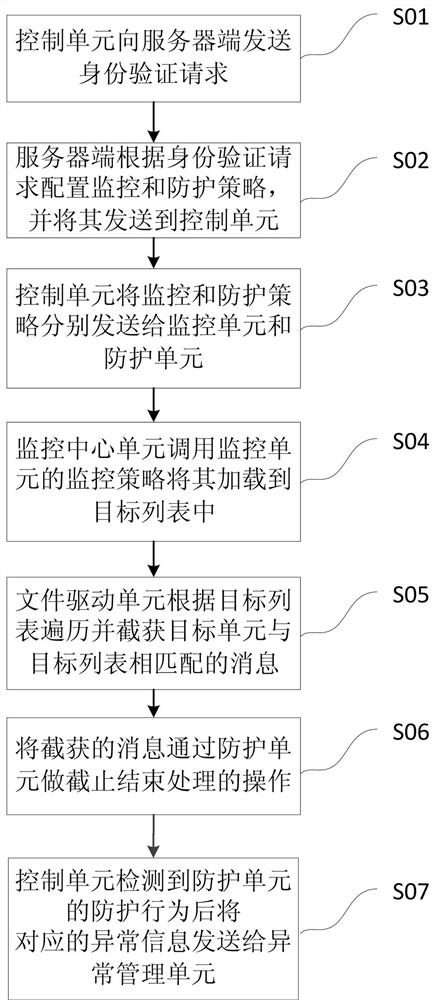
A system and method for preventing illegal outreach of local area network computers
A computer and local area network technology, applied in transmission systems, electrical components, etc., can solve problems such as cross-security domain damage, network structure, server deployment, and leakage of security protection measures, and achieve the effect of protecting information security confidentiality and computer security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments, but the protection scope of the present invention is not limited thereto.
[0038] At present, the commonly used security protection methods to control USB storage devices or mobile devices are often based on modifying the registry or USB drivers or hiding drive letters. This method is often powerless for controlling mobile phones, tablet computers, etc. to connect to the Internet , because although these devices use the USB interface for transmission, the communication protocols are completely different, and with the assistance of third-party software, it is difficult to effectively deal with such storage devices through the registry, modifying the USB drive or hiding the drive letter. It is extremely easy to be bypassed by someone with a little technical knowledge by reversely modifying the registry, repairing the USB drive, or redispl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com