Two-factor two-dimensional code door opening system based on dynamic token and implementation method
A dynamic token, two-factor technology, applied in the field of information security, can solve the security problems of QR code door opening, the inability to realize QR code door opening, and the inability to realize transmission door opening, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
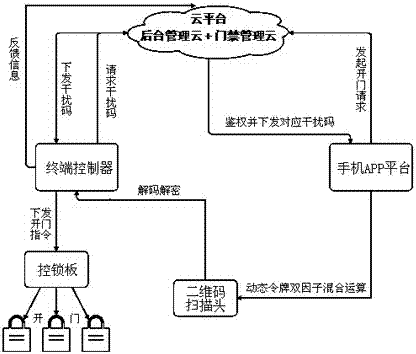
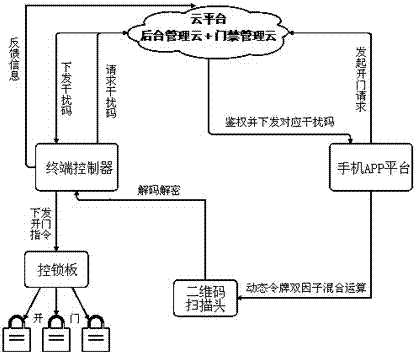
[0017] Such as figure 1 A dynamic token two-factor two-dimensional code door opening system shown includes a cloud management service platform, a mobile phone APP platform, and a terminal controller, and each system calls each other for services, wherein:
[0018] The cloud management service platform implements communication with the mobile phone APP by calling webservice from the Internet, provides identity authentication and authentication for mobile phone APP user login, and provides user authority management and authorization; realizes instant communication with the terminal controller through the MQTT protocol of the Internet of Things, and manages Terminal controller device ID and physical address; issue user login information and interference codes to the terminal controller, and record device operation information, door opening information and error messages;
[0019] The mobile APP platform provides an entrance for user operations, which is used for user login and co...
Embodiment 2
[0022] As a preference of Embodiment 1, the one-time password refers to: the mobile phone APP initiates a door opening request, and is locally generated by an algorithm through the token seed and the current time.
[0023] There are two ways for the interference code. In the first way, if the login information is consistent with the last time, then use the locally cached interference code and the one-time password to perform a mixed operation to generate a two-factor password; in the second way, if the login user is inconsistent with the last time, then Request user information and the corresponding interference code from the cloud, and perform mixed operations on the requested interference code and one-time password to generate a two-factor password; encrypt the two-factor password to generate a challenge code, generate a QR code based on the challenge code, and display it on the mobile phone APP side.
[0024] After the local decryption, the terminal controller compares the ...
Embodiment 3
[0027] The present invention provides a dynamic token two-factor two-dimensional code door opening system to realize three door opening scenarios, while ensuring the security of information in each scenario and the legality of the identity of the person who opens the door:
[0028] Scenario 1: Open the door remotely.
[0029] The communication connection between the access control system and the cloud platform is established through the Internet of Things protocol, and the cloud platform can monitor the access control status (online and offline) of the emergency station / emergency warehouse. The cloud initiates a door-opening request (opening user, corresponding device, opening authority, time, etc.), converts the request into a door-opening command and encrypts it. Through the MQTT protocol of the Internet of Things, an instruction is sent to the terminal controller (the instruction is valid once), and the terminal receives the instruction to decrypt and execute the operation ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com