Coefficient mapping transformation-based polynomial complete homomorphic encryption method and system
A technology of homomorphic encryption and mapping transformation, applied in the field of information security, can solve the problems of no commercial application instance of homomorphic encryption algorithm, large computing and storage resources, and inability to effectively control noise, etc. The effect of speed increase, ciphertext size and expansion speed is small
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
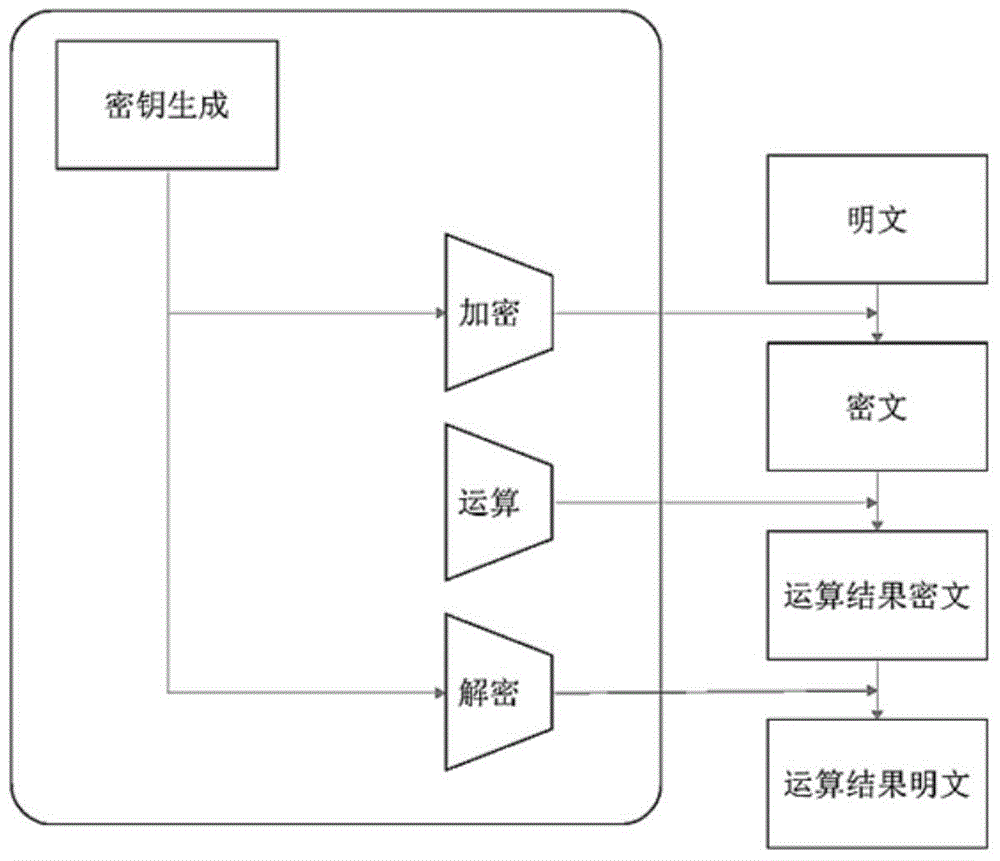
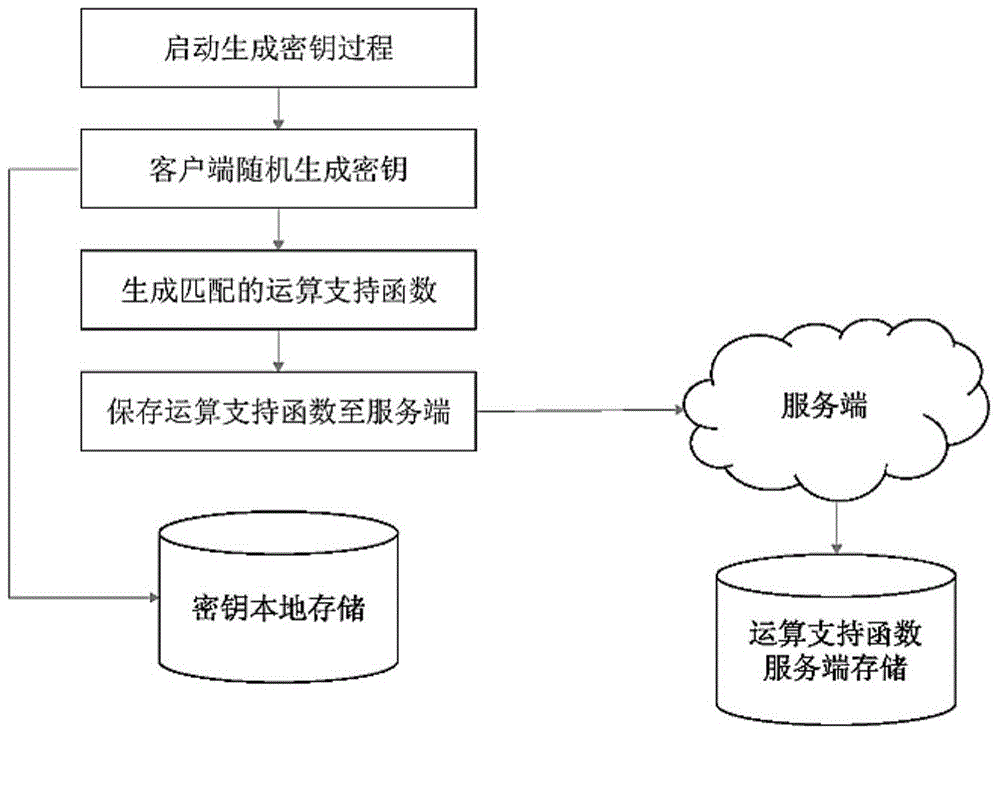
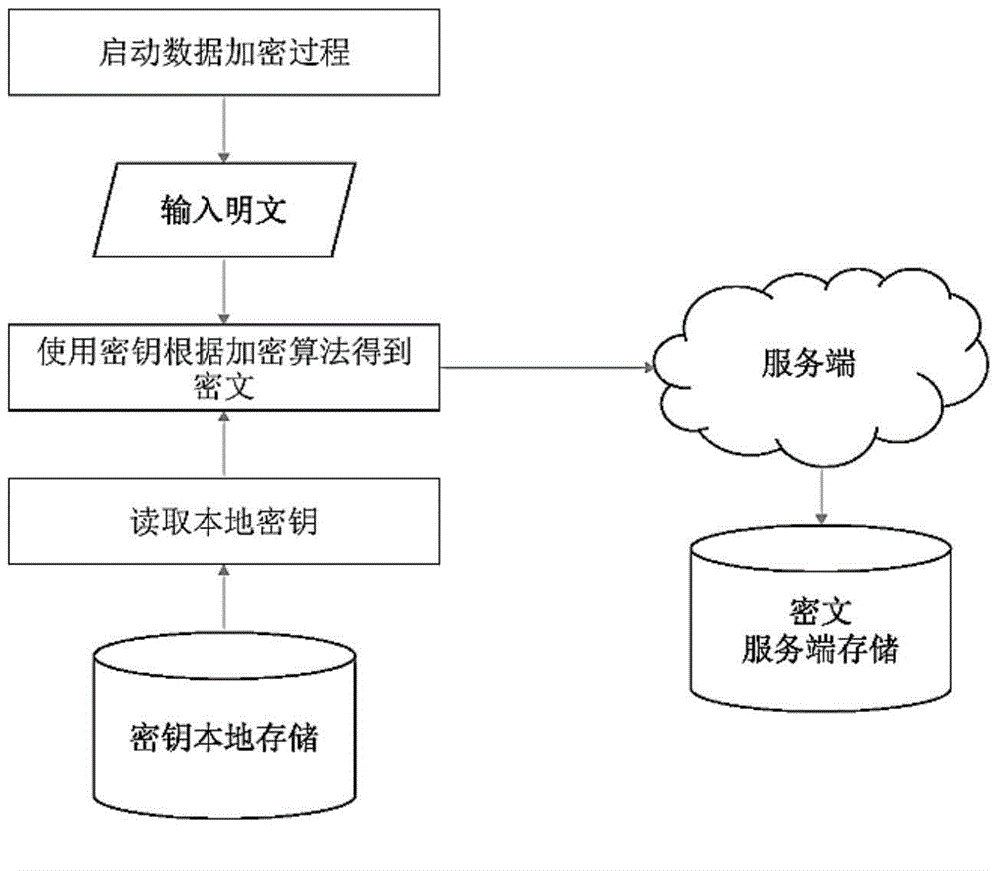
[0036] The present invention can be implemented in various ways corresponding to different demand environments and application scenarios, including: USBKey implementation, API implementation, SDK implementation, chip implementation, expansion card implementation, special equipment implementation, etc. Such as figure 1 and figure 2 As shown, any implementation method includes: client and server. The steps of a typical homomorphic encryption operation process are as follows:
[0037] 1) The client invokes the locally stored key to encrypt sensitive plaintext data and obtain the ciphertext;
[0038] 2) The client sends the ciphertext and calculation requirements to the server, and the key is kept on the client;
[0039] 3) The server calls the corresponding operation support function family, and uses the homomorphic operation function to perform the required operation on the ciphertext uploaded by the client, and then returns the ciphertext of the operation result;
