Key management, data encryption and identity authentication method oriented to electrical measuring instrument
A technology of data encryption and identity authentication, which is applied in the field of information security and can solve problems such as interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The accompanying drawings are only for illustrative purposes and cannot be understood as a limitation of the patent; in order to better illustrate this embodiment, some parts of the accompanying drawings may be omitted, enlarged or reduced, and do not represent the size of the actual product; For personnel, it is understandable that some well-known structures in the drawings and their descriptions may be omitted. The positional relationship described in the drawings is only for illustrative purposes and cannot be understood as a limitation of the patent.
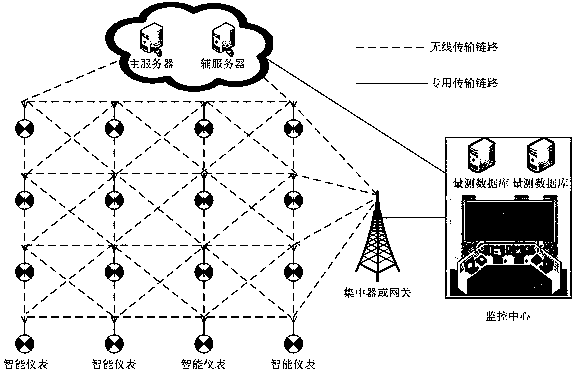
[0065] Such as figure 1 The power measurement instrument shown in the large-scale network deployment application scenario, the power measurement instrument periodically uploads the collected and stored data to the monitoring center according to the specified time frequency, and various smart electrical equipment connects to the electricity through the network The measurement instruments are interconnected to form a Home...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com