Method for generating big data security posture map based on trusted computing
A technology of trusted computing and security posture, applied in the field of network security, can solve problems that are difficult to identify effectively, and achieve the effect of ensuring comprehensiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention is further described in conjunction with the following examples.
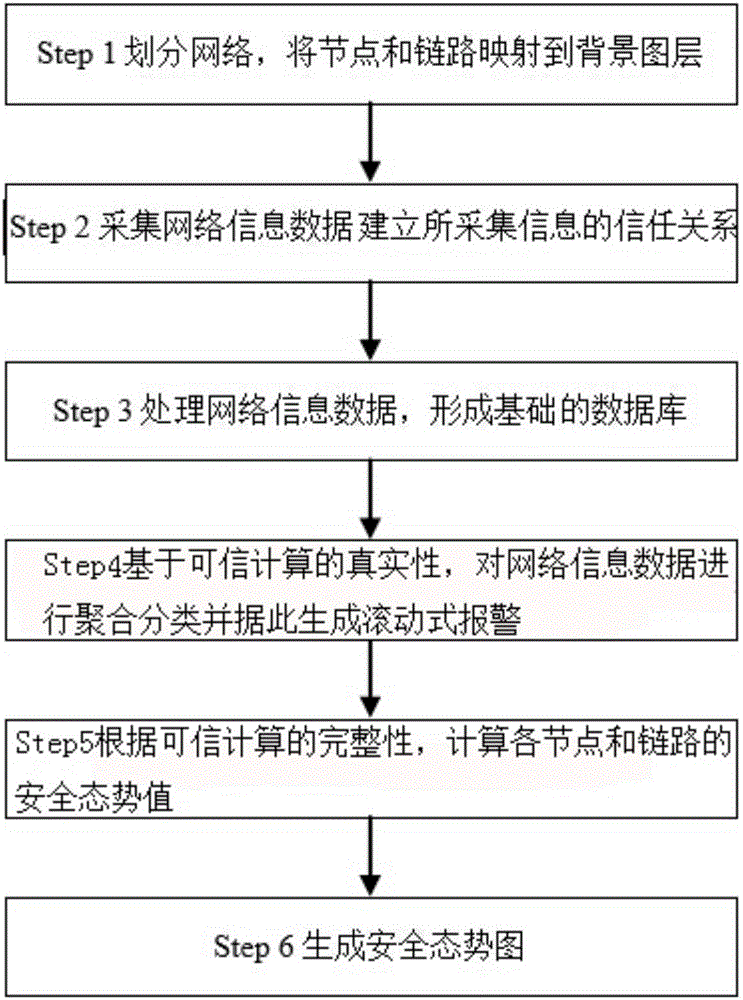
[0044] like figure 1 The shown method for generating a big data security situation map based on trusted computing includes the following steps:
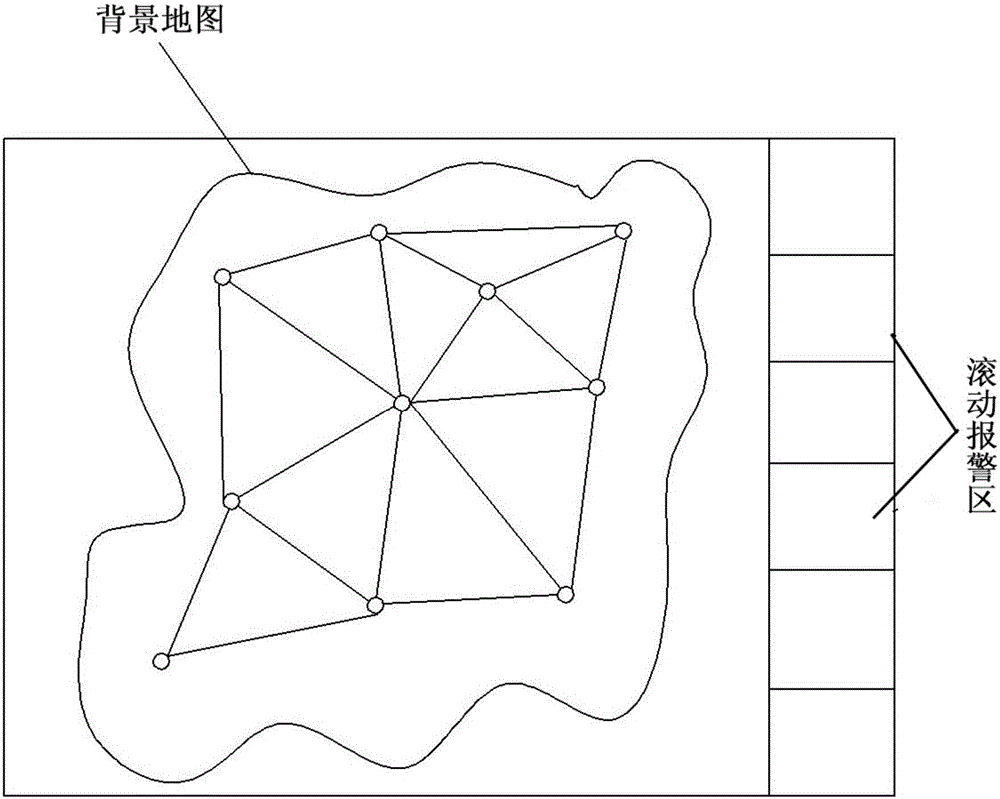
[0045] (1) Utilize MAPX software, use the geographic map where the network is located as a background layer, divide the network into multiple nodes and links connecting two nodes, and map the nodes and links to the background layer;
[0046] (2) collect network information data by a variety of data collectors, authenticate hardware nodes in the network for information collection, judge the credibility of network hardware nodes, and establish trust relationships for collected information. The data collector uses Syslog The collection method is mainly based on Snmp as a supplementary collection method, and the collection of network information data is completed by configuring different network security devices; the network information data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com