Cyber theft behavior detection method based on DNS traffic analysis and device
A flow analysis and network technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems that firewalls cannot completely control malware infection and data leakage, and achieve the effect of relatively low detection cost, simple specification, and small DNS protocol traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
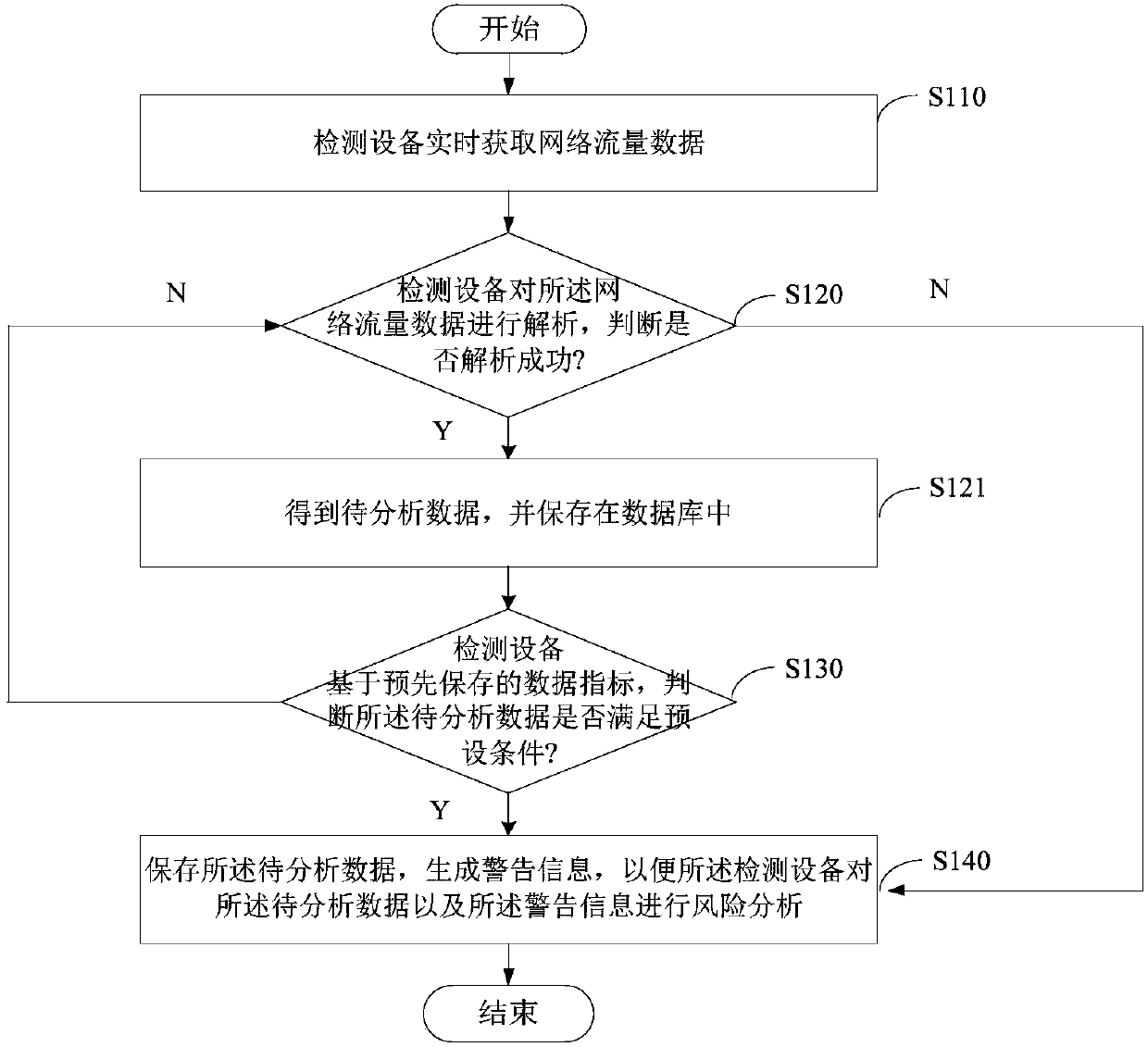
[0027] Please refer to figure 2 , figure 2 It is a flow chart of a method for detecting network stealing behavior based on DNS traffic analysis provided by the first embodiment of the present invention, and the method is applied to a detection device. The following will be figure 2 The process shown is described in detail, and the method includes:
[0028] Step S110: The detection device acquires network traffic data in real time.
[0029] The detection equipment can directly collect data from the network card, and can also directly receive network traffic data sent by other systems.
[0030] Step S120: the detection device analyzes the network traffic data, and judges whether the analysis is successful.
[0031] The detection device can analyze the network flow data based on the RFC protocol specification, and restore the operator's original network behavior information. Further, the protocol analysis module can analyze the information of both communication parties f...
Embodiment approach
[0039] As an implementation, the detection device may pre-acquire the IP address and the domain name of the C&C (Command and Control) server accessed by the target malware, and use the IP address and the domain name of the C&C server as a domain name blacklist Save to the blacklist library.
