Side channel energy analysis method and device for HMAC (Hash-based Message Authentication Code)-SM3 cryptographic algorithm
A cryptographic algorithm and energy analysis technology, applied in the field of data analysis, can solve problems such as low success rate and difficulty in cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
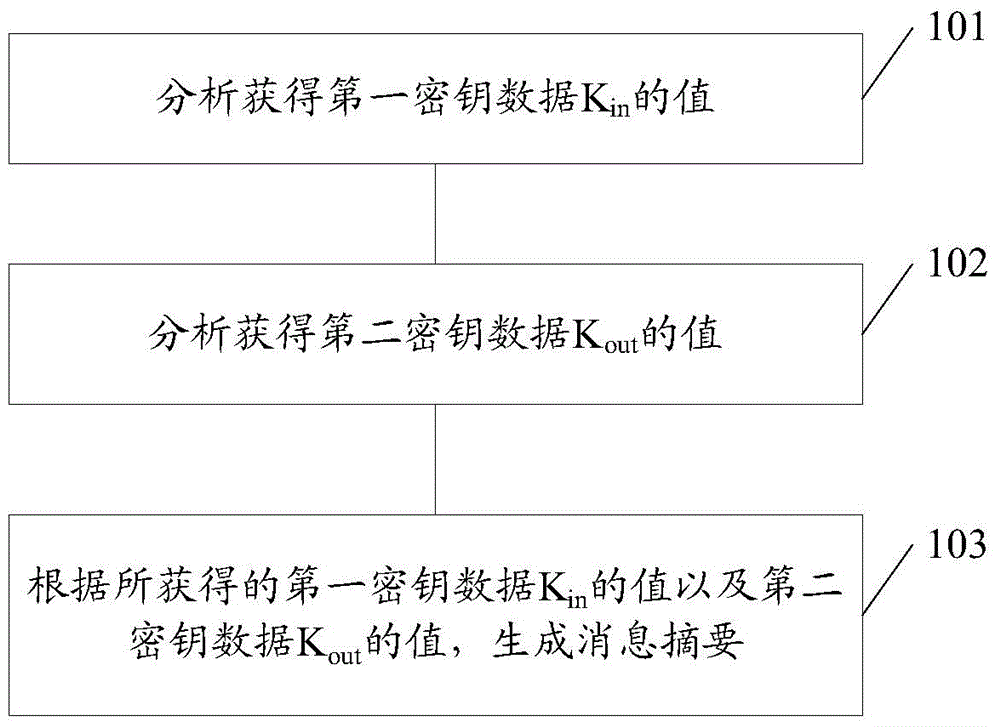
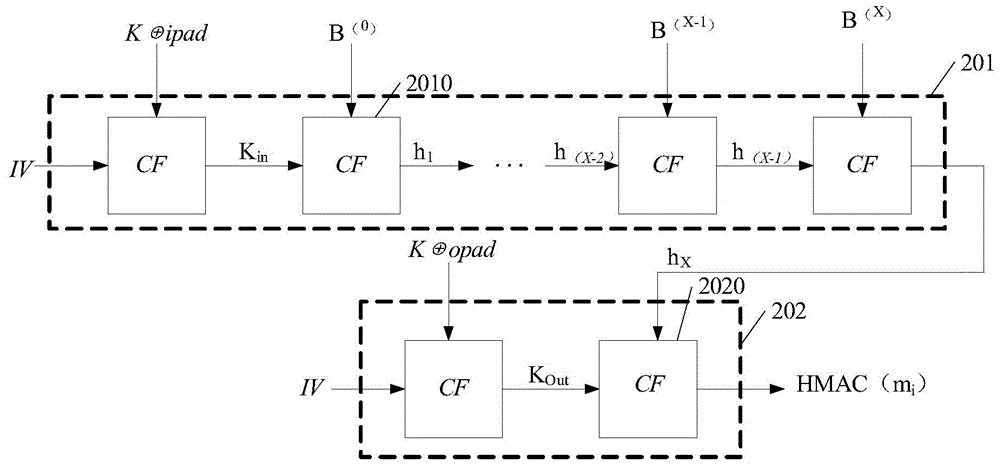
[0078] At present, when obtaining the first key data of the cryptographic module, because there is an energy leak in the bit conversion between the known state value and the unknown state value of a certain register of the cryptographic module, the Hamming distance model can be used to The cryptographic module is analyzed to obtain the first key data of the cryptographic module. However, the above method is more suitable for cryptographic modules implemented in hardware, and it is difficult to crack cryptographic modules implemented in software.
[0079] In view of the above problems, an embodiment of the present invention provides a side channel energy analysis method of the HMAC-SM3 encryption algorithm. The method inputs a message group to a cryptographic module based on the HMAC-SM3 cryptographic algorithm, collects energy consumption information generated by the message group on the one hand, and establishes a corresponding energy consumption matrix; The variable is used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com