Password management method, electronic device and computer storage medium
A password management and password technology, which is applied in the field of data security, can solve security problems, database server user names and password information are easily leaked, and achieve the effects of avoiding leaks, ensuring transmission security, and ensuring password security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
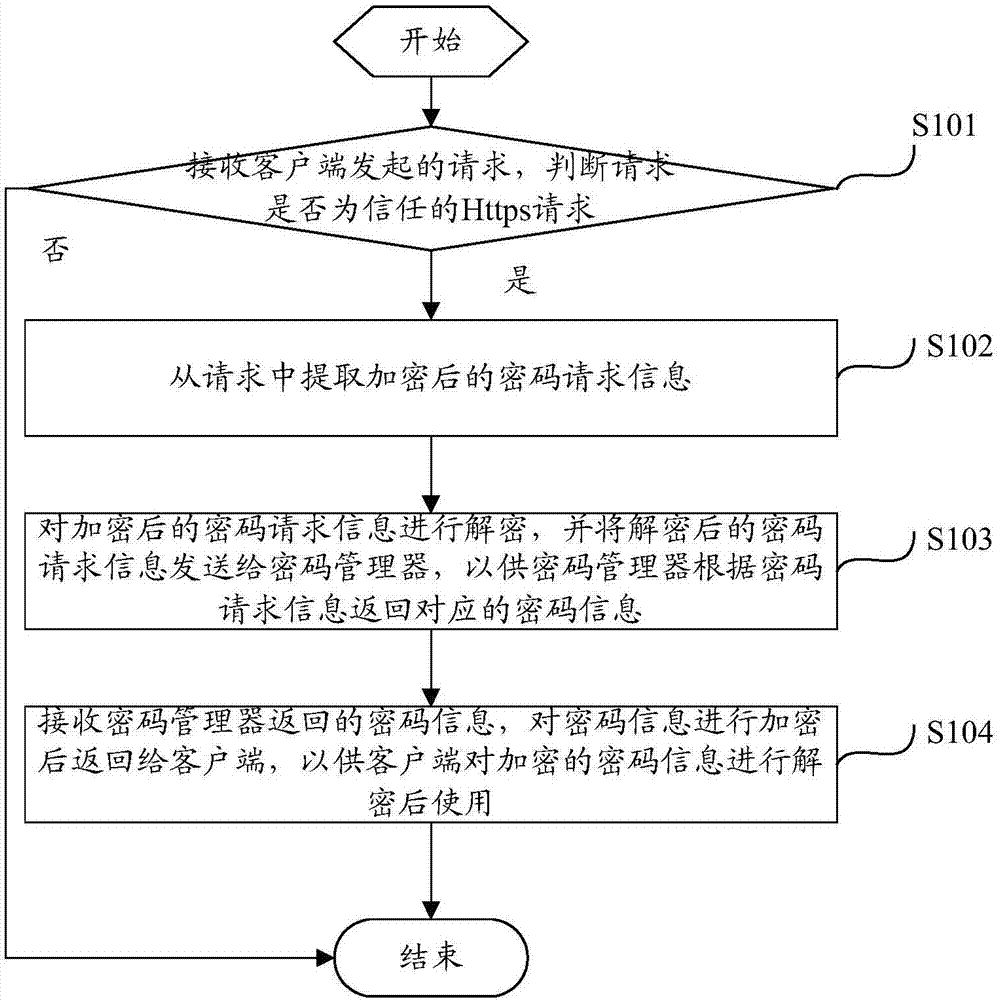
[0030] figure 1 Shows a flowchart of a password management method according to the first embodiment of the present invention, such as figure 1 As shown, the password management method specifically includes the following steps:
[0031] Step S101: Receive a request initiated by the client, and determine whether the request is a trusted Https request.
[0032] The request initiated by the client can use Http request based on Http Hypertext Transfer Protocol, or Https request based on Https Secure Socket Layer Hypertext Transfer Protocol. However, because the Http protocol sends content in plain text and does not provide any means of data encryption, it is extremely easy for attackers to intercept the transmission message and crack the information in it. Https requests are transmitted in encrypted mode when transmitting messages. Even if the attacker intercepts the transmission message, the information in it cannot be cracked, which ensures the security of message transmission. There...
