Full-duplex opportunistic relaying protocol self-adaptation switching security transmission scheme
A technology of adaptive switching and secure transmission, which is applied in the field of protocol adaptive switching secure transmission schemes, can solve problems such as danger, and achieve the effect of improving the evaluation security rate and performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
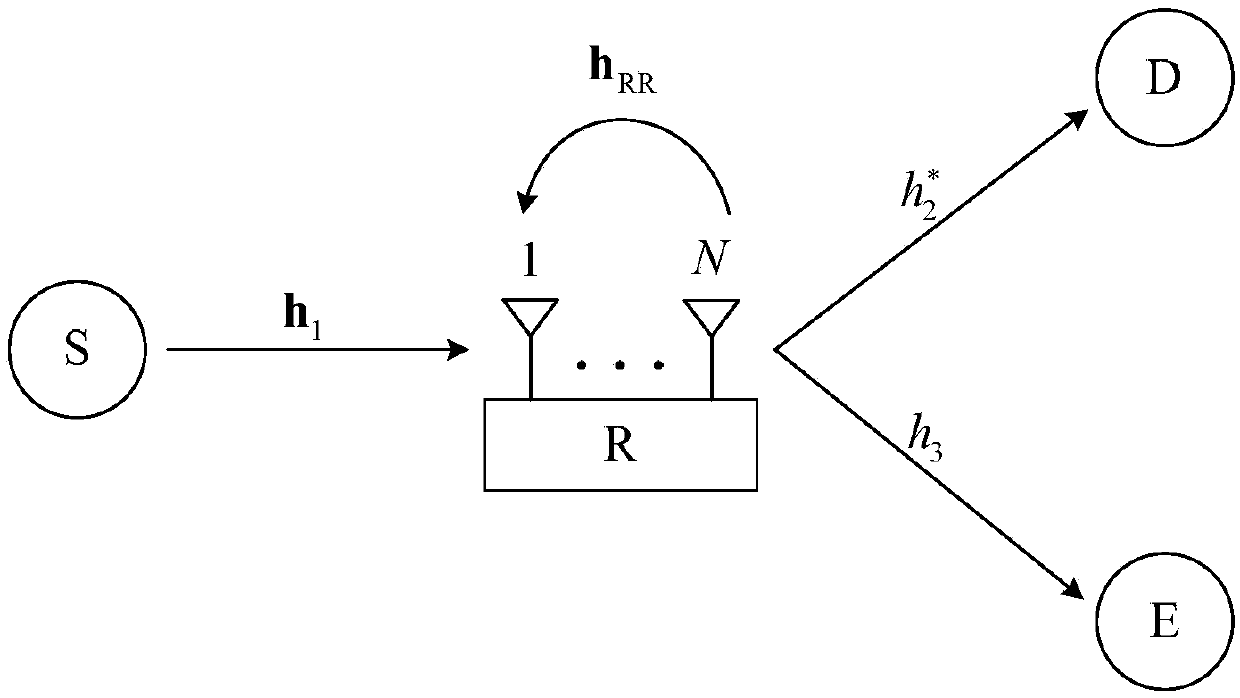
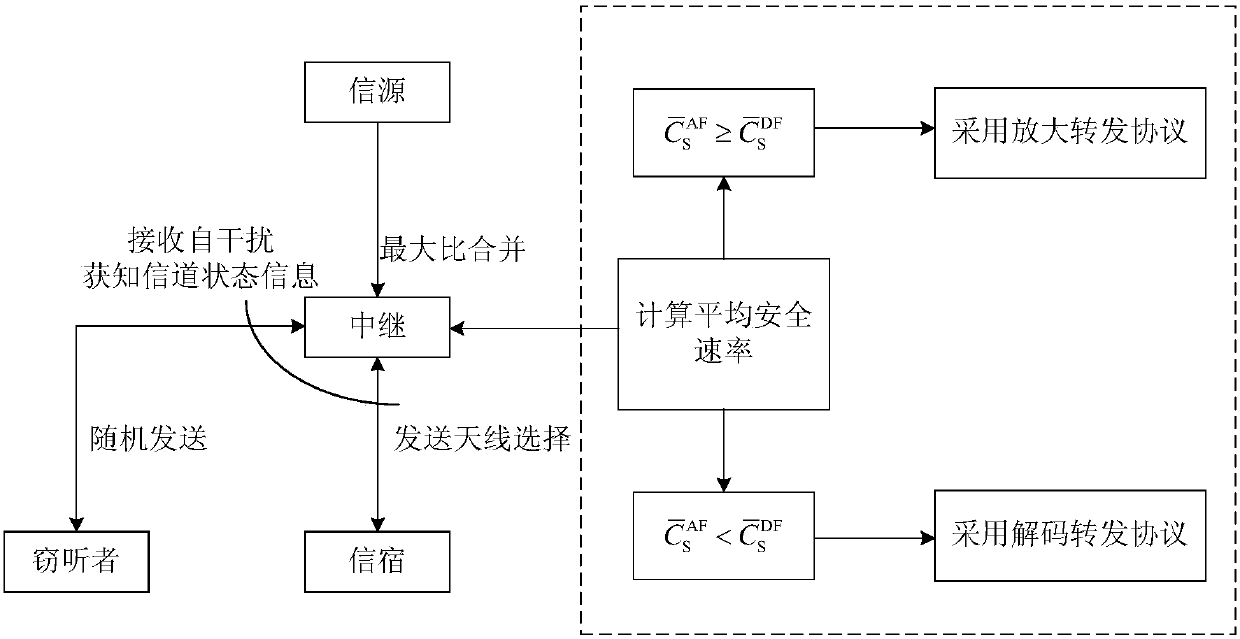
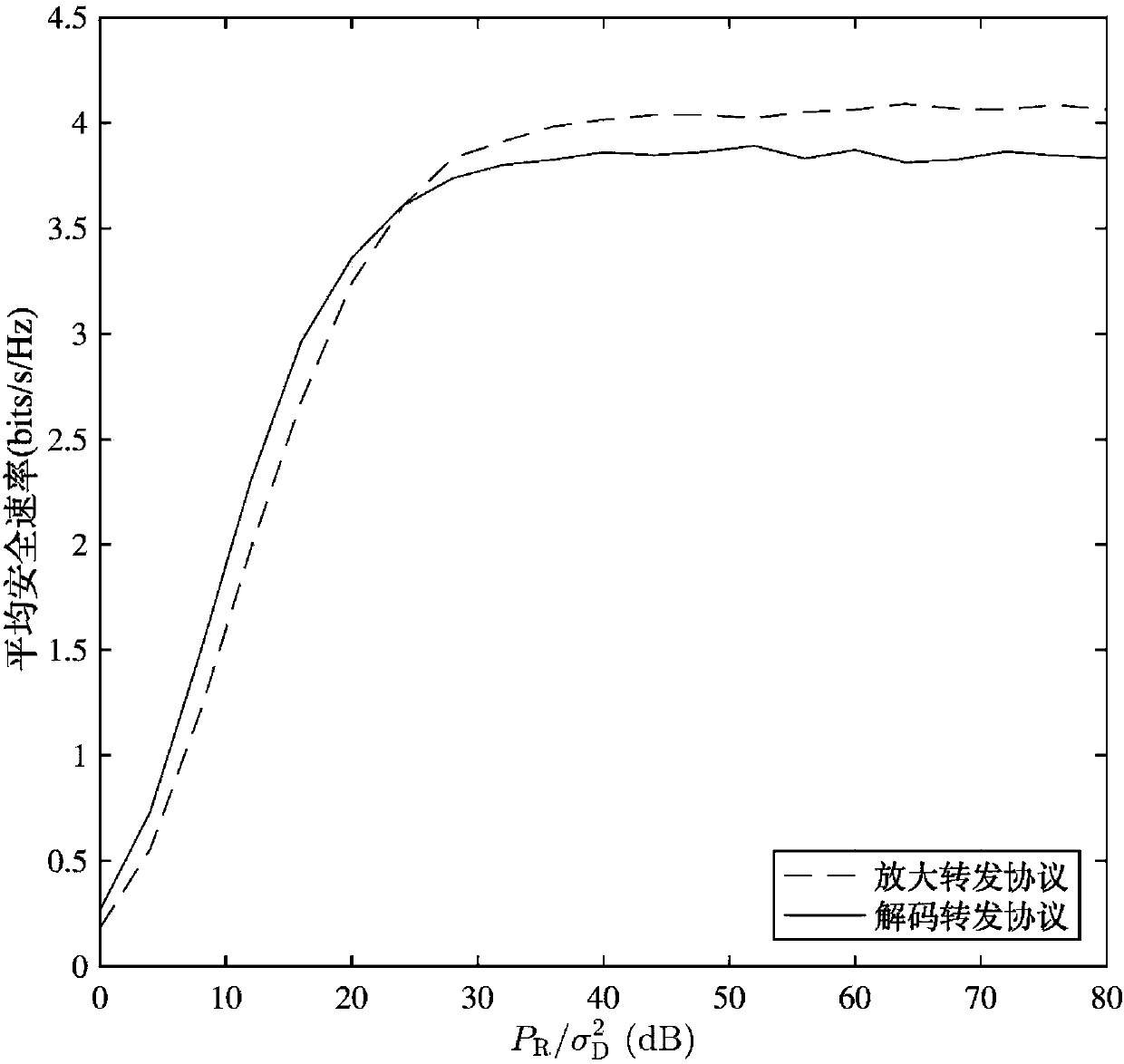
[0038] A full-duplex opportunistic relay protocol adaptive switching security transmission scheme disclosed by the present invention, such as figure 1 As shown, the scheme is applied in a system including four nodes of source (S), relay (R), sink (D) and eavesdropper (E), and the transmission of system information is completed in one time slot, in which The relay is configured with N antennas and the rest of the nodes are configured with a single antenna. The channel vector from the relay to the sink is denoted as Such as figure 2 As shown, the scheme includes the following steps:
[0039] Step 1, the relay sends pilot information to the sink, and the sink estimates the channel information h from the relay to the sink 2 Finally, the channel information is fed back to the relay, and the relay divides the N antennas into two groups according to the channel information, and one group is an optimal transmitting antenna, which can maximize the channel gain from the relay to the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com