Safety protection method for the whole life cycle of engineering documents
A technology of full lifecycle and engineering documents, which is applied in the field of security protection of the whole lifecycle of engineering documents, can solve problems such as weak threats, and achieve the effect of improving self-security and increasing privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
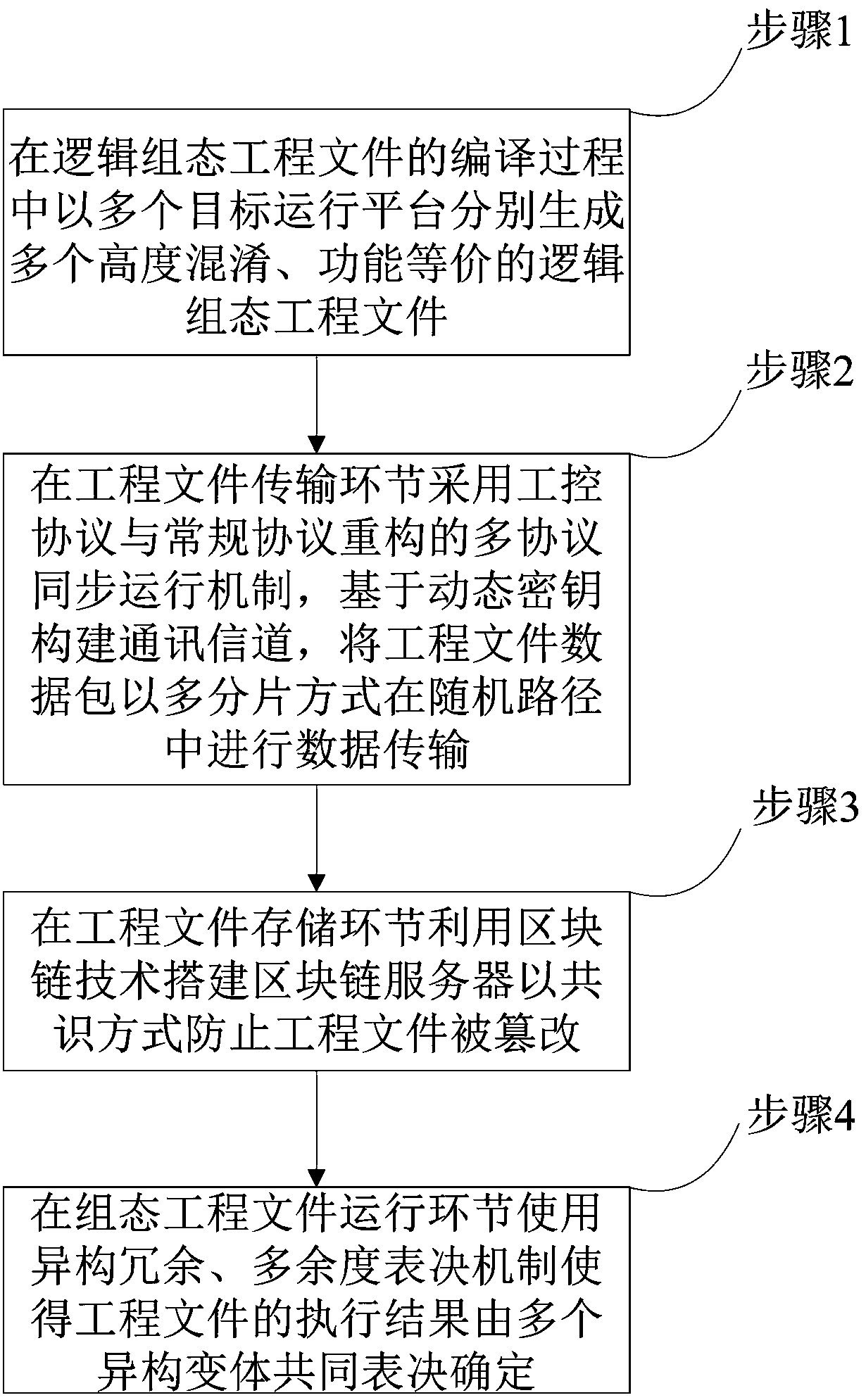
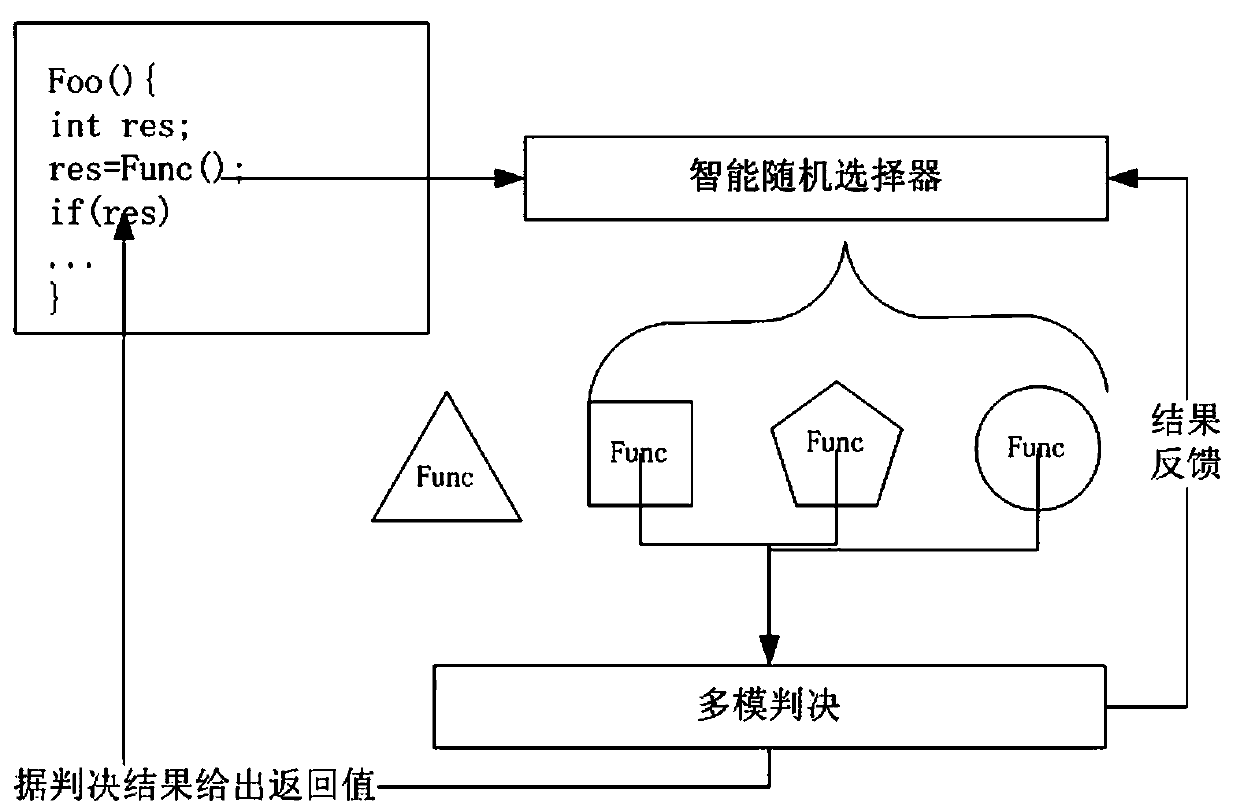
