Safety data acquisition and anomaly detection method and system facing industrial control network
An industrial control network and security data technology, applied in the field of security data collection and anomaly detection, can solve the problems of inability to cope with APT attacks, limited security data collection range, restricting the implementation and promotion of security solutions, etc., to improve the ability to resist APT attacks , the effect of reducing casualties and property damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the present invention will be described in detail below in conjunction with the accompanying drawings.
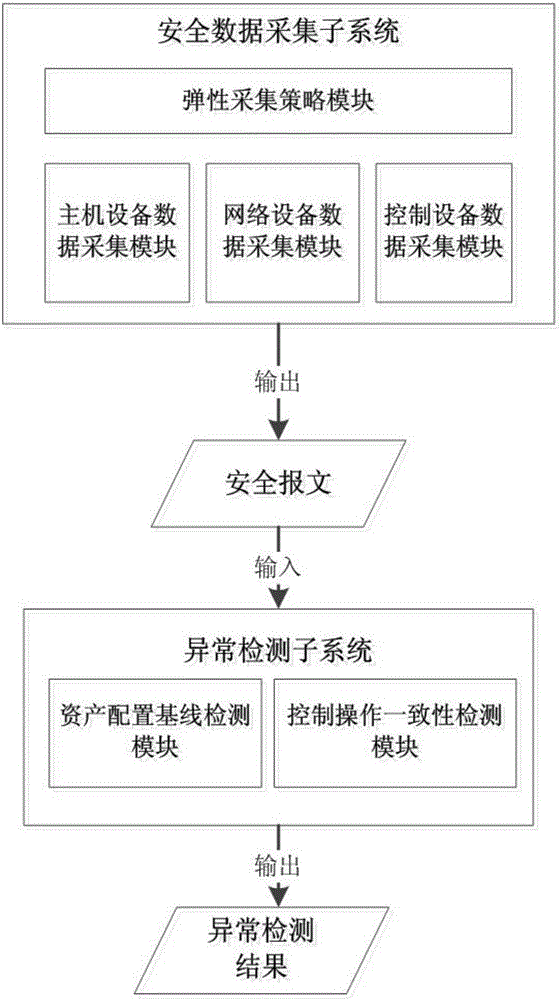
[0032] 1. figure 1 It is a schematic diagram of the system operation flow chart of the present invention. Such as figure 1 As shown, the system includes:
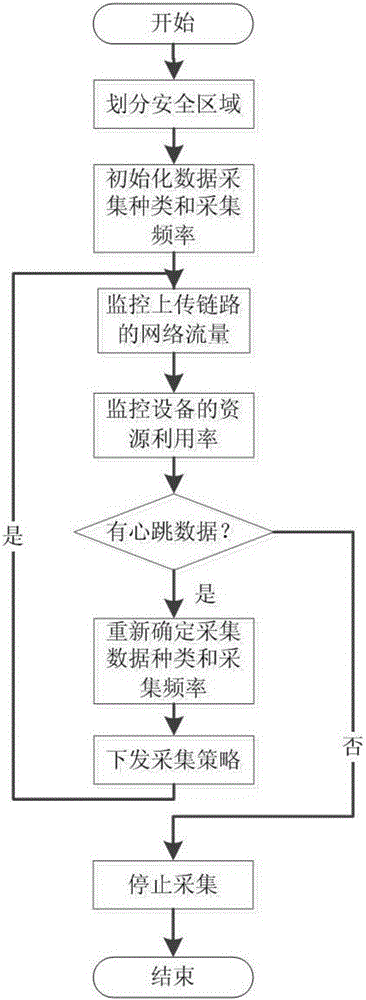
[0033] 1) The security data collection subsystem is composed of a host device data collection module, a network device data collection module, a control device data collection module and an elastic collection strategy module. And generate a security message in JSON format, and the security message is stored in a distributed database; the assets include Web server, mail server, ERP system server, OA system server, host computer, history library server, real-time library server, Switches, firewalls, one-way gatekeepers, IDS / IPS, PLC controllers, DCS controllers, etc.;
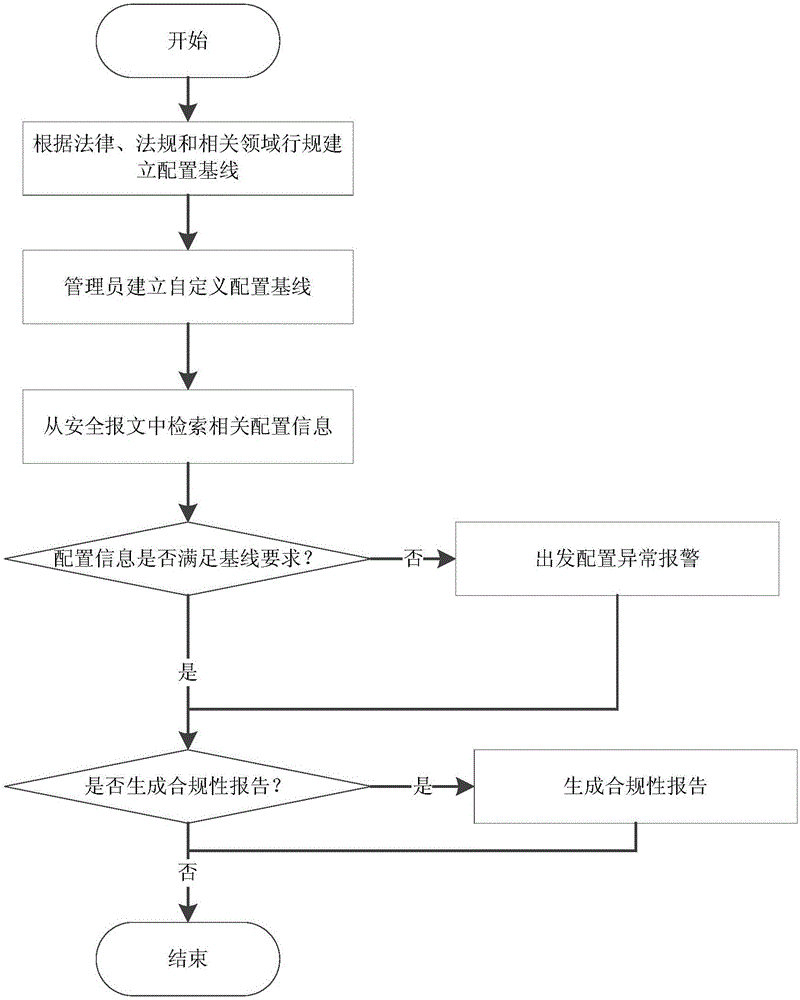
[0034] 2) The anomaly dete...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com