Distributed heterogeneous network vulnerability mining method based on Fuzzing algorithm
A vulnerability mining and heterogeneous network technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as unfavorable analysis, insufficient protocol coverage efficiency, artificial interference, etc., to improve coverage and effectiveness, comprehensive protocol operation path, The effect of lowering barriers to entry
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] The present invention will be described in further detail below in conjunction with the accompanying drawings.
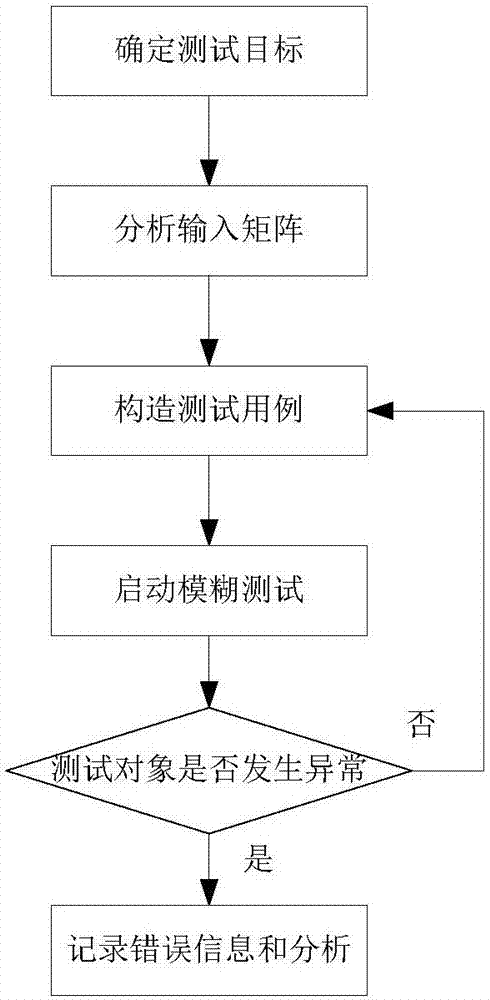
[0061] Such as image 3 As shown, the distributed heterogeneous network vulnerability mining method based on Fuzzing algorithm described in the present invention comprises the following steps:
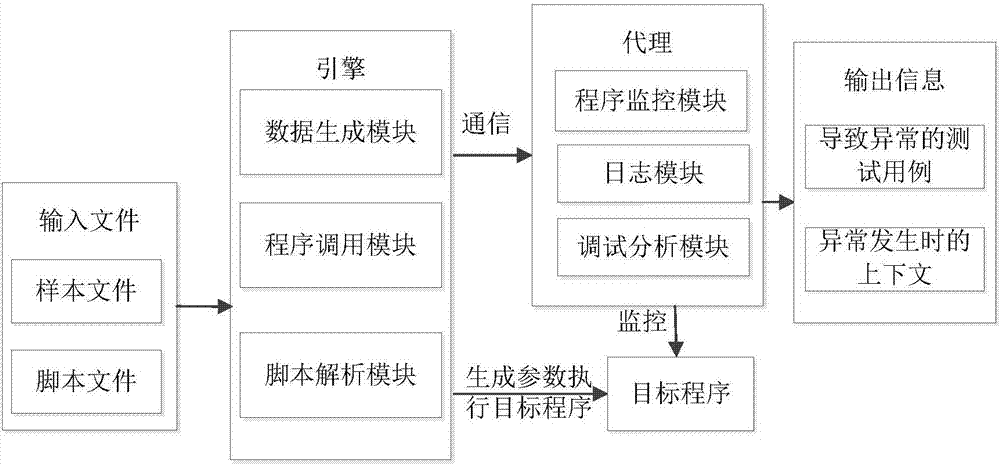
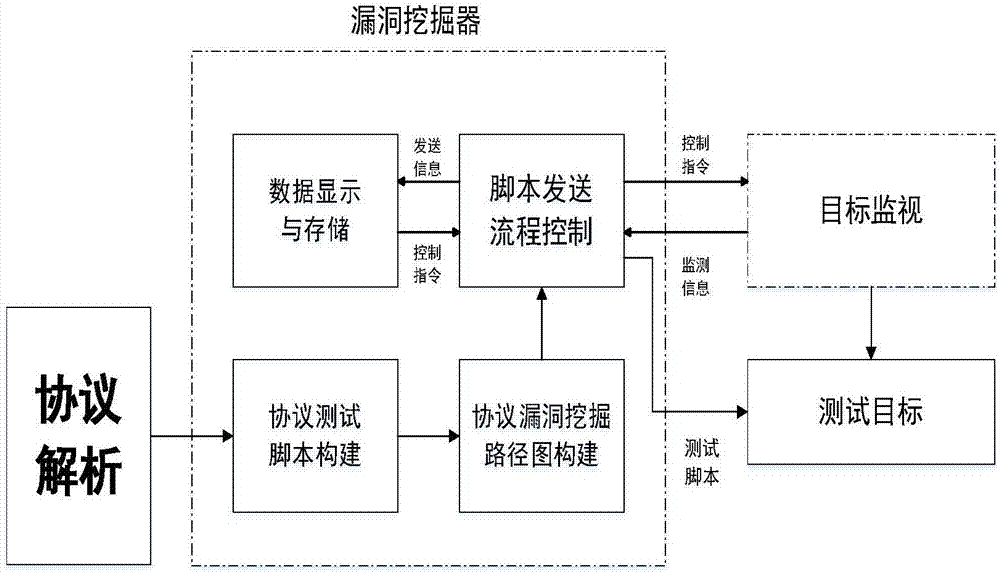
[0062] Step 1, protocol analysis: capture the network data packets of the test target, analyze the network protocol of the test target, and determine the protocol used by the test target and the corresponding protocol key information;
[0063] Step 2, protocol test script construction: According to the results of protocol analysis, comprehensively describe the key information of the protocol, model different data formats accordingly, and determine the various data formats and corresponding fields displayed by the protocol Information, the output is the information vector of the corresponding protocol data, that is, the protocol test script is generated;
[0064] Ste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com