Network authentication method, access control method and network access equipment
A technology for network access equipment and network authentication, which is applied in the fields of access control methods, network access equipment and network authentication methods, and can solve the problems of wireless network occupation and easy cracking of wireless passwords.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
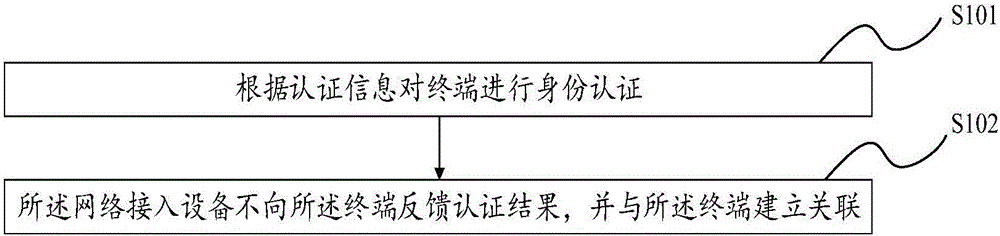
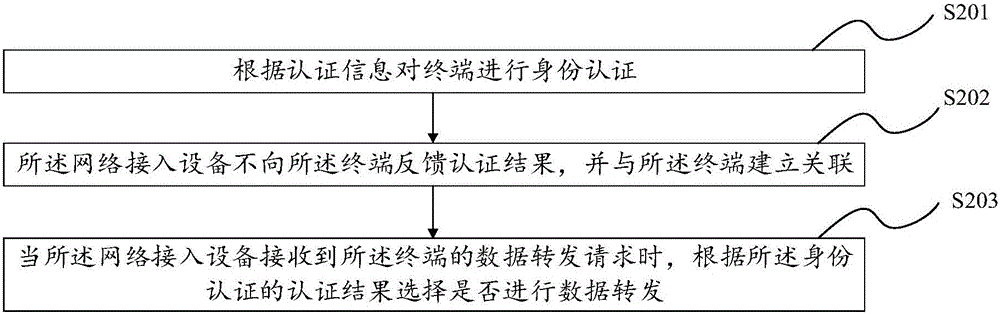
[0039] According to the existing authentication mechanism for network access, the network terminal device can continuously send authentication information to the network access device for identity authentication, thus causing a hidden danger to network security. Illegal users can try to authenticate by brute force cracking, and finally achieve the purpose of password cracking and occupying network bandwidth. For some simple passwords, the current cracking method only takes a few minutes.
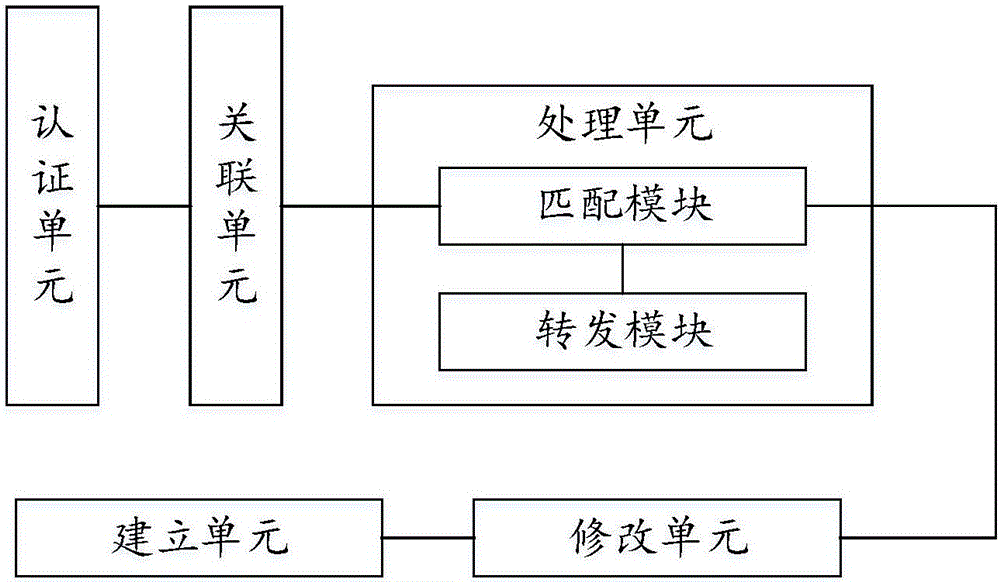
[0040] In view of the above technical problems in the prior art, after completing the authentication information for the terminal in this embodiment of the present invention, since the network access device does not feed back the corresponding verification result, but directly establishes an association with the terminal, the connected user does not It is not known whether the access is really successful, so that the illegal user can not confirm whether the correct password has been cracked,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com