[0040] The preset condition may be: the IP address and domain name accessed by the data to be analyzed are the IP address and domain name of the C&C server in the blacklist database.
[0041] As another implementation manner, before step S110, the detection device may also acquire a plurality of normal domain name data accessed by the target network device during daily work within a preset time, and the domain name data includes a domain name and a subdomain name.
[0042] The preset time may be one week or half a month. It is worth pointing out that during this period of time, the target network equipment (computer equipment in the internal network of the unit) must be in a daily workin...
no. 2 example
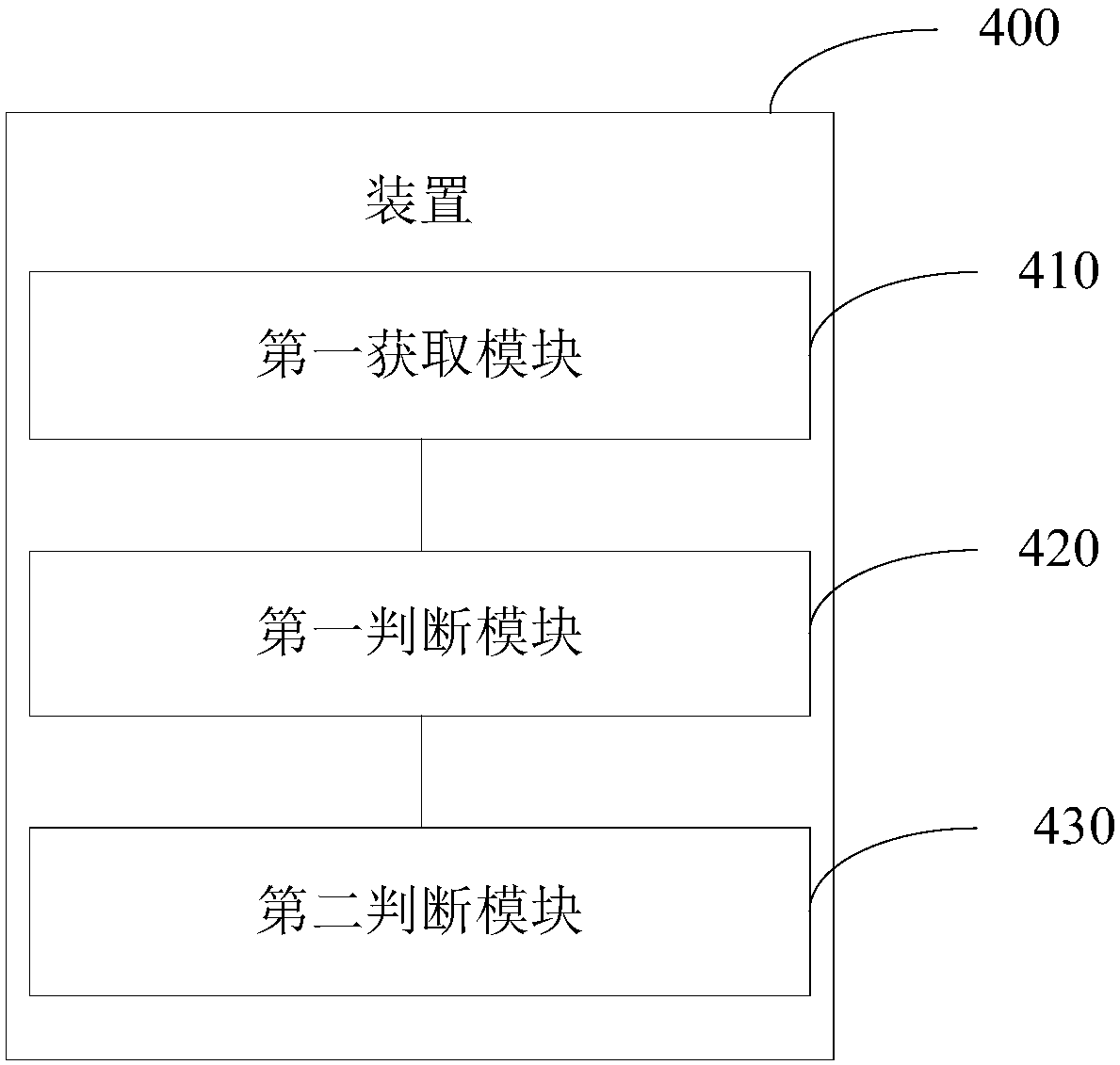
[0072] Please refer to image 3 , image 3 It is a structural block diagram of an apparatus 400 for network stealing behavior detection based on DNS traffic analysis provided by the second embodiment of the present invention. The following will be image 3 The structure block diagram shown is described, and the shown device includes:
[0073] The first acquisition module 410 is configured to acquire network traffic data in real time;
[0074] The first judging module 420 is configured to analyze the network traffic data, and obtain the data to be analyzed when judging that the parsing is successful;
[0075] The second judging module 430 is used to judge whether the data to be analyzed satisfies the preset condition based on the pre-saved data indicators, and if yes, save the data to be analyzed and generate a warning message, so that the detection device can Perform risk analysis on the data to be analyzed and the warning message.
[0076] As an implementation, see Fig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com