Application program control method, device and mobile terminal
A mobile device and program startup technology, applied in the communication field, can solve the problems of privacy leakage, economic loss, and low security, and achieve the effect of improving security performance, reducing economic loss, and increasing vigilance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
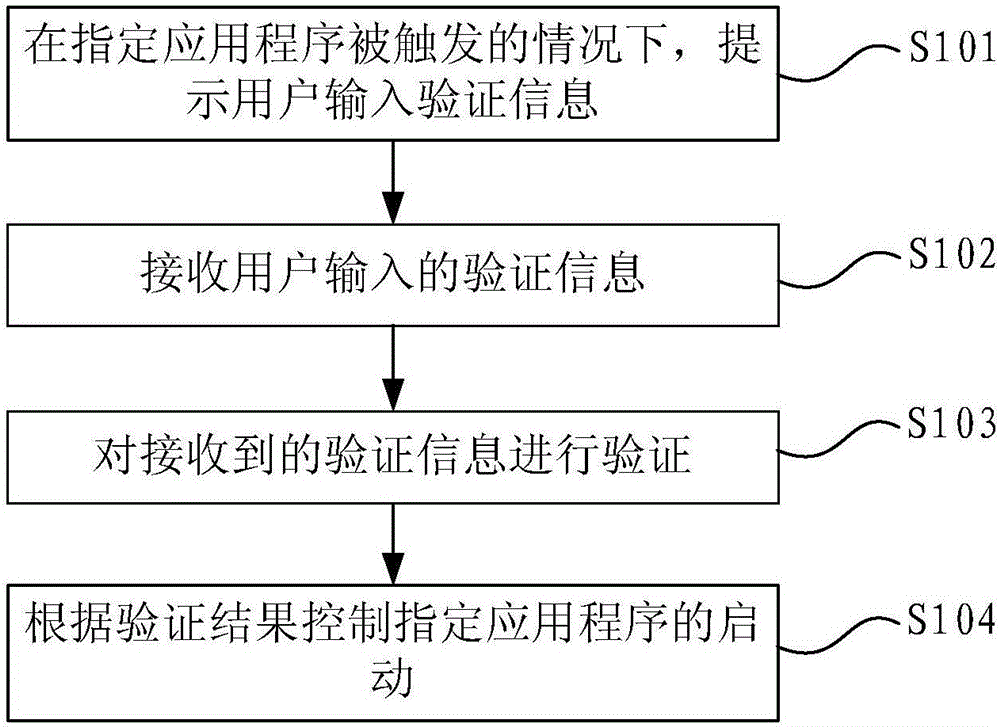
[0050] The application program control method in this embodiment can be applied to mobile devices, such as mobile phones, tablet computers, and the like.
[0051] figure 1 It is a flow chart of the application control method in Embodiment 1 of the present invention. like figure 1 As shown, in this embodiment, the application program control method may include the following steps:
[0052] Step S101, prompting the user to input verification information when the specified application is triggered;
[0053] The designated application program here refers to the application program involving sensitive functions, such as turning on the traffic switch, 4G switch, text message sending and reading permission, contact reading permission, etc.
[0054] In practical applications, the program of the application program control method of the embodiment of the present invention can be implanted in the interface of the application program involving sensitive functions, so that when these s...
Embodiment 2
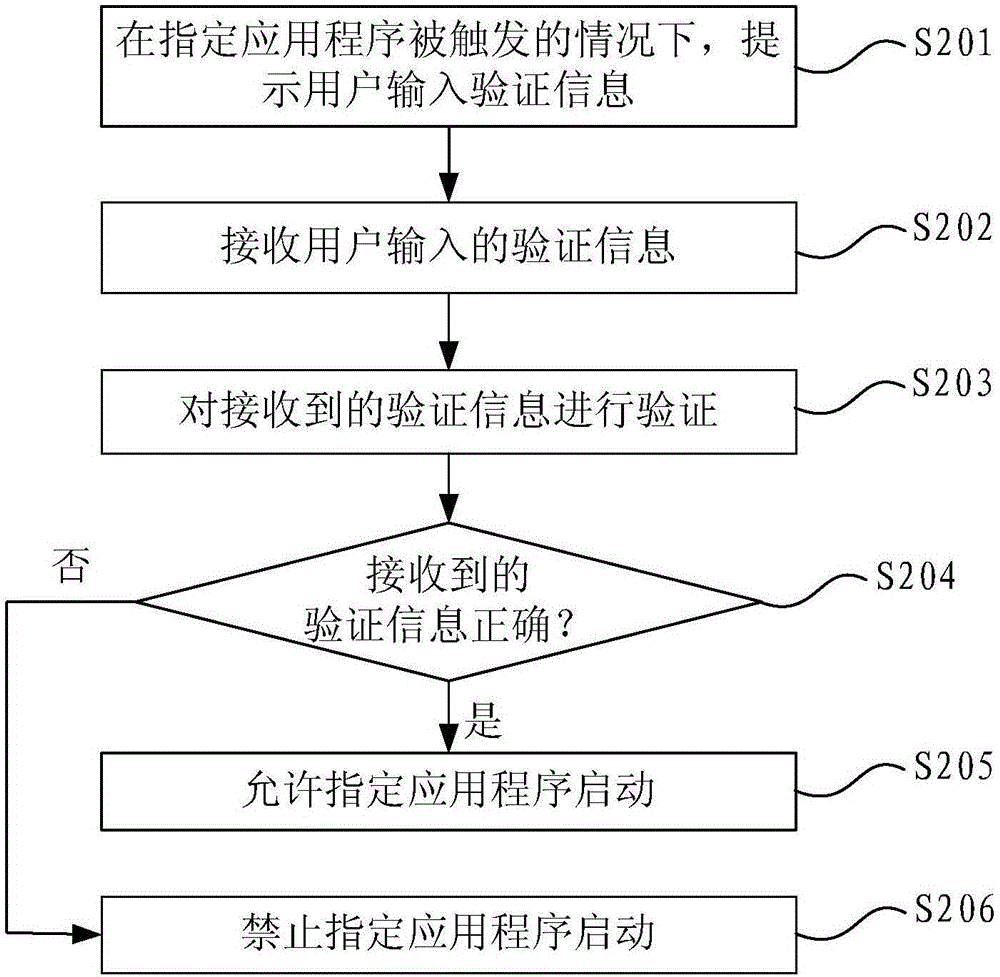
[0067] The application program control method in this embodiment can be applied to mobile devices, such as mobile phones, tablet computers, and the like.
