System dispatching method
A kind of employee, unique technology, applied in the field of management software system dispatch, can solve problems such as affecting task execution, prone to errors, increasing internal friction, etc., to achieve the effect of guaranteeing the execution cycle, convenient and fast operation, and reducing workload
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
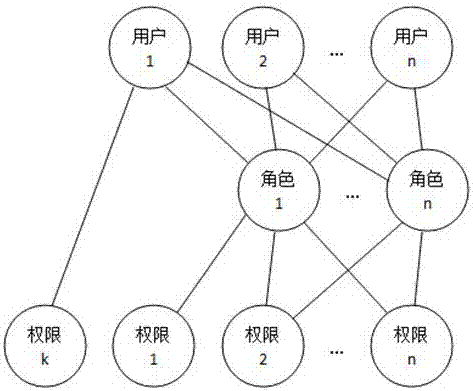
[0059] [Example 1] such as Figure 5 As shown, a system dispatching method includes a step of determining the dispatched task, a step of determining the dispatched object and a dispatching step;
[0060] S1: Steps to determine the task to be dispatched: determine the task that needs to be dispatched. The task can be the content filled in manually, or the specified form data or the content brought out by the specified form data (such as dispatching a worker to process a documentary , dispatching workers to handle a complaint, specifying to handle an installation request, etc.), or a combination of the three; tasks include: production tasks, sales tasks, logistics tasks, after-sales tasks, and other tasks that need to be dispatched .
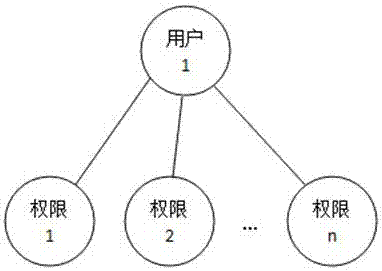
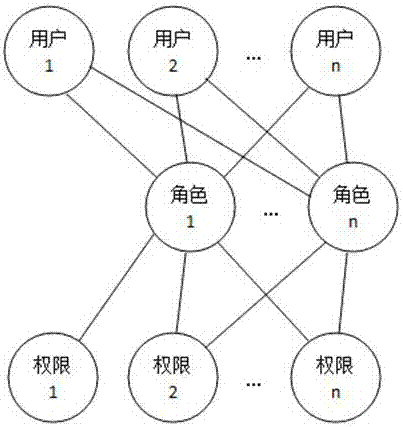
[0061] S2: The step of determining the object to be dispatched: determine the object to be dispatched, and the object is a role, such as Figure 4 As shown, the role is an independent individual, not a group / class. A role can only be associated ...
Embodiment 2
[0066] [Example 2] such as Figure 5As shown, a system dispatching method includes a step of determining the dispatched task, a step of determining the dispatched object and a dispatching step;
[0067] SS1: Steps to determine the dispatched object: determine the dispatched object, the object is a role, and the role is an independent individual, not a group / class. A role can only be associated with a unique user at the same time, and a A user is associated with one or more roles;
[0068] SS2: Steps for determining the tasks to be dispatched: determine the tasks that need to be dispatched;
[0069] SS3: Work assignment step: The dispatcher assigns the tasks that need to be dispatched to the dispatched role, and the employees corresponding to the users associated with the dispatched role get the dispatched tasks. A dispatcher can be a role, a user, or a person.
[0070] If the user needs to transfer jobs across departments, a user cross-department job transfer management ste...
Embodiment 3
[0076] [Example 3] such as Figure 5 As shown, a system dispatching method includes a step of determining the dispatched task, a step of determining the dispatched object and a dispatching step;
[0077] S1: The step of determining the tasks to be dispatched: determine the tasks that need to be dispatched;
[0078] S2: The step of determining the assigned object: determine the assigned object, the object is a role, the role is an independent individual, not a group / class, a role can only be associated with a unique user at the same time, and a A user is associated with one or more roles;
[0079] S3: Work dispatching step: dispatch tasks that need to be dispatched to the dispatched role, and the employees corresponding to the users associated with the dispatched role obtain the dispatched tasks. The time assigned by the dispatcher is a time period, not an exact time point, as long as it is completed within this time period, it is considered normal completion.
[0080] It al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com