Intelligent security management system and control method thereof
A management system and security technology, applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve the problems that cannot solve the hidden dangers of the owner of the IC card duplication technology security system, and achieve the goal of solving security loopholes Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
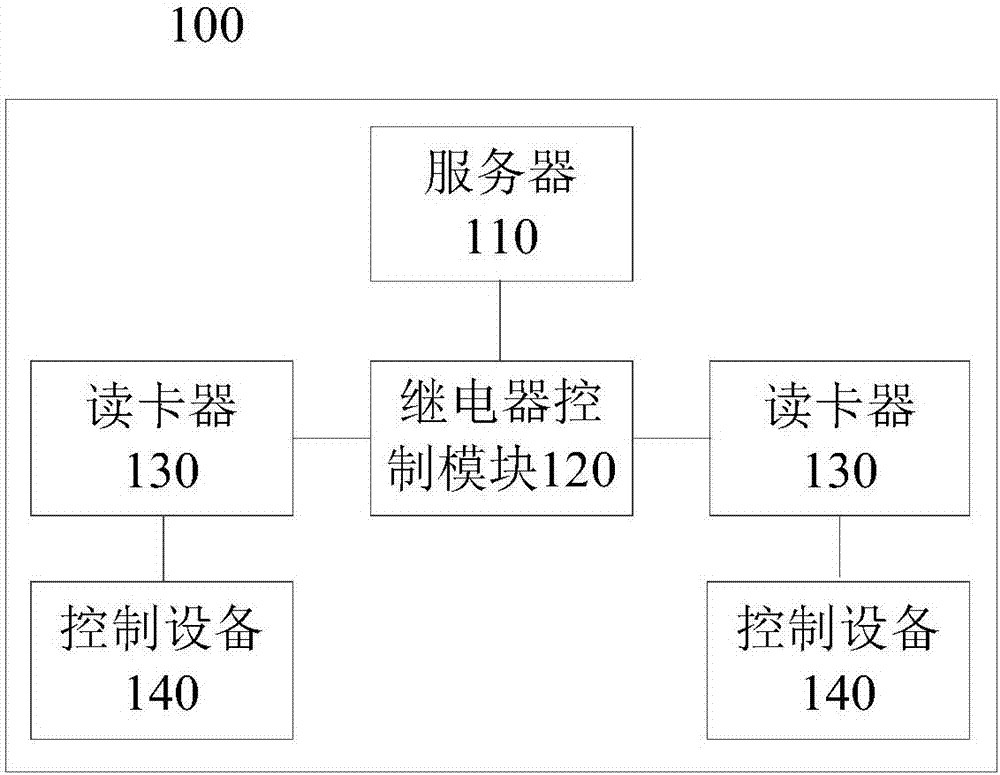
[0018] Please refer to figure 1 , figure 1 It is a structural block diagram of an intelligent security management system 100 provided in the first embodiment of the present invention, including: a server 110, a relay control module 120, a plurality of card readers 130, and a control device corresponding to each of the card readers 130 140.
[0019] Wherein, the server 110 may be a network server, a database server, etc., and may establish a communication connection with the relay control module 120 for sending control parameters and instructions to the relay control module 120 . The control parameters and instructions can be implemented by logic programming, and can be modified according to actual conditions. At the same time, the server 110 is also used to receive the user's ID data sent by the relay control module 120 , of course, the user's ID data needs to be entered in the server 110 in advance.
