Obfuscating method and device for virtual machine command, and virtual machine protection system
A virtual machine and instruction technology, applied in the direction of program/content distribution protection, etc., can solve problems such as easy to be decompiled, O-llvm code confusion, etc., to achieve the effect of solving the problem of being easy to be decompiled and increasing the difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
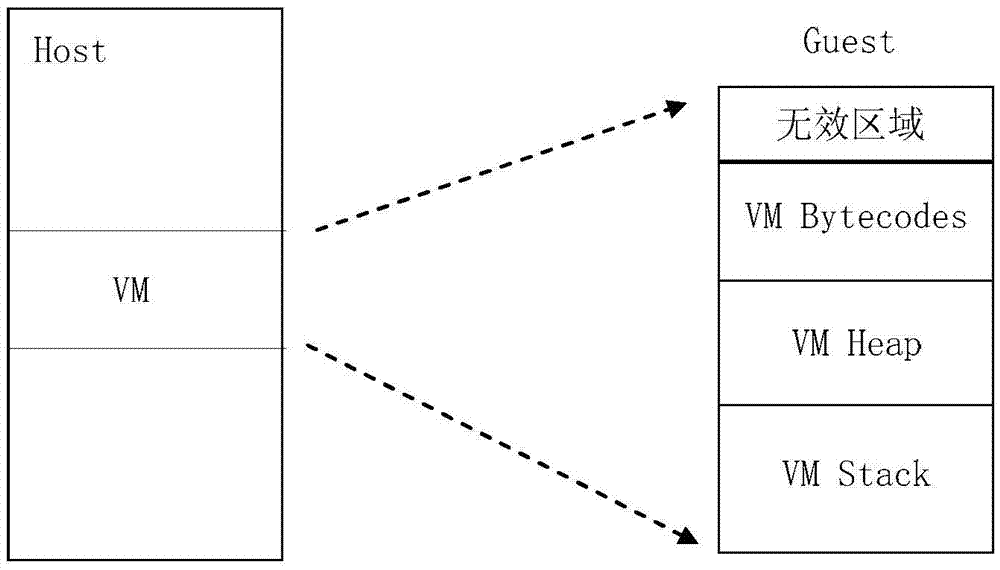
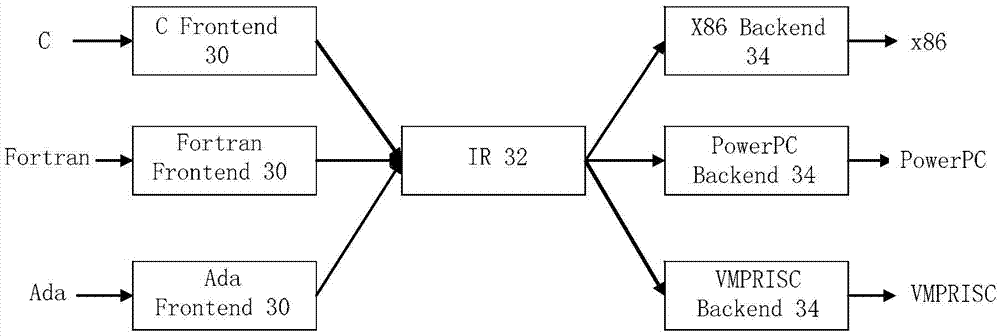
[0034] According to the embodiment of the present application, an embodiment of a method for obfuscating virtual machine instructions is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be implemented in a virtual machine protection system such as a set of computer-executable instructions. and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
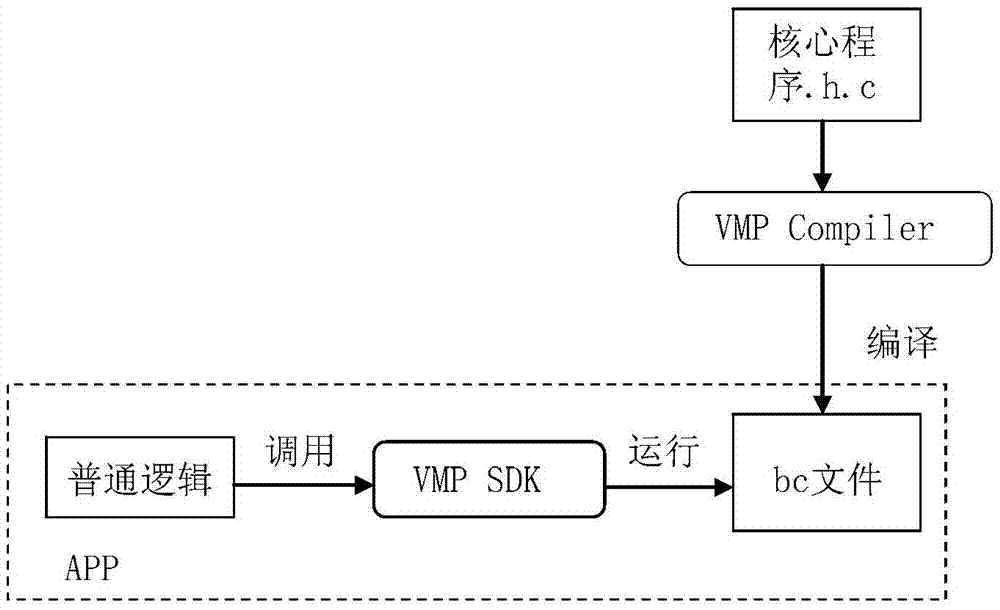
[0035] Such as figure 1 Shown: The virtual machine protection system roughly divides into two processes when verifying instructions:
[0036] (1) Bytecode generation process, corresponding to the module VMP compiler (Compiler)
[0037] The protected code (that is, the program code of the program to be compiled) is provided in the form of C language source code, and the virtual machine bytecode is finally generated through AVMPCompiler. It should be noted tha...
Embodiment 2
[0082] The method shown in Embodiment 1 can be executed in a mobile terminal, a computer terminal or a similar computing device. Take running on a computer terminal as an example, Figure 6 It is a block diagram of the hardware structure of a computer terminal for realizing the obfuscation method of virtual machine instructions according to the embodiment of the present application. Such as Figure 6 As shown, the computer terminal 60 may include one or more (only one is shown in the figure) processors 602 (the processors 602 may include but not limited to processing devices such as microprocessor MCU or programmable logic device FPGA, etc.), for A memory 604 for storing data, and a transmission device 606 for communication functions. Those of ordinary skill in the art can understand that, Figure 6 The shown structure is only for illustration, and it does not limit the structure of the above-mentioned electronic device. For example, computer terminal 60 may also include ...
Embodiment 3
[0093] The embodiment of the present application also provides a device for obfuscating virtual machine instructions. Figure 7 is a structural block diagram of an optional obfuscation device for virtual machine instructions according to an embodiment of the present application, such as Figure 7 As shown, the device includes:
[0094] The obfuscation module 70 is used to perform code obfuscation processing on the target output instruction corresponding to the program to be compiled to obtain the target instruction, wherein the above-mentioned target output instruction is an instruction corresponding to the above-mentioned program to be compiled outputted by the compiler backend;
[0095] The output module 72 is connected to the obfuscation module 70, and is configured to use the target instruction as a final output instruction of the compiler and output the final output instruction.
[0096] Optionally, the obfuscation module 70 is also used to convert the source code of the...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap