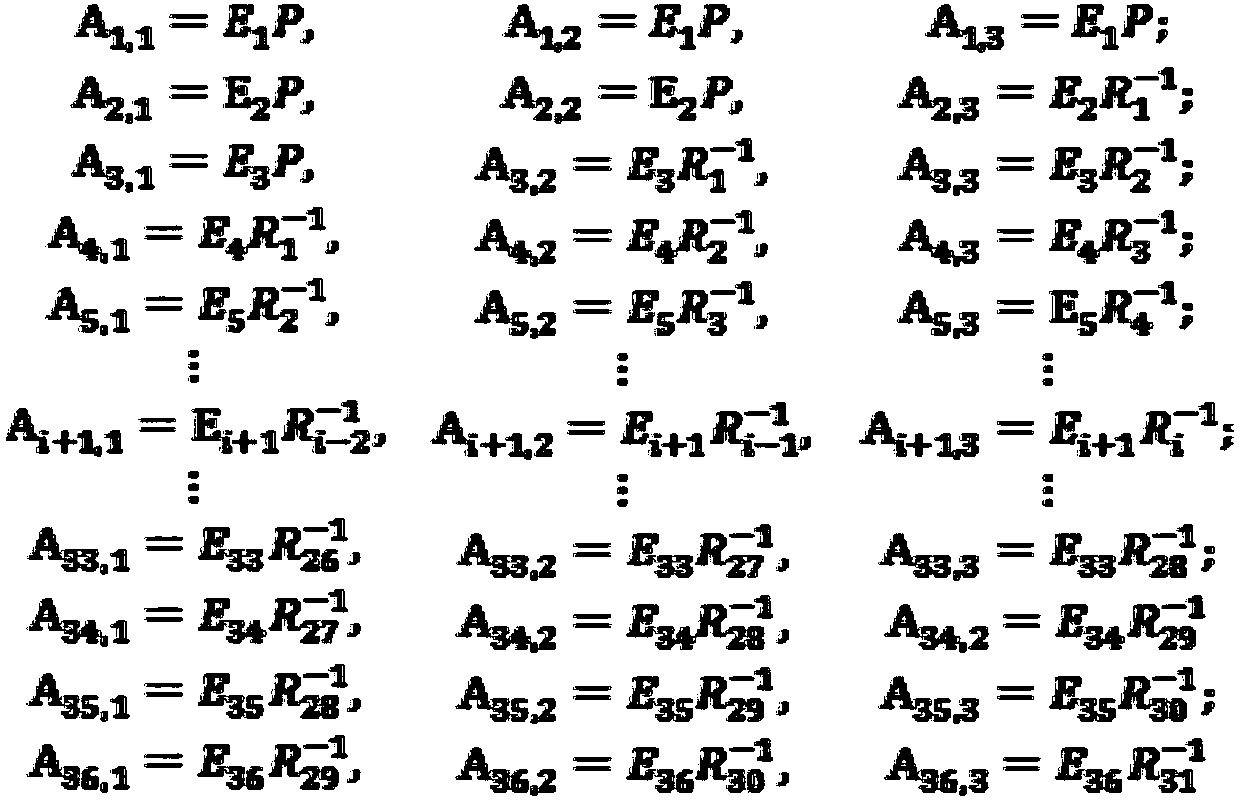White-box software implementation method of commercial code SM4 algorithm in standard ciphertext output format
A software implementation, encryption algorithm technology, applied in the field of information security, can solve problems such as unfavorable wireless LAN product key security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
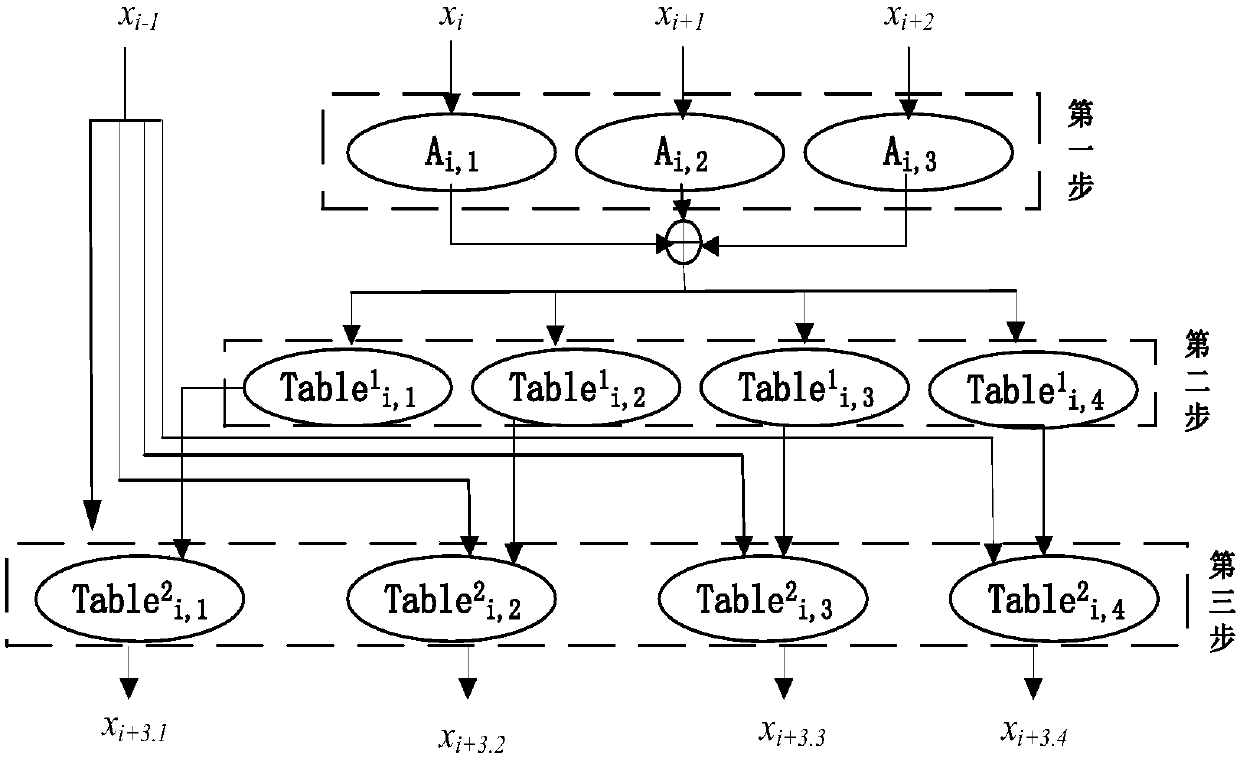
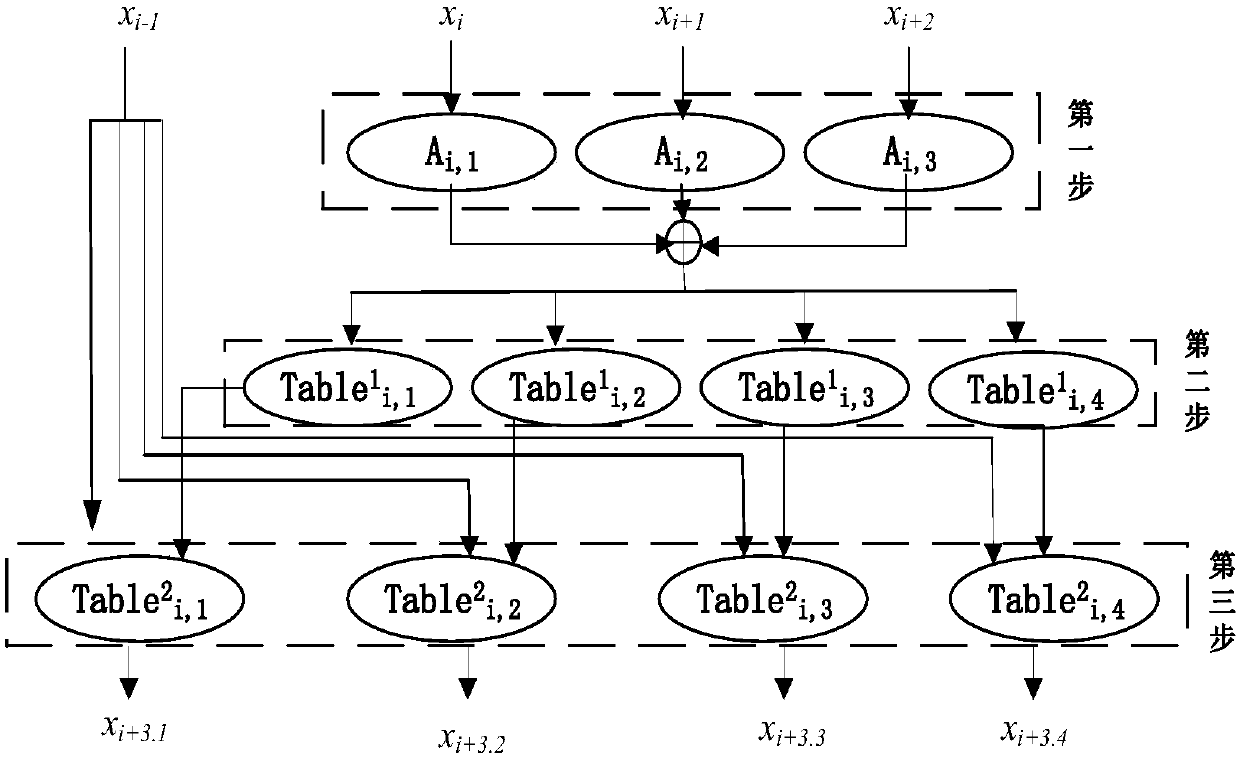
[0079] The design idea of the present invention is: each round of the algorithm is divided into three layers, each layer is confused by input or output transformation, the input and output transformation between layers is partially offset, and the layer containing the key is calculated by A lookup table is implemented, the key does not appear explicitly in the algorithm, and the key cannot be obtained by analyzing the intermediate data. In order to ensure that the output of the algorithm is in the standard ciphertext format, and at the same time protect the security of the initial and final round keys of the algorithm, we add the confusion matrix P in the first round. However, since the S-box nonlinear transformation cannot be restored after linear operations such as XOR and shift, the matrix must be canceled before passing through the S-box, and then added after passing through the S-box.
[0080] The present invention comprises the steps:
[0081] Step 1: Generate a set o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com