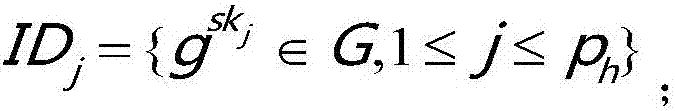Efficient pseudonym management and data integrity protection protocol
A technology of data integrity and pseudonymity, which is applied in digital transmission systems, encryption devices with shift registers/memory, security devices, etc., to provide location privacy protection, balance false recognition rates, and reduce communication time and computing costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be further explained below in conjunction with the accompanying drawings and specific embodiments.
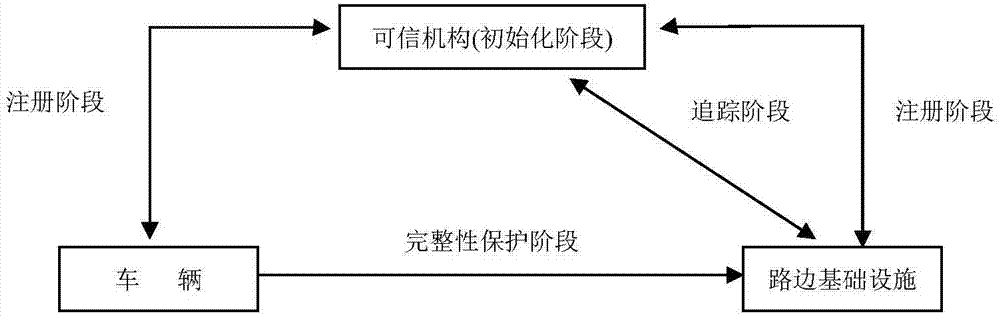
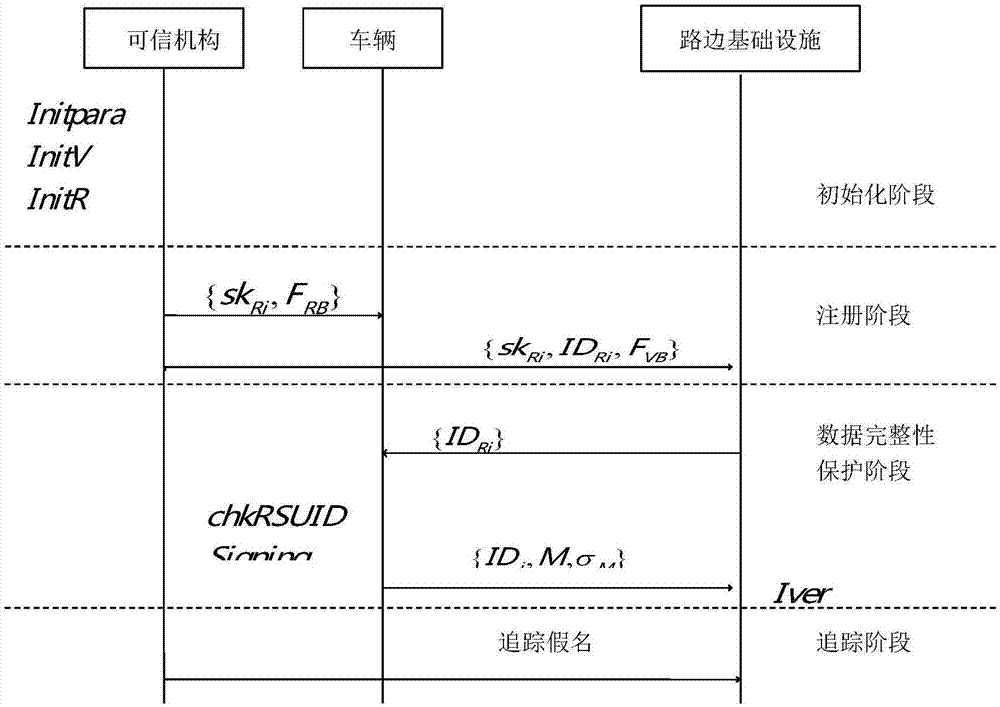
[0048] Such as figure 1 As shown, the present invention involves three entities, the content of the communication between these entities, and the four phases contained in the protocol. The three entities defined in the present invention are: Trusted Authority (TA), Vehicle (Vhicle) and Roadside Infrastructure (RSU). The trusted authority generates keying material and communicates the corresponding keying material to the vehicle and the roadside infrastructure, respectively. After the vehicle obtains the key and public parameters distributed by the trusted organization, it needs to use the signature algorithm to generate a signature for the message to be sent and send it to the roadside infrastructure. After the roadside infrastructure receives the message, it needs to use the signature algorithm to verify the message. Finally, the trusted or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com