Security control method and system based on CPK intelligent switch device
A smart switch and security control technology, applied in the field of data security, can solve problems such as the inability to realize remote unlocking, and achieve the effect of improving convenience, safety, and convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
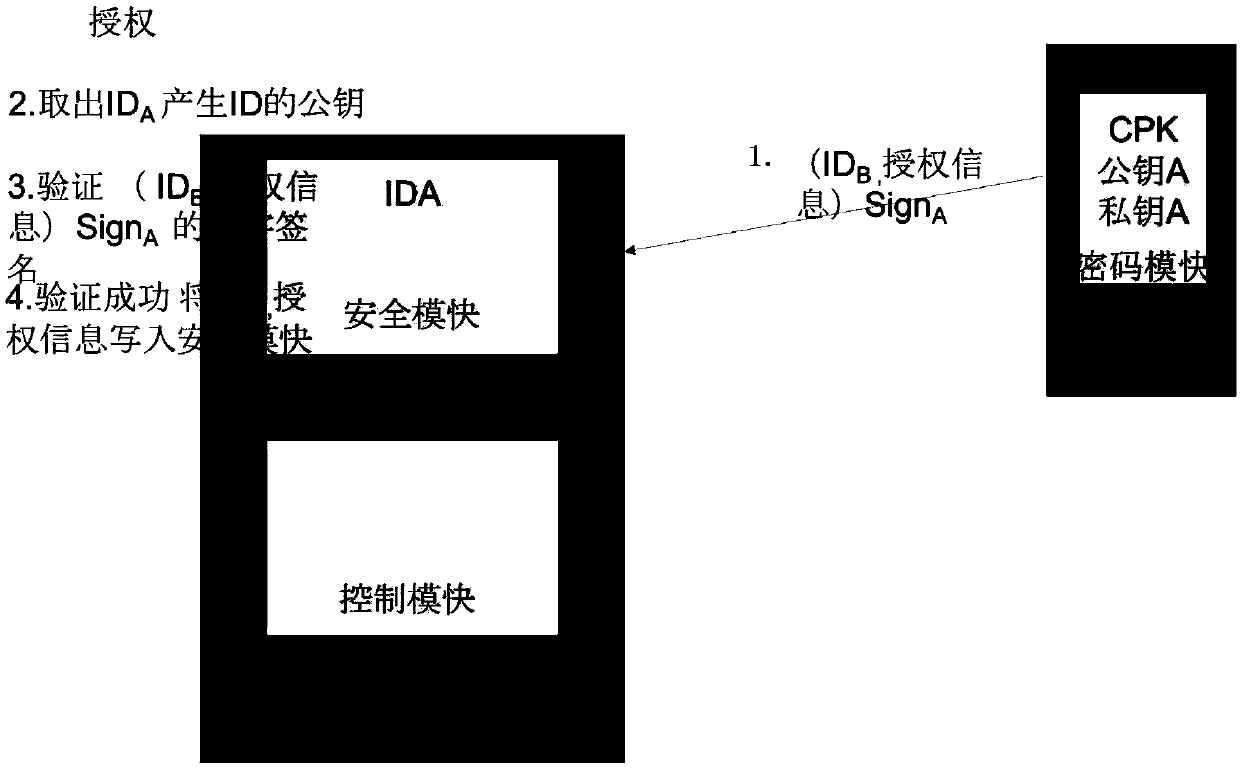
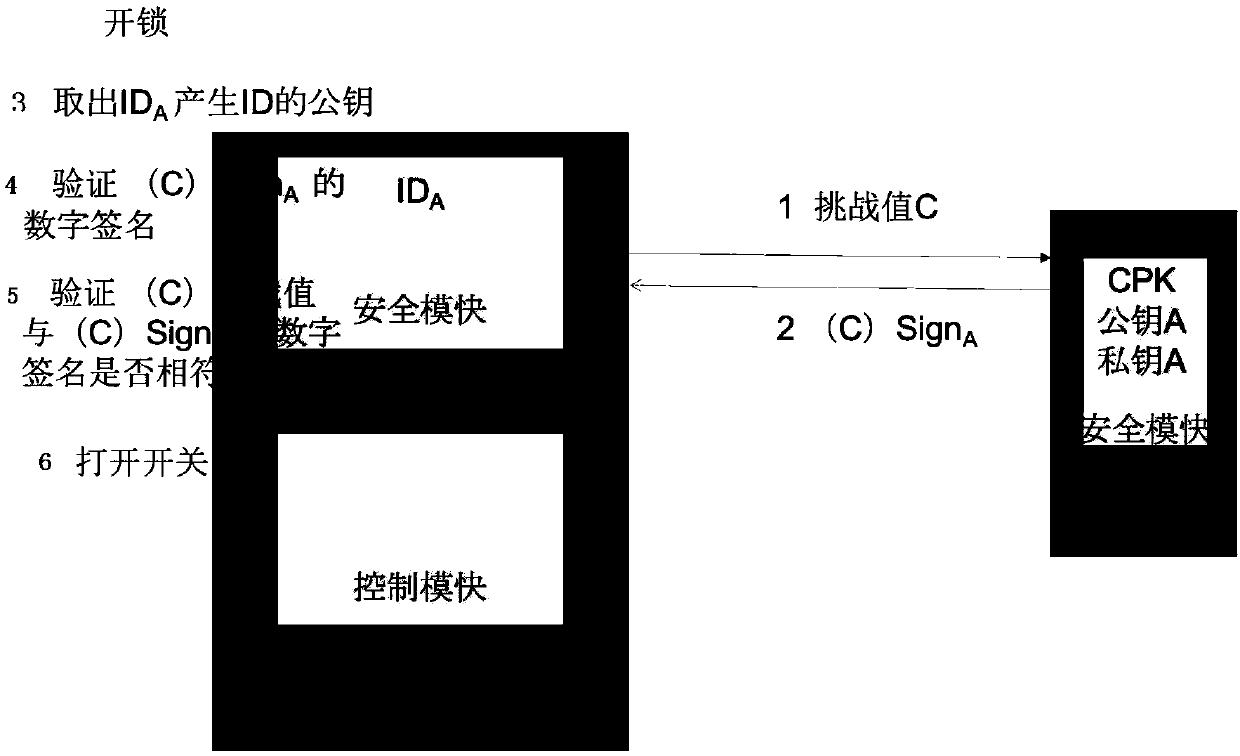
[0035] For smart devices based on the CPK identification authentication mechanism, the CPK security module is added to the smart device. According to the key characteristics of the CPK, the overall security mechanism is established in the CPK security module. When the smart device is connected to the Internet, all data