Codebook design method for resisting passive eavesdropping in MISO system based on weighting Voronoi graph
A design method and codebook technology, applied in transmission systems, radio transmission systems, diversity/multi-antenna systems, etc., can solve the problems of inaccurate beamforming at the transmitting end, leakage of user information, and impact on system security rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
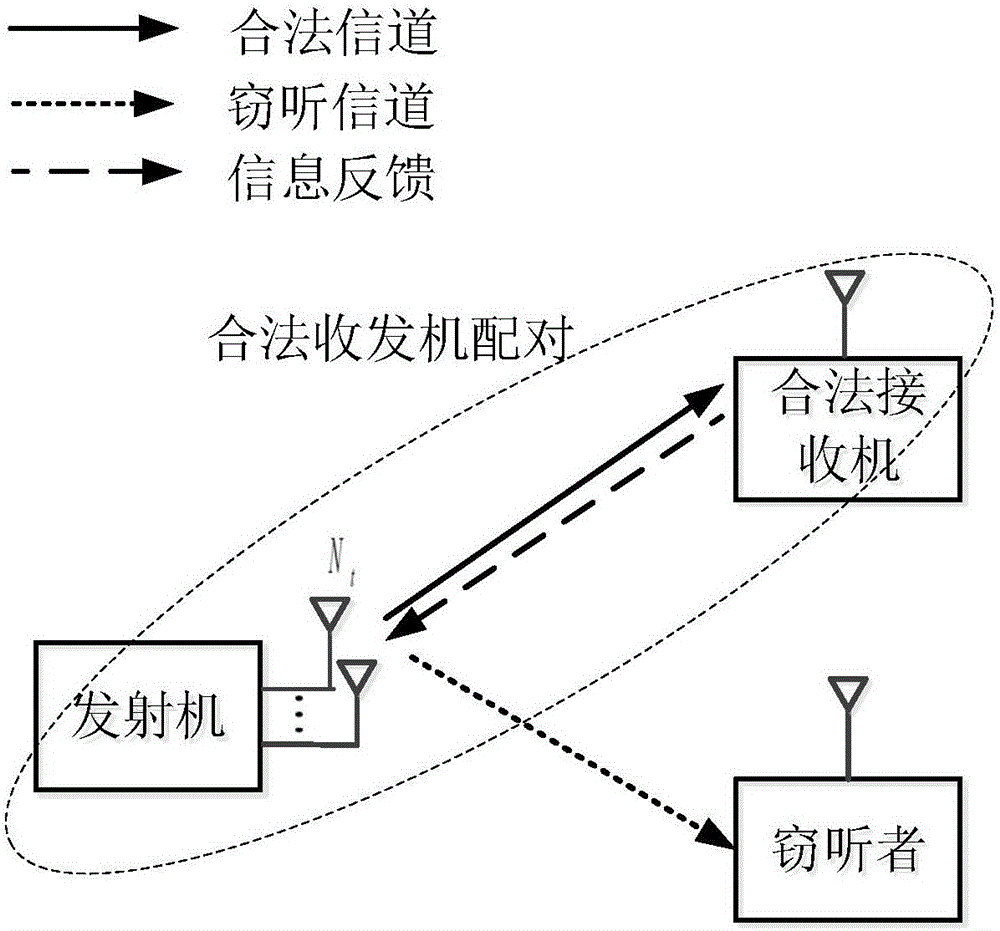
[0059] The structural representation of the system model of the present invention is as figure 1 As shown, the present invention is based on a legitimate transceiver pair and an eavesdropper, the transmitter has N t root antenna, both the legitimate receiver and the eavesdropper have a single antenna, and the receiving signal models of the legitimate receiver and the eavesdropper are:
[0060] y L = P Σ L G w s + n L , y E = P Σ E G w s + n E ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com