Anti-piracy encryption method for static library files in embedded system
An embedded system and encryption method technology, which is applied in the direction of program/content distribution protection, instruments, electronic digital data processing, etc., can solve the problems of not being able to guarantee the use of library files within the legal scope, insufficient protection methods, and deciphering, so as to reduce deciphering and the risk of misappropriation, increasing difficulty, and the effect of guaranteeing rights and interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The scheme of this application is further described in conjunction with the accompanying drawings as follows:
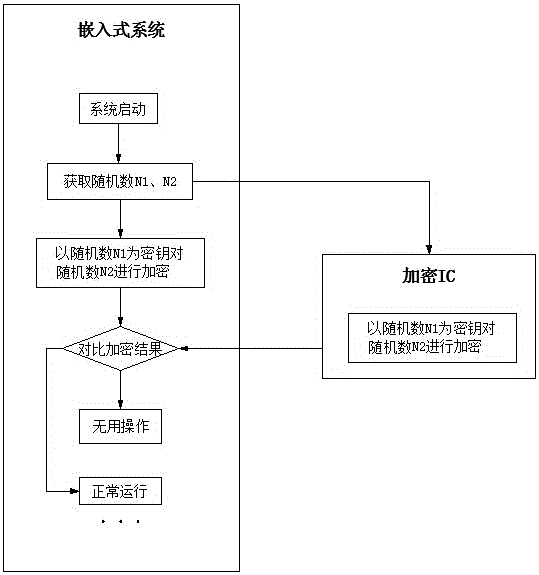
[0027] See attached figure 1 , an anti-piracy encryption method for static library files in an embedded system. The implementation of encryption requires a soft encryption program of the embedded system and a matching encryption IC (integrated circuit integrated circuit), which specifically includes the following steps:
[0028] S01. The embedded system starts and connects to the encryption IC to generate random numbers N1 and N2;
[0029] SO2, the soft encryption program of the embedded system obtains the random numbers N1 and N2, and encrypts another random number with any random number as a key to generate encryption result 1; similarly, the encryption IC obtains the random numbers N1 and N2 N2, perform the same encryption operation to generate encryption result two, and feed back the encryption result two to the embedded system;
[0030] S03. The embedde...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com