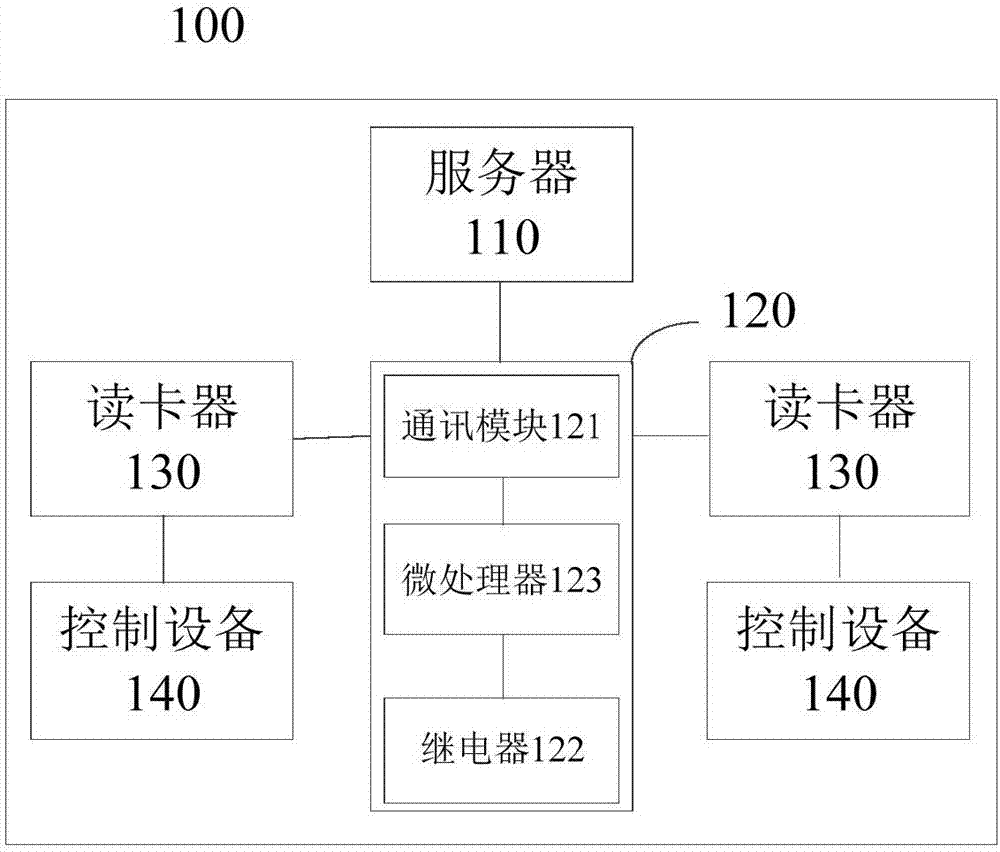
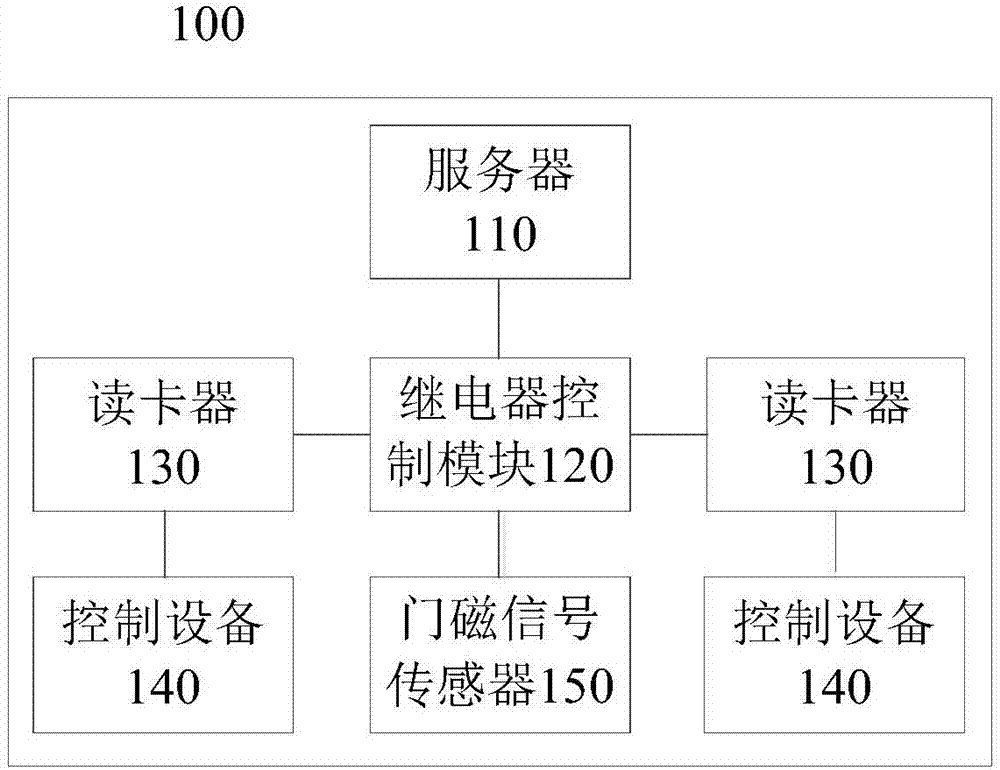
[0020] Please see figure 2 , the relay control module 120 may include:...
no. 2 example
[0047] Please refer to Figure 5 , Figure 5 It is a flowchart of a control method of an intelligent security management system provided by the second embodiment of the present invention. The method is applied to an intelligent security management system, the intelligent security management system includes a server, a relay control module, a plurality of card readers and a control device corresponding to each of the card readers, the relay control module router, mobile The terminal establishes a network connection with the server, and the relay control module is respectively coupled with each of the card readers and each of the control devices. The following will be Figure 5 As illustrated in the flow chart, the method includes:
[0048] Step S110: the card reader reads user ID data.
[0049] Step S120: The relay control module obtains the address and user ID data of the card reader, and sends them to the server.
[0050] Step S130: the server sends control parameters an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com