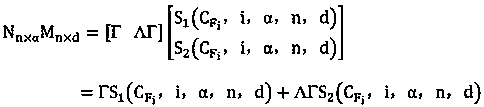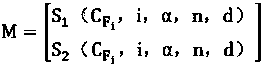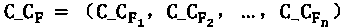Secondary encryption-based data validation and data recovery algorithm in cloud storage
A secondary encryption and data verification technology, applied in digital data protection, electronic digital data processing, computing, etc., can solve the problems of inability to completely avoid data tampering loss, increase space occupation, and large system overhead, and achieve simple and accurate recovery , reduce overhead, and take up less storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] Step 1: Data is encrypted for the first time
[0018] Before the data is uploaded to the cloud space, for the safety of the data, the data will be encrypted before uploading. There are many confidential algorithms. In the present invention, asymmetric encryption is adopted:
[0019] Data F, divide it into blocks, expressed as: F=(F 1 , F 2 ,...,F n ), use the RSA algorithm to encrypt the data block once, and the encrypted public key is key pk , the private key is key sk , the encrypted ciphertext data:
[0020]
[0021] Step 2: Ciphertext data is encrypted again
[0022] The secondary encryption of data is to integrate the data verification process into the encryption process. The process is as follows:
[0023] (1) Hash the original data F to get the hash value h of the file F (or called digital signature), in order to facilitate calculation in this method, the length of the hash value is set to 8 bits.
[0024] (2) For ciphertext data block Also perform a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com