[0040] 4...
Embodiment 2
[0111] The difference between this embodiment and Embodiment 1 lies in that the operation support function G used in it includes:
[0112] Where: α, β∈X, h 1 (α,β), h 2 (α,β) and h 3 (α,β) to satisfy h1 (α,β)≠h 2 (α,β)≠h 3 Any function of (α,β)≠α≠β;
[0113] The corresponding homomorphic operations specifically include:
[0114] i) Addition and subtraction of ciphertext and ciphertext: C r =C 2 ±C 1 , C r ={A r ,X r ,B r},in:
[0115] A r = { a ri | i ∈ I } , a ri = a 2 i · g 1 ( x 2 i , x 1 i ...
Embodiment 3
[0131] In order to improve security, this embodiment introduces the function f when generating the operation support function G 2 , this function does not need to be added to the key, and only affects the calculation and expression of the operation support function G, which can be understood as encrypting the operation support function G.
[0132] The specific expression is as follows: Where: α, β∈X, h 1 (α,β), h 2 (α,β), h 3 (α,β) and h 4 (α,β) to satisfy h 1 (α,β)≠h 2 (α,β)≠h 3 (α,β)≠h 4 Any function of (α,β)≠α≠β; f 2 () is a random generation function used to encrypt the operation support function,
[0133] The corresponding homomorphic operations specifically include:
[0134] i) Addition and subtraction of ciphertext and ciphertext: C r =C 2 ±C 1 , C r ={A r ,X r ,B r}, where: A r ={a ri |i∈I},
[0135] a ri =g 6 ·[a 2i g 1 (x 2i ,x 1i ) g 3 (h 1 (x 2i ,x 1i ), h 2 (x 2i ,x 1i ))±a 1i g 2 (x 2i ,x 1i ) g 4 (h 1 (x 2i ,x 1i ), h 2...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com