Collaborative signature and decryption method, apparatus and system of SM2 algorithm
An algorithm and hash algorithm technology, applied in the field of cryptography, can solve problems such as the inability to protect user privacy, and achieve the effect of less application requirements, low delay, and less interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
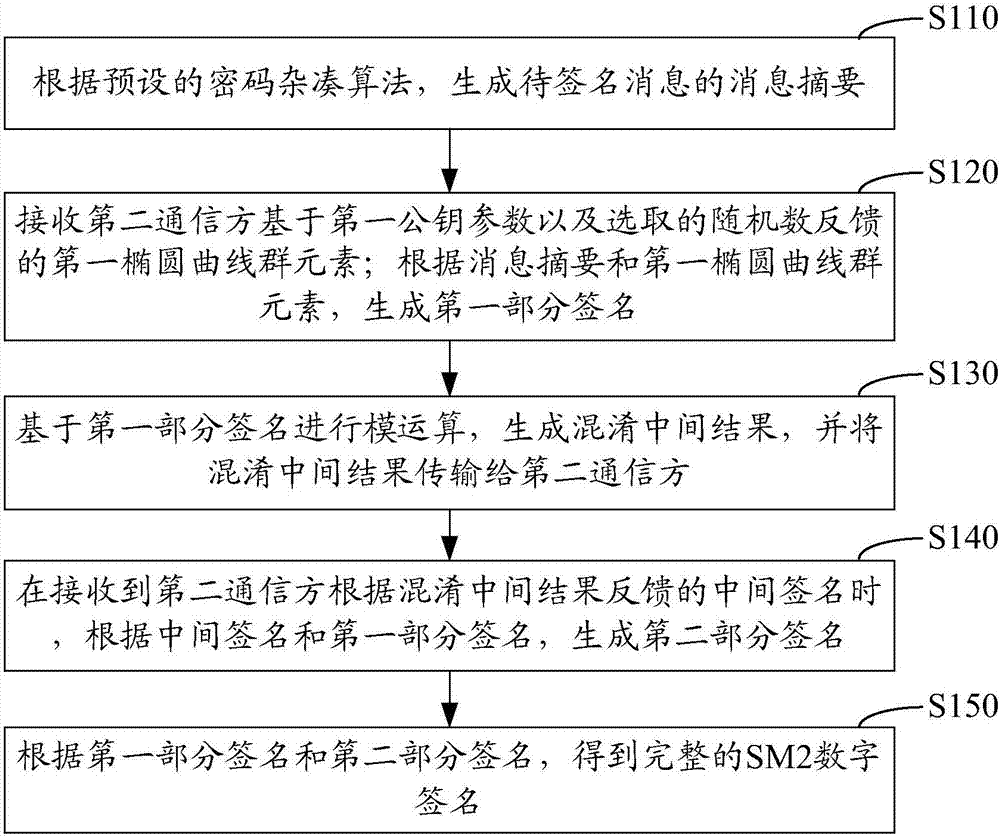
[0081] In order to solve the problem that traditional technologies cannot protect user privacy and resist malicious attacks, the present invention provides an embodiment 1 of an SM2 algorithm collaborative signature method implemented from the perspective of the first communication party; figure 1 It is a schematic flow chart of Embodiment 1 of the SM2 algorithm cooperative signature method implemented from the perspective of the first communication party in the present invention; as figure 1 As shown, the following steps may be included:
[0082] Step S110: Generate a message digest of the message to be signed according to a preset cryptographic hash algorithm;
[0083] Step S120: receiving the first elliptic curve group element fed back by the second communication party based on the first public key parameter and the selected random number; generating the first partial signature according to the message digest and the first elliptic curve group element;
[0084] Step S130: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com