SMV (sampled measured value) network attack grading detection method applicable to digital substation bay level
A technology of network attack and detection method, which is applied in the field of power system information security, and can solve problems such as security accidents, false data injection attacks, and refusal to operate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
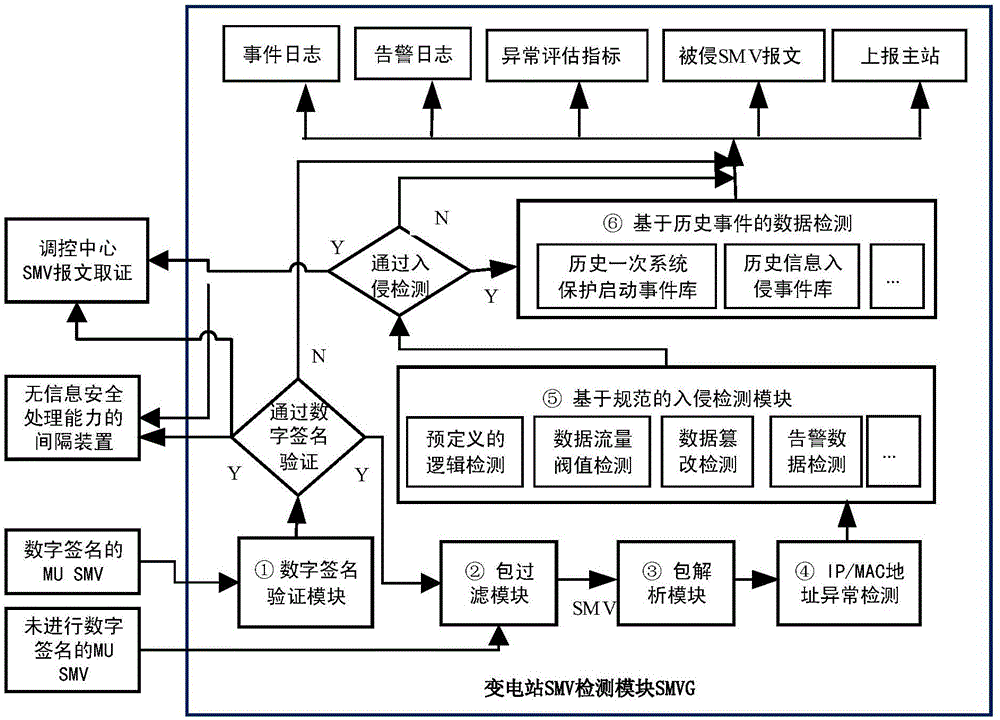
[0021] Such as figure 1 As shown, a method for grading detection of SMV network attacks applicable to digital substation bay layer includes the following steps:
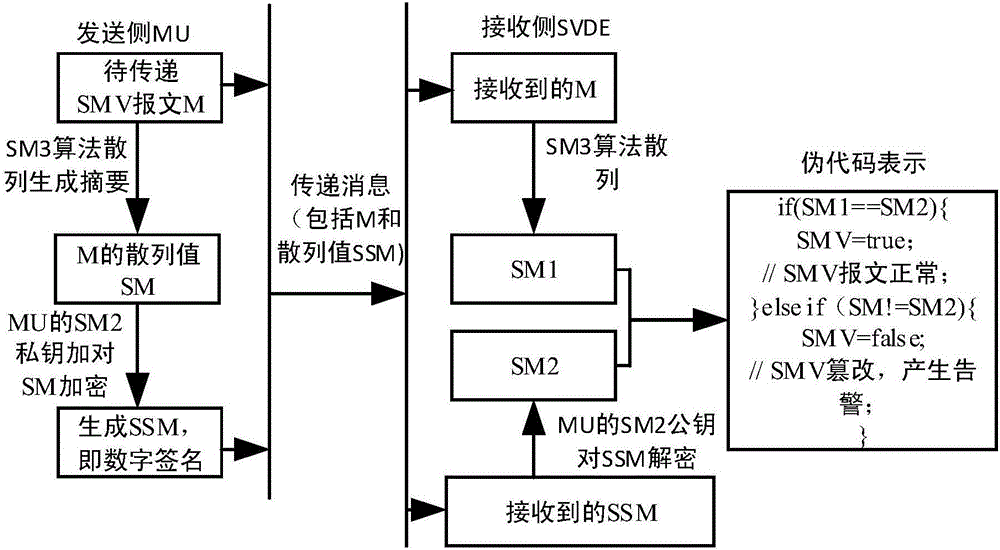
[0022] Step 1. Packet decryption: Perform digital signature verification on the digitally signed SMV packet of MU, and process the data packet according to the encryption and decryption rules;
[0023] Step 2. Packet filtering: Since GOOSE / SMV has high requirements on real-time performance, GOOSE / SMV message transmission is directly from the application layer to the data link layer, without using UDP / TCP / IP protocol, so it needs to be started according to the SMV data packet MVC Different addresses, filter out SMV packets;
[0024] Step 3. Packet analysis: peel off the MAC address protocol on the outer layer of the SMV data packet, extract the data in the packet, and send the MAC address and packet data to the packet anomaly detection module.
[0025] Step 4. MAC address anomaly detection: All MAC addresses arrivin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com