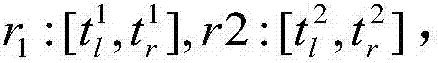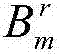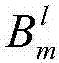Safe nearest neighbor searching method used in cloud computing
A nearest neighbor, cloud computing technology, applied in the field of information security and cloud computing, can solve the problems of security and efficiency data structures and algorithms are not secure enough, indexing is not efficient enough, data leakage and tampering, etc.
Inactive Publication Date: 2017-08-29
DONGGUAN UNIV OF TECH
View PDF0 Cites 9 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Nearest neighbor query is one of the basic problems in many fields. With the advent of cloud computing and big data era, outsourcing data to cloud servers has become very popular, but the data stored in the cloud may be leaked and tampered. Data security and privacy pose a huge threat, so how to perform nearest neighbor queries safely and efficiently is an urgent problem to be solved
In the existing technology, such as the secure nearest neighbor query method based on order-preserving encryption, an encryption method of asymmetric product preservation (ASPE), etc., cannot resist selective plaintext attacks, and the security and privacy of data cannot be obtained. Guarantee; there is another type of method based on asymmetric encryption and requires linear query time. Some methods require multiple communications between the user and the cloud server to execute a query. As the amount of data increases, the time required for the query will become more and more Long, bring bad experience to users, and there is another kind of method that needs to rely on secure hardware, making it difficult to promote this kind of method
To sum up, the problem of the existing technology is that the existing technology cannot guarantee both safety and high efficiency
The reason why the existing technology cannot guarantee security and efficiency is that its data structure and algorithm are not secure enough, and attackers can obtain data information or query information through selective plaintext attacks, etc., and on the other hand, its index is not efficient enough , the time complexity of executing the query operation is high, causing users to need a long time to query data
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention belongs to the technical field of cloud computing and information security, and discloses a safe nearest neighbor method used in cloud computing. The safe nearest neighbor method used in cloud computing includes: using a Voronoi graph to divide a 2-D space; and using two arrays to construct two kinds of safe data structures including a single-homing Bloom filter and a multi-homing bloom filter. To ensure the security of data, the 2-D safe nearest neighbor searching problem is converted into a problem of determining if a point is in a certain range or not, and then a problem of determining if two sets intersects or not is converted. The Voronoi graph based 2-D space division scheme and the two kinds of data structures including the single-homing Bloom filter and a multi-homing bloom filter can ensure performing correct nearest neighbor searching in the condition that a server does not know a data real value and a search real value, the security demand of IND-CPA can be met, and the sub-linear searching time can be reached.
Description
A Secure Nearest Neighbor Retrieval Method in Cloud Computing technical field The invention belongs to the fields of cloud computing and information security, and in particular relates to a safe nearest neighbor retrieval method in cloud computing. Background technique Nearest neighbor query is one of the basic problems in many fields. With the advent of cloud computing and big data era, outsourcing data to cloud servers has become very popular, but the data stored in the cloud may be leaked and tampered. Data security and privacy pose a huge threat, so how to perform nearest neighbor query safely and efficiently is an urgent problem to be solved. In the existing technology, such as the secure nearest neighbor query method based on order-preserving encryption, an encryption method of asymmetric product preservation (ASPE), etc., cannot resist selective plaintext attacks, and the security and privacy of data cannot be obtained. Guarantee; there is another type of method ba...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F17/30
CPCG06F16/90335G06F16/9027
Inventor 李睿
Owner DONGGUAN UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com