An RTL hardware Trojan detection method based on the recursive descent algorithm
A technology of hardware Trojan detection and recursive descent, applied in the field of RTL-level code security analysis, to improve work efficiency and shorten test time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The embodiments listed in the present invention are only used to help understand the present invention, and should not be interpreted as limiting the protection scope of the present invention. For those of ordinary skill in the art, they can also Improvements and modifications are made to the present invention, and these improvements and modifications also fall within the protection scope of the claims of the present invention.
[0020] The present invention will be further described below in conjunction with accompanying drawing.
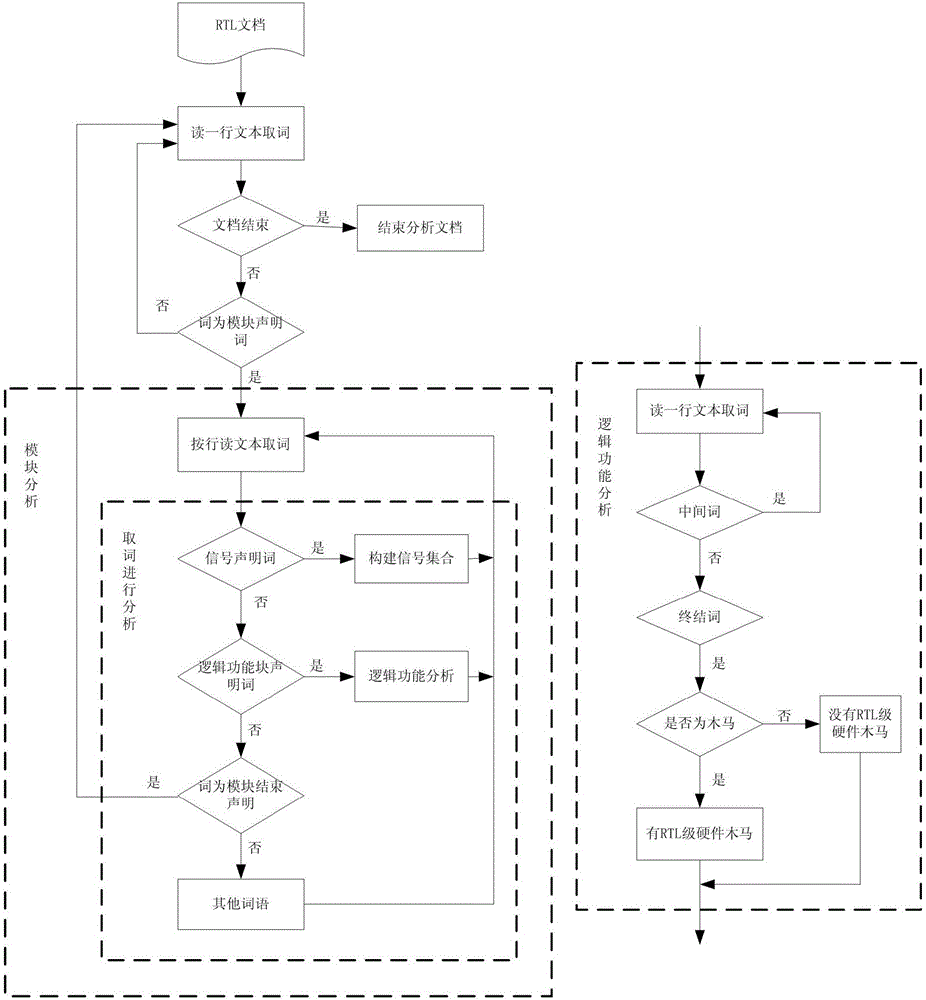
[0021] The invention provides a RTL level hardware Trojan detection method based on a recursive descent algorithm. According to the Trojan model, RTL code rules are designed, and word types are specified, including module declaration words, module end declaration words, signal declaration words, logic function block declaration words, The middle word and the terminator are used to analyze the RTL file and find out the Trojan horse modules th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com