[0068] figure 2 It is a flow chart of the application control method in the second embodiment of the present invention. like figure 2 As shown, in this embodiment, the application program control method may include the following steps:
[0069] Step S201, prompting the user to input verification information when the specified application is triggered;
[0070] Step S202, receiving verification information input by the user;
[0071] Step S203, verifying the received verification information;
[0072] Step S204, judging whether the received verification information is correct, if the verification information is correct, it means that the verification has passed, then execute step S205, if the verification information is wrong, it means that the verification has not passed, and execute step S206;
[0073] Step S205, al...
Embodiment 3
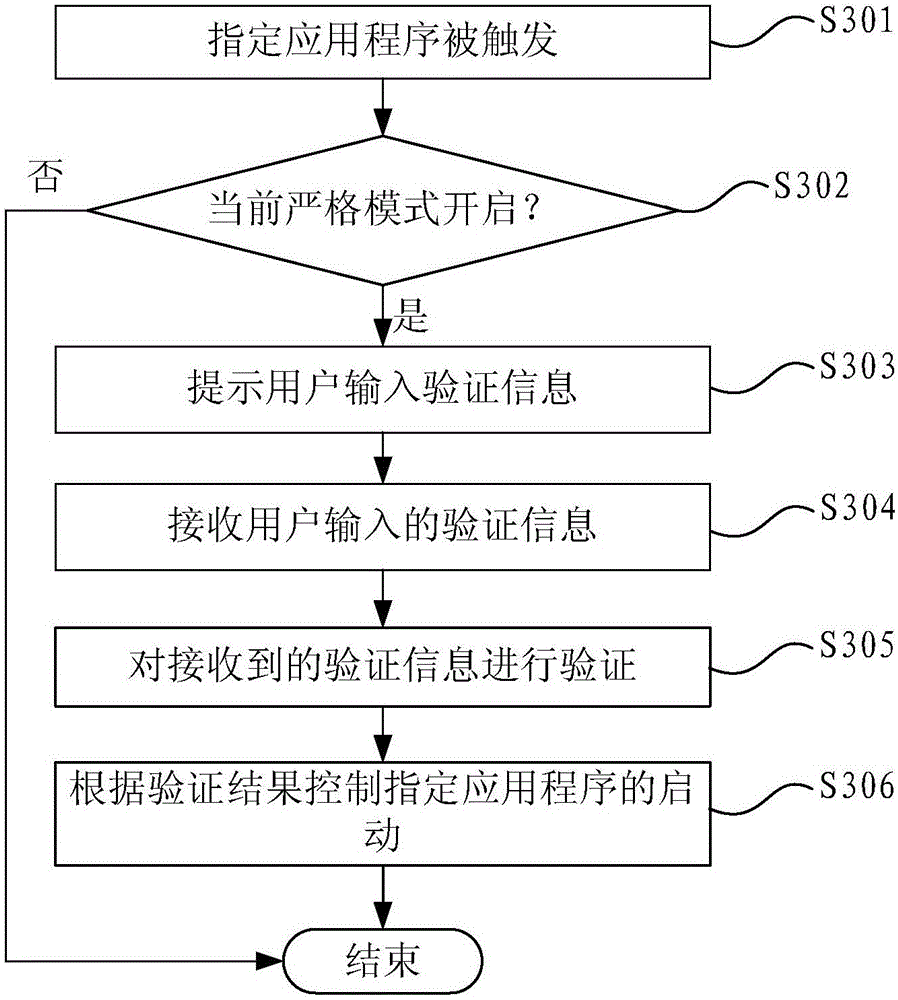
[0079] The application program control method in this embodiment can be applied to mobile devices, such as mobile phones, tablet computers, and the like.
[0080] image 3 It is a flow chart of the application control method in the third embodiment of the present invention. like image 3 As shown, in this embodiment, the application program control method may include the following steps:
[0081] Step S301, the specified application is triggered;
[0082] Step S302, judging whether the current strict mode is enabled, wherein the strict mode refers to a mode in which the startup of the specified application program needs to be verified, if the strict mode is enabled, execute step S303, otherwise end;
[0083] In this article, the mode in which the startup of the specified application needs to be authenticated is referred to as the strict mode.
[0084] In practical applications, you can set the strict mode switch in the mobile device. When the strict mode is enabled, authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com