must be encrypted. And the source of data must be confirmed, and effective security control is carried out through data encryption and data signature. This mechanism can be used with various identification methods for users, such as fingerprint / iris and other two-factor authentication methods.
[0036]
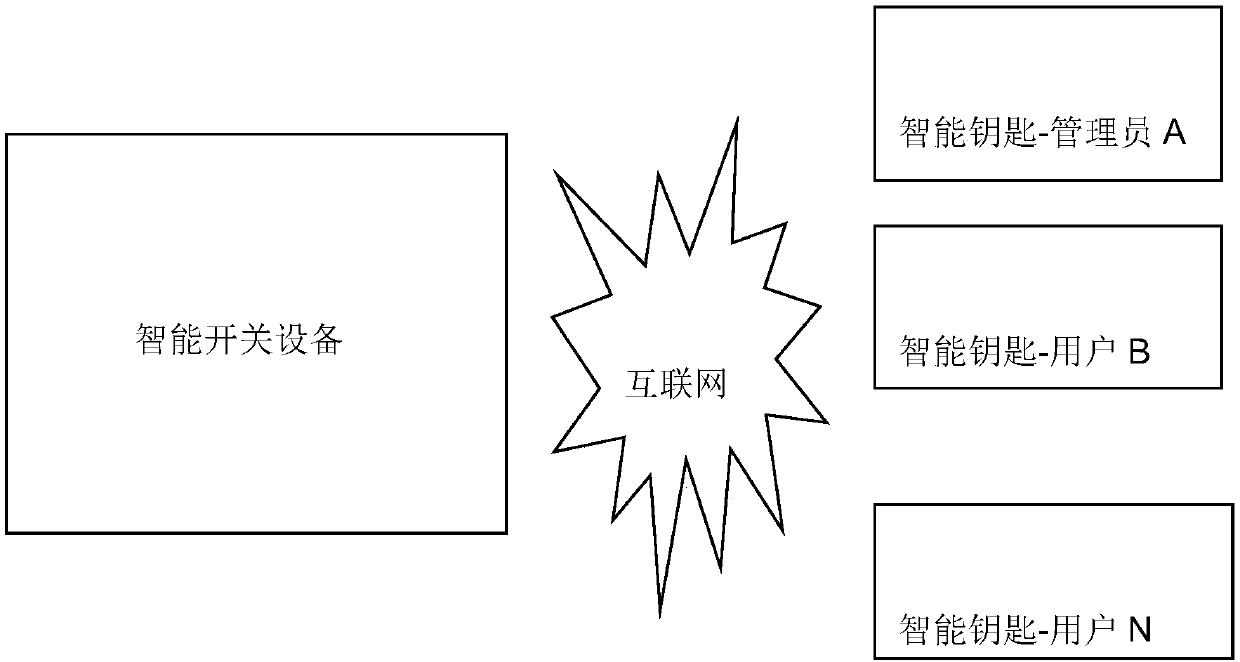
[0037] Such as figure 1 , is a system architecture diagram of the present invention.
[0038] The invention includes a smart switchgear and at least one smart key. Wherein, at least one smart key includes a management smart key with management authority, and there may be no user smart key, or one or more user smart keys.
[0039] The invention integrates the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com