Configurable multiplication device applied to AES and RSA mixed algorithm hardware circuit
A hardware circuit, hybrid algorithm technology, applied in encryption devices with shift registers/memory, secure communication devices, electrical components, etc., can solve the problems of cost, multiple circuit area and logic, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
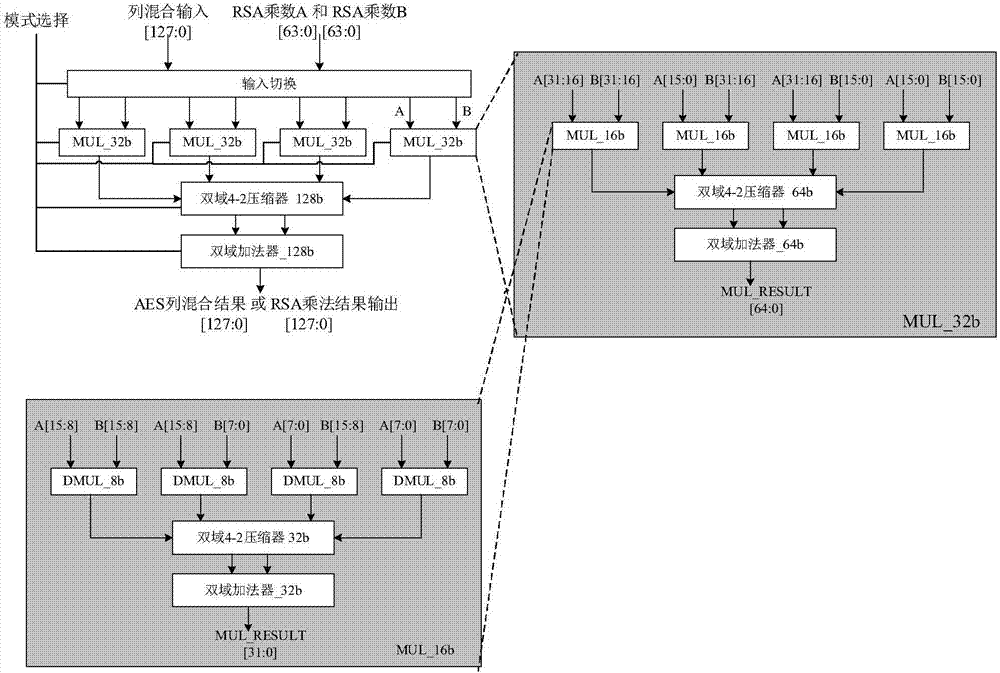
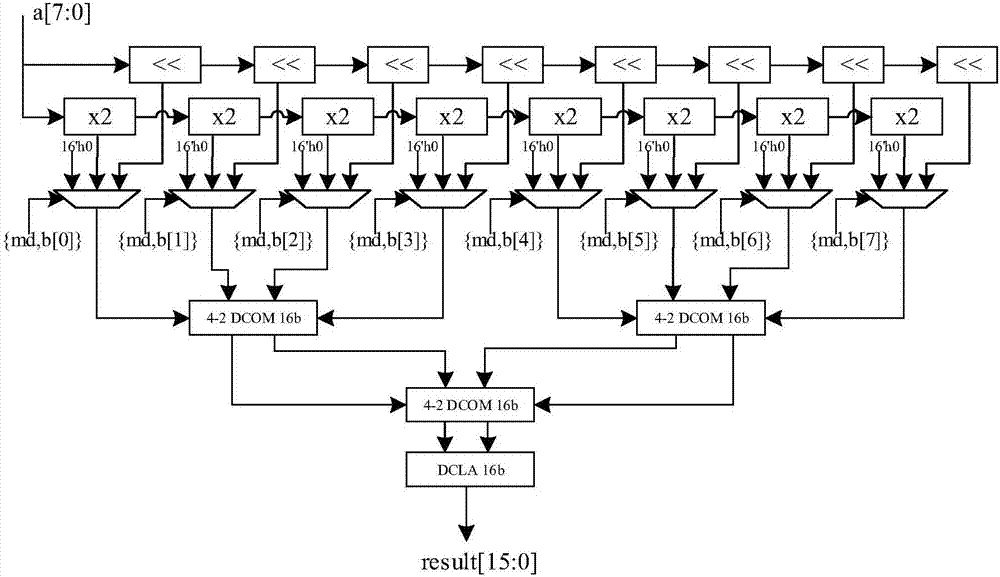
[0018] figure 1 Shown is a block diagram of the internal structure of a configurable multiplication device that can be used in AES and RSA mixed algorithm hardware circuits of the present invention. The device organizes multipliers and adders according to a special structure to realize configurable AES column mixing and RSA 64bit multiplication. In the figure, a 16-bit dual-field multiplier is realized by using four 8-bit dual-field multipliers, one 32-bit dual-field 4-2 compressor and one 32-bit dual-field look-ahead carry adder; and then four 16-bit dual-field multipliers , 1 64bit dual-field 4-2 compressor and 1 64bit dual-field look-ahead adder to realize 32bit dual-field multiplier; 4 32bit dual-field multipliers, 1 128bit dual-field 4-2 compressor and 1 A 128bit double-field look-ahead adder implements a 64bit double-field multiplier. Therefore, the implementation scheme shown in the figure includes the following 4 parts: 1. Multiplier array composed of 64 8bit multipl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com