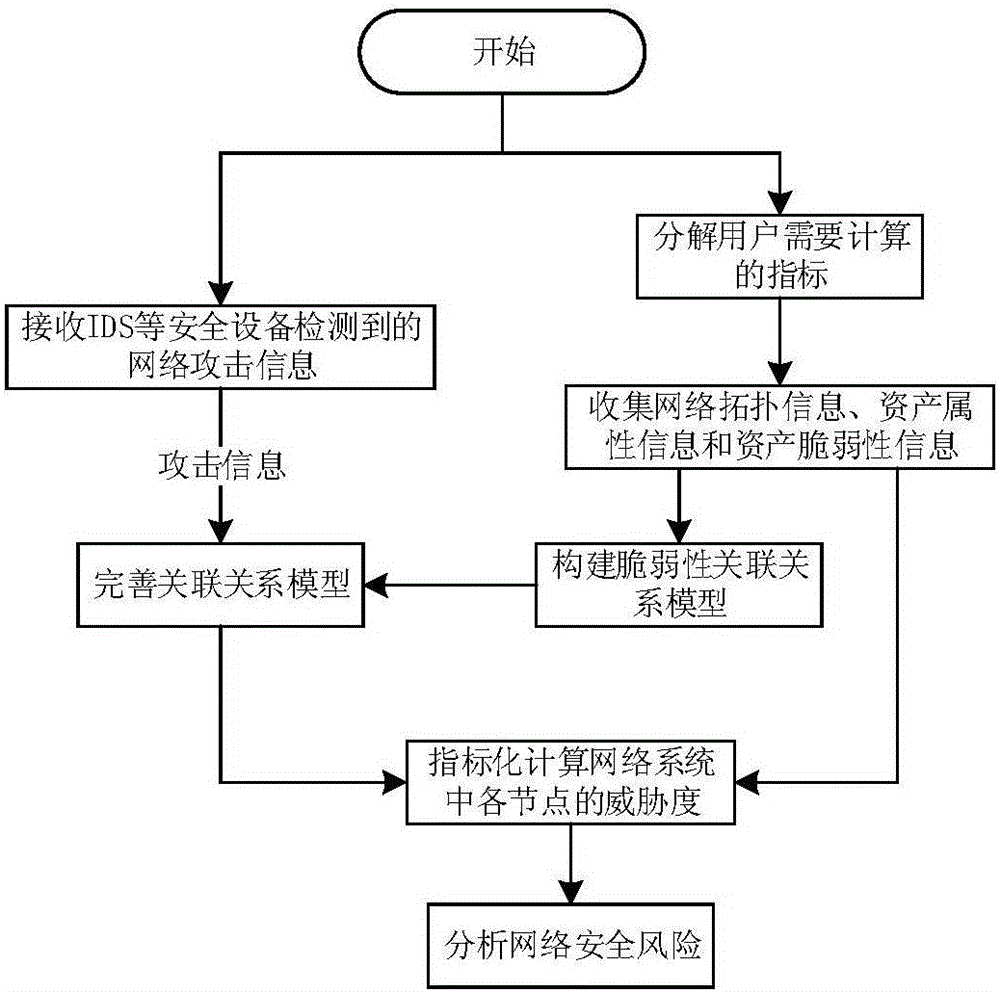
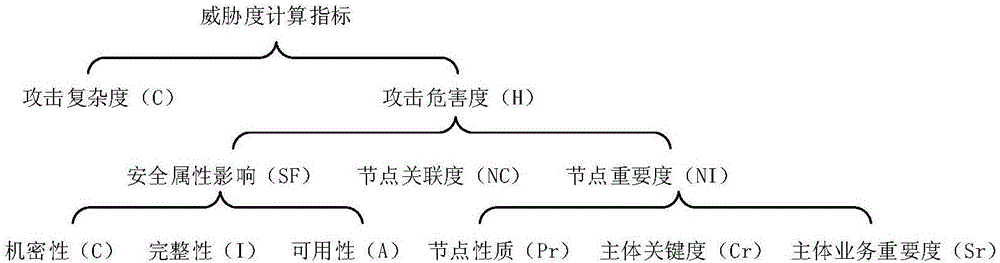
[0044] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
[0045] The theoretical basis of related concepts in the present invention is as follows:
[0046] Information system: It is composed of computers and related and supporting equipment and facilities (including networks). It is a man-machine system that collects, processes, stores, transmits, and retrieves information according to certain application objectives and rules;
[0047] Threat: A potential cause of an undesired incident that could result in harm to a system or organization;
[0048] Vulnerability: An asset or a weakness of several assets that may be exploited by a threat;
[0049] Associations include physical associations and logical associations. Physical associations include physic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com