[0026] Embodiment one, such as figure 1 As shown, the project file full lifecycle security protection method of the present invention includes four stages: project file compilation link, project file transmission link, project file storage link and project file operation link. In each link, based on heterogeneous redundancy, Redundancy voting mechanism, combined with the specific process to increase the corresponding security protection technology to form an information security protection plan, specifically includes the following steps:
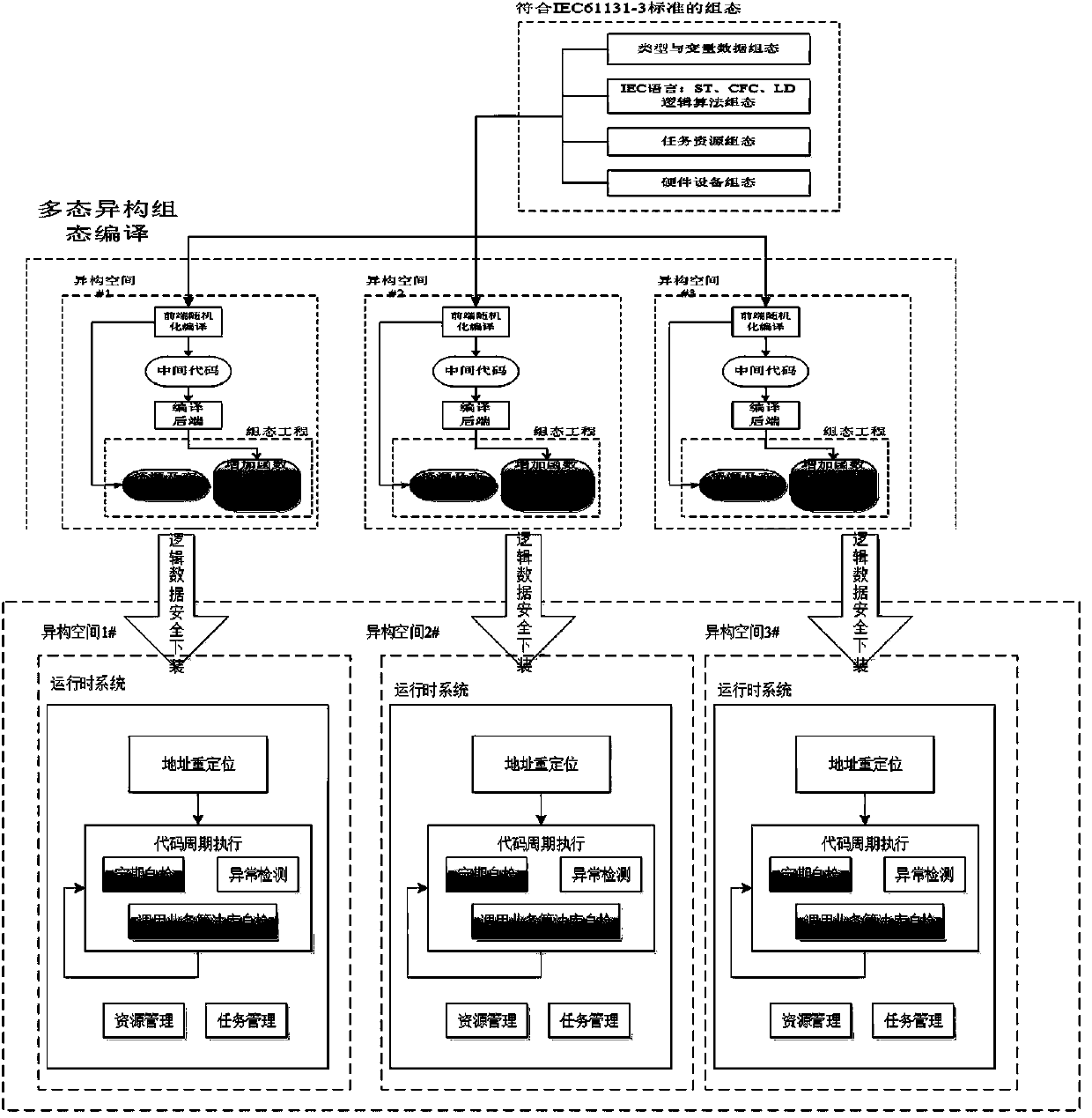
[0027] Step 1, such as figure 2 As shown, the intermediate code of the cross-platform environment is generated based on the basic environment of the heterogeneous multi-mode lower computer software and hardware; in the process of compiling the logic configuration project file, multiple target operating platforms are used to generate multiple highly confusing and functionally equivalent Logical configuration project files;
[0028] Interme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com