Security protection component interconnection structured system and implementation method
A security protection and interconnection structure technology, applied in the field of network security, can solve problems such as easy interception of the communication process, fraudulent use of the main Client and Server, malicious tampering of communication information, etc., and achieve the effect of integrity protection of the communication process and credible identity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
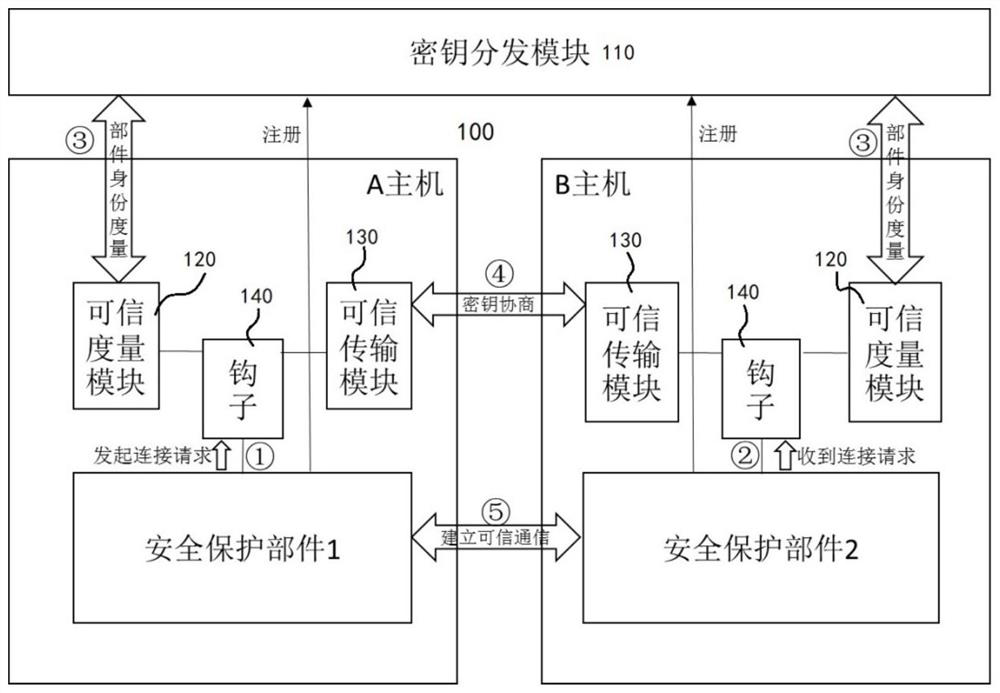
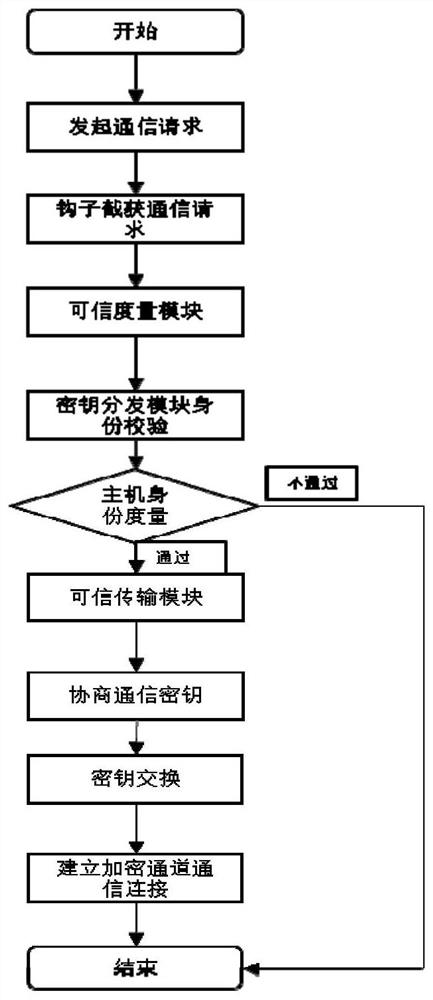
[0034] According to the "GB / T25070 Information System Hierarchical Protection Security Design Technical Requirements" on the structural description of the interconnection of security protection components, the technical focus is: 1. Mutual verification of each other's credibility through a trusted verification mechanism; 2. Ensure the security protection components trusted connection.
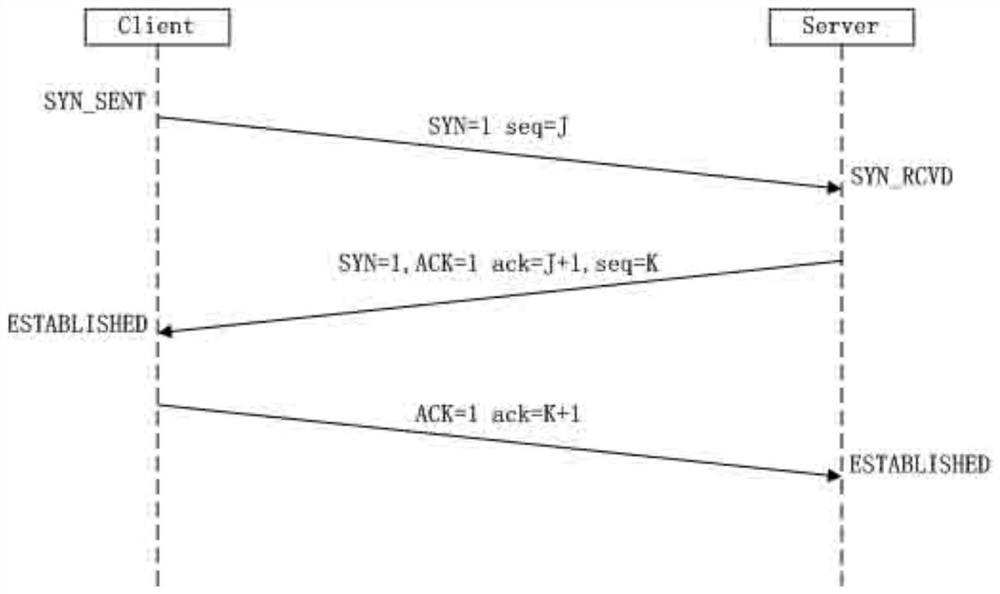
[0035] There are various ways for resource devices to communicate, such as TCP connection, UDP communication, HTTP communication, FTP communication and so on. Regardless of the communication method, the main body of the communication is a program, process or service. In this example, the communication program or process is used as a security protection component,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com