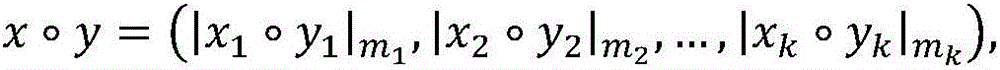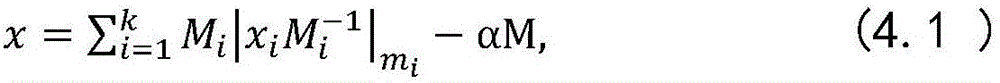Method for implementing SM2 white-box digital signature based on residue number system
A residual system and digital signature technology, applied in the field of information security, can solve the problems of high use cost, inability to deal with white-box attack methods, poor versatility, etc., and achieve the effect of high practicability, expanding the scope of use, and reducing the cost of use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
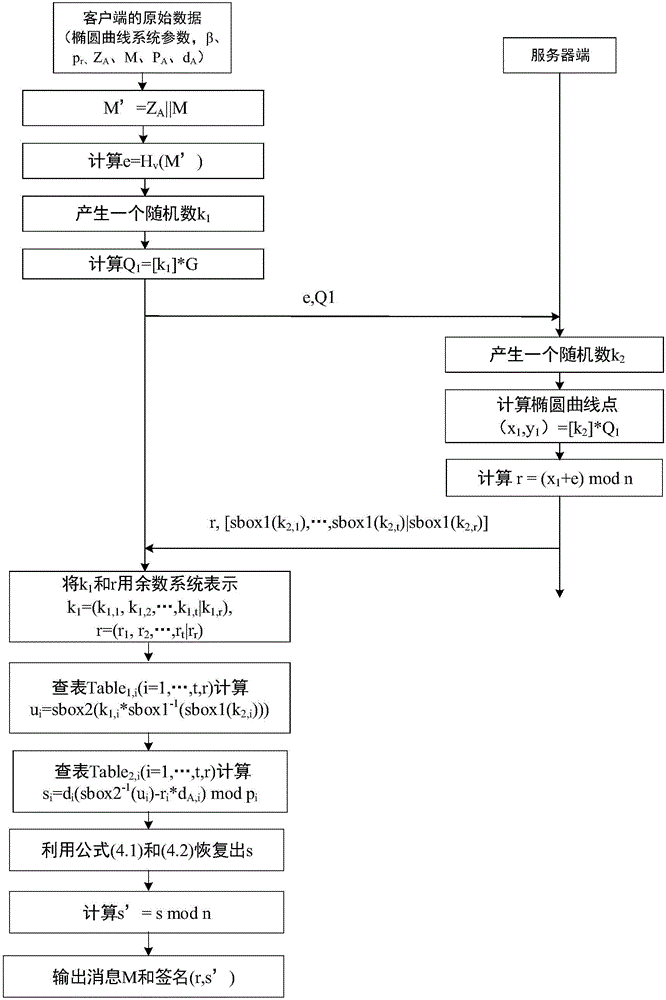
[0031] The design idea of the present invention is to conduct research on the problem that the key operation is not safe in an untrusted environment, and malicious attackers can obtain the system key through white-box attack means, and realize the splitting of large numbers by using the remainder system, thereby reducing The size of the key table; by using scrambling and obfuscation to ensure that the intermediate results are invisible to the attacker; by using the random factor in the cloud to ensure the unknownness of the terminal key calculation relationship, the security of the signature private key during the terminal signature calculation process is realized, and at the same time It can be verified using the standard SM2 signature verification algorithm.
[0032] The present invention is constructed based on the national commercial cryptographic algorithm SM2 digital signature algorithm. Please refer to the management standard issued by the National Commercial Cryptogra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com