Embodiment 2
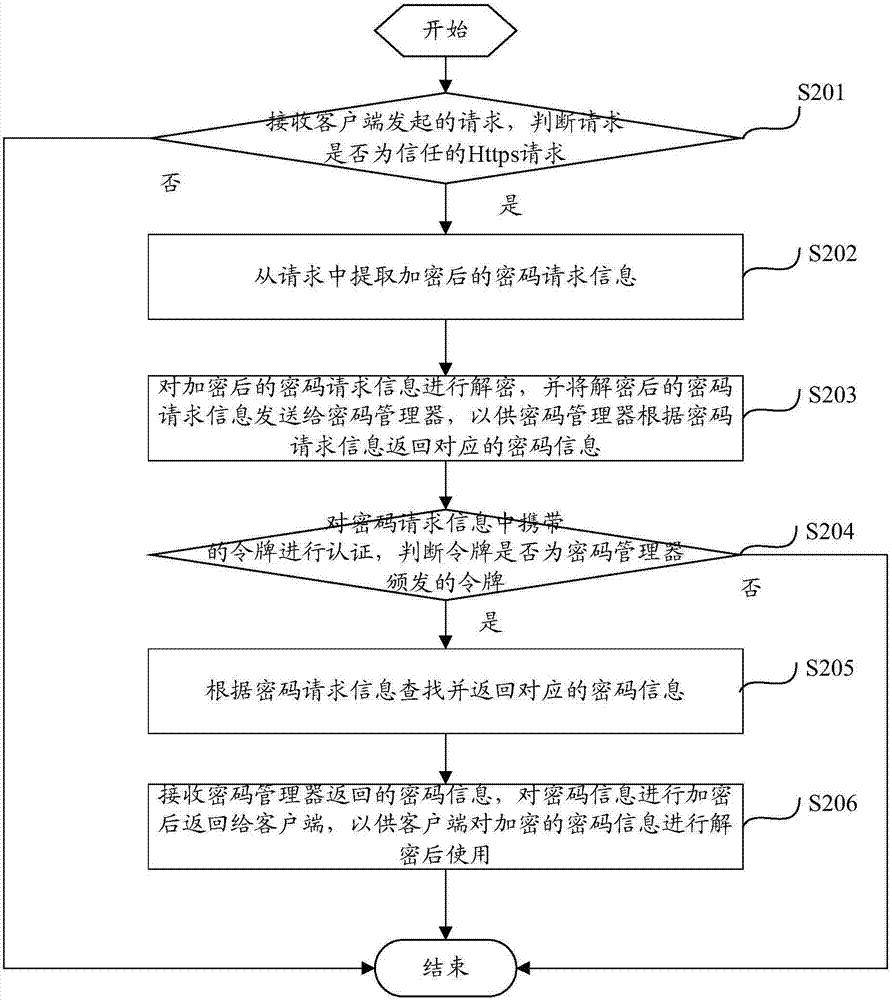
[0043] figure 2 Shows a flowchart of a password management method according to the second embodiment of the present invention, such as figure 2 As shown, the password management method includes the following steps:
[0044] Step S201: Receive a request initiated by the client, and determine whether the request is a trusted Https request.
[0045] Step S202: Extract the encrypted password request information from the request.
[0046] Step S203: Decrypt the encrypted password request information, and send the decrypted password request information to the password manager.
[0047] The above steps refer to the description of steps S101-S103 in the first embodiment, and will not be repeated here.
[0048] Step S204, the token carried in the password request information is authenticated, and it is determined whether the token is a token issued by the password manager.
[0049] The password manager may use an authentication mechanism to authenticate the sender of the password request inform...
Embodiment 3
[0058] The third embodiment of the present application provides a non-volatile computer storage medium, the computer storage medium stores at least one executable instruction, and the computer executable instruction can execute the password management method in any of the foregoing method embodiments.
[0059] The executable instructions may be specifically used to cause the processor to perform the following operations:
[0060] Receive the request initiated by the client and determine whether the request is a trusted Https request;
[0061] If yes, extract the encrypted password request information from the request;
[0062] Decrypt the encrypted password request information, and send the decrypted password request information to the password manager for the password manager to return the corresponding password information according to the password request information;
[0063] Receive the password information returned by the password manager, encrypt the password information and retu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com