Malicious domain name determination method based on frequency characteristics
A judgment method and domain name technology, applied in the field of network information security, to achieve the effect of enhancing adaptability, reducing accidental and false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments.
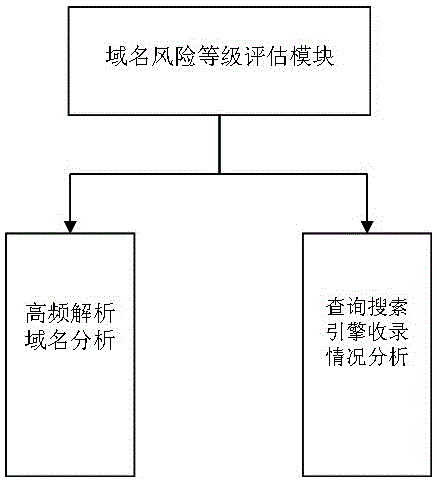
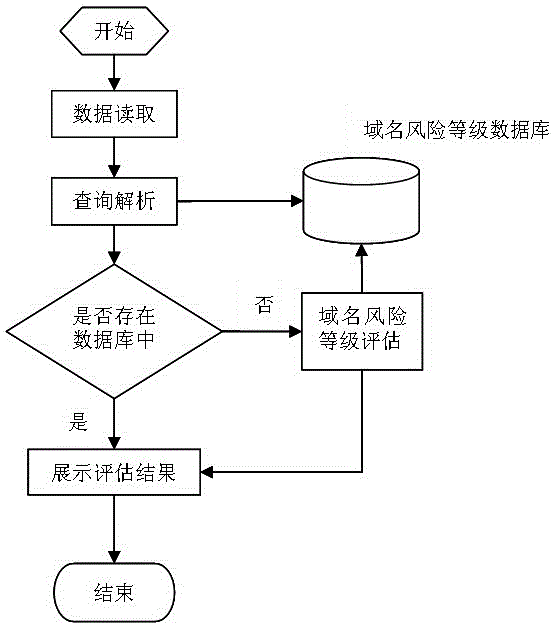
[0017] In the domain name risk level evaluation system of the malicious domain name determination method of the present invention, we comprehensively evaluate the risk level of the domain name from two aspects respectively, and its structure is as follows figure 1 shown.
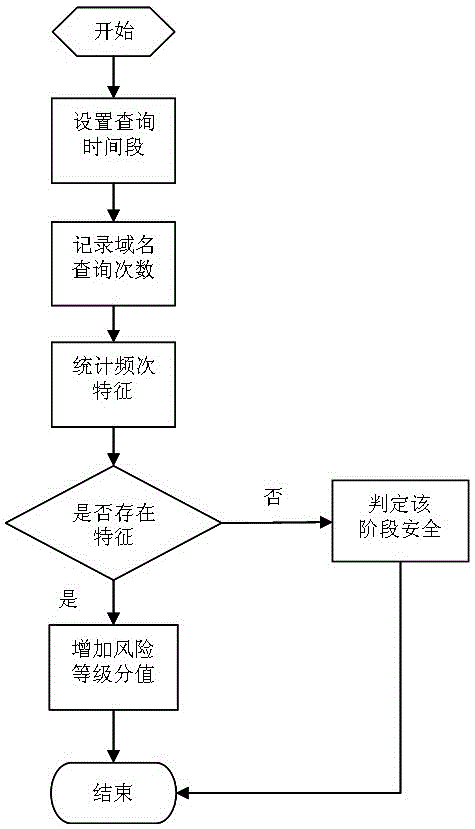
[0018] The first stage, high-frequency analysis and domain name analysis. Divide the time period and periodically count the top 10 commonly used domain names of each host. According to statistical laws and the rules of each host’s Internet access, periodically count the top 10 commonly used domain names of each host. Generally, the list of Top 10 will basically not change. The Internet access is stable. If the list of Top 10 has changed greatly, it is considered that the "behavior" of the host during this period is abnormal compared with usual, which is likely to be attack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com