Uniform identity security authentication method capable of supporting multiple systems
A security authentication and multi-system technology, applied in the field of unified identity security authentication that supports multiple systems, can solve problems such as password theft, management chaos, token forgery, etc., to ensure account system and information security, convenient operation and use, avoid The effect of wasting resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The embodiments of the present invention will be described in detail below. It should be emphasized that the following description is only exemplary, and is not intended to limit the scope of the present invention and its application.
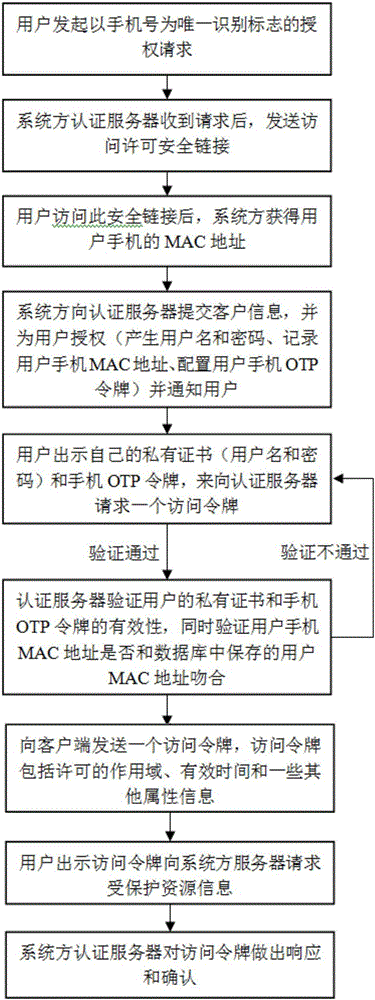
[0041] Refer to figure 1 In an embodiment, a unified identity security authentication method supporting multiple systems includes the following steps:
[0042] S1. The user's mobile phone initiates an authorization request with the mobile phone number as the unique identification mark to the system server;
[0043] S2. The system server sends an access permission security link to the user's mobile phone;
[0044] S3. After the user's mobile phone accesses the access permission security link, the system server obtains the MAC address of the user's mobile phone;
[0045] S4. The system side server submits user information to the authentication server, generates a user name and password, records the MAC address of the user's mobile phone, configure...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com