A virtualization packing method based on elf infection android local layer instruction compilation
A local layer, instruction technology, applied in the direction of instruments, computing, electrical digital data processing, etc., can solve the problems of weak operability, compiling confusion, unable to deal with dynamic analysis reverse attackers in essence, to increase attack cost, The effect of excellent performance and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
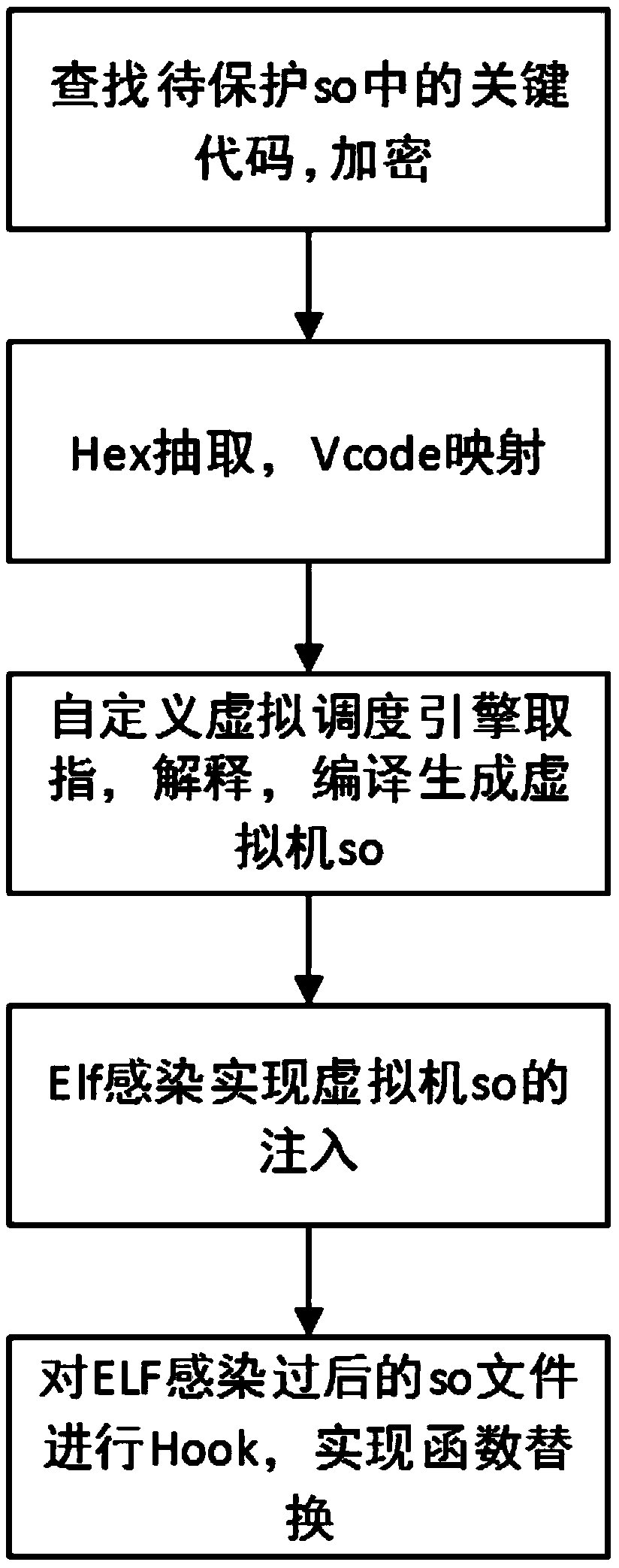
[0026] The present invention proposes a kind of Android local layer instruction compilation virtualization packing method based on ELF infection, comprising the following steps:
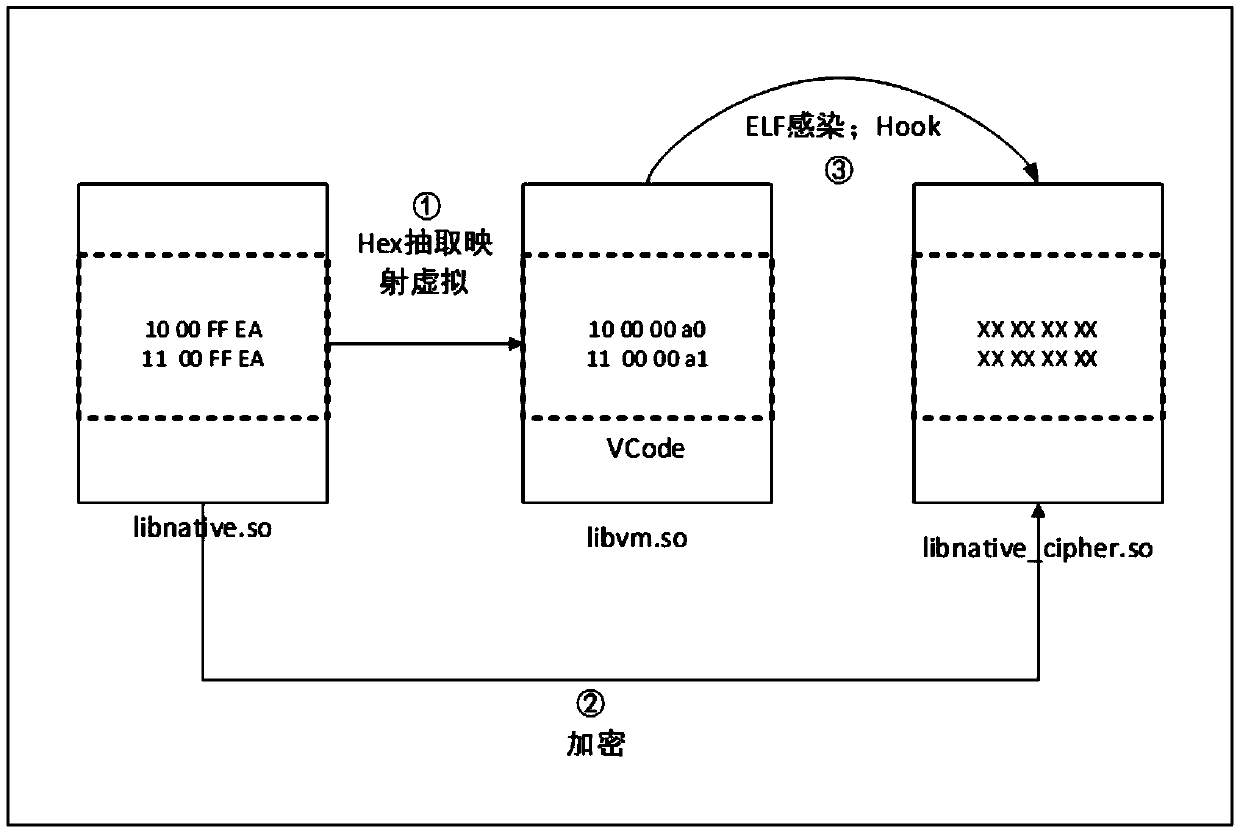
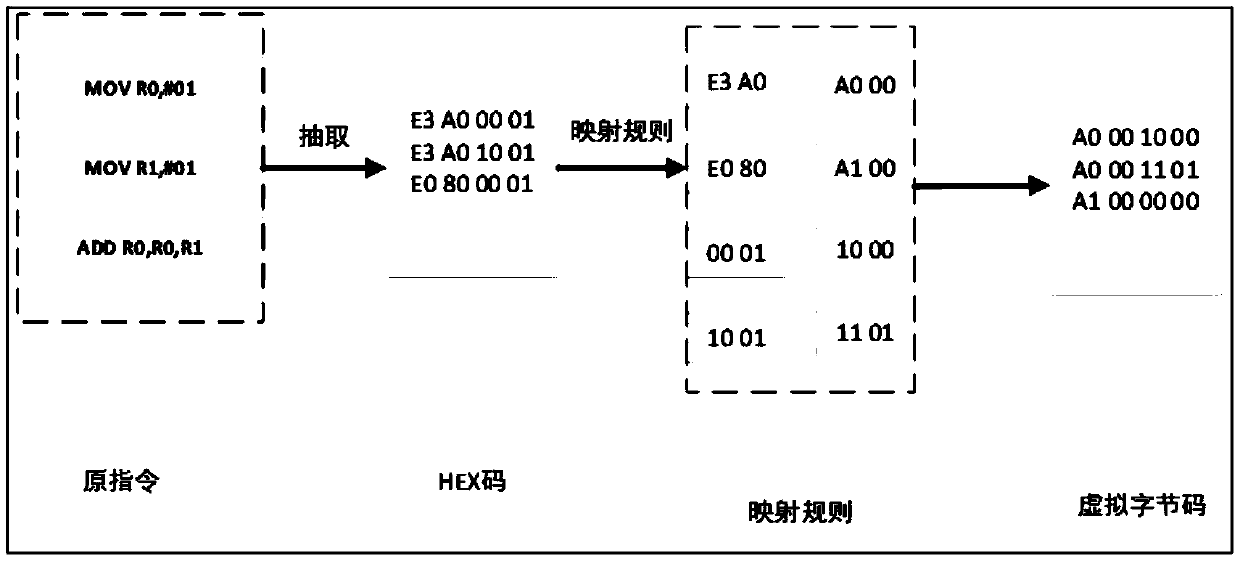
[0027] Step 1, input the Android local layer dynamic link library file to be protected, usually in .so file format, called so file; find the key code segment that needs to be protected in the so file, and perform instruction Hex extraction and mapping virtual to the key code segment , forming a virtual machine so file;
[0028] Such as figure 2 As shown, in this embodiment, libnative.so is the so file to be protected. The present invention first searches and locates the key code segment according to the label provided by the developer, as shown in the dotted line area in the figure, and HEX extracts this part of the code , use the custom mapping rules to map and transform the extracted results.
[0029] The so-called custom mapping rule refers to setting a set of mapping rules by itself, so that t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com