SSL strip defense method based on historical information
A technology of historical information and rules, applied in the field of network security, can solve problems such as difficult to unify and affect wide-scale use, and achieve the effect of improving security and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0058] Below in conjunction with accompanying drawing, the specific implementation of the present invention is described in further detail:
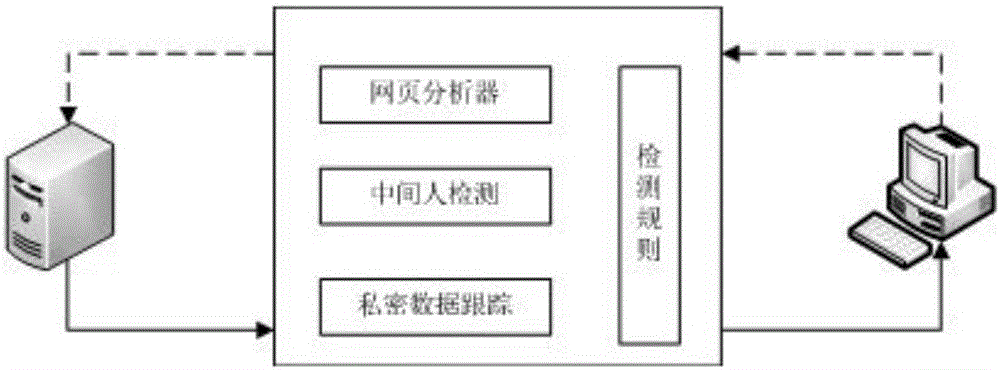
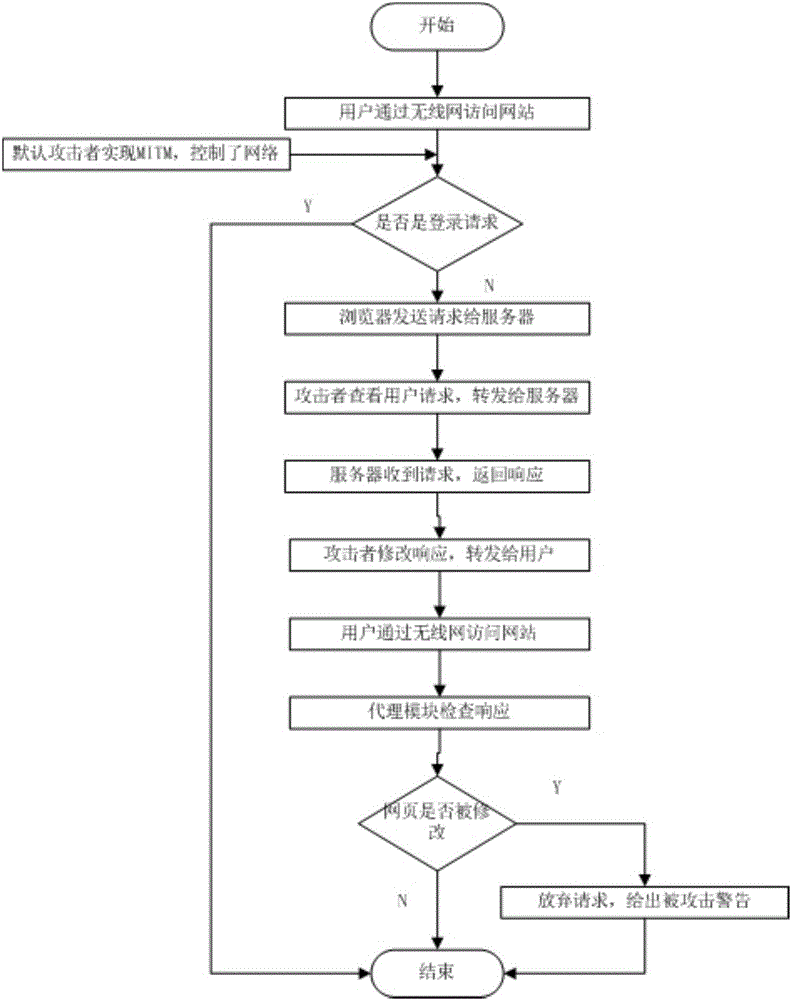
[0059] Step 1: Establish detection rules, which include dangerous modifications to each typical sensitive data structure. Each page from the network will be checked and compared with strict rules before being sent back to the user. The HTTP Moved message detection rule detects whether the conversion of HTTP and HTTPS requests is allowed;
[0060] Establish JS detection rules through the JS preprocessing program to check whether the loaded JavaScript code has been maliciously modified; the Iframe tags rule is used to prohibit additional Iframes from overwriting the original page; the HTTP Forms rule records the form information of the page, and does not allow modification that may leak users information form.
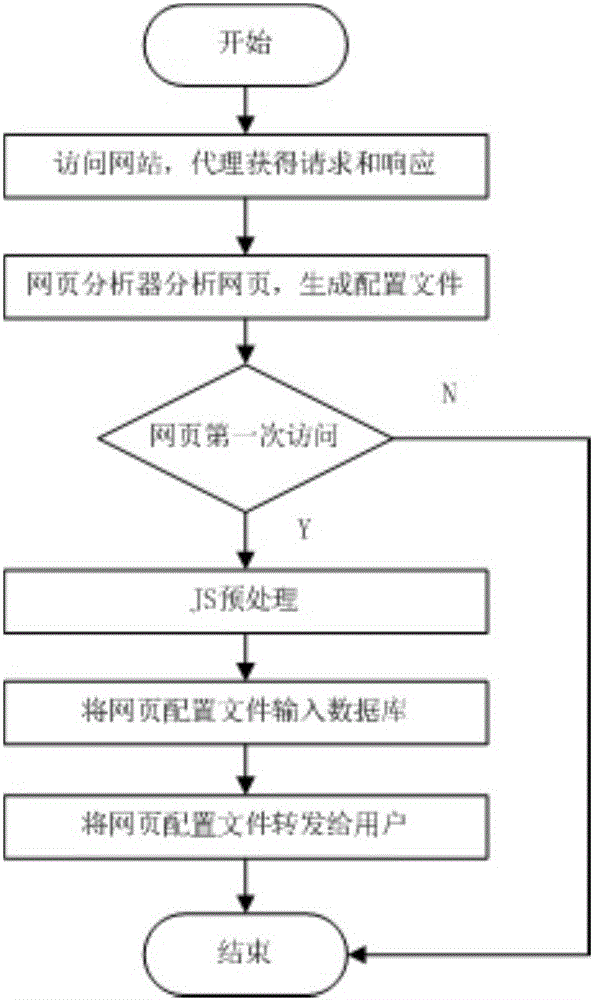
[0061] Step 2: Configuration file generation. Such as figure 2 As shown, the page analyzer identifies key data and their attr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com