Method and device for processing authentication information
A technology of authentication information and processing methods, applied in data processing applications, commerce, instruments, etc., can solve problems such as unfavorable user experience consistency, authentication information dispersion, redundancy, etc., to achieve simple and fast access, improve consistency, and fast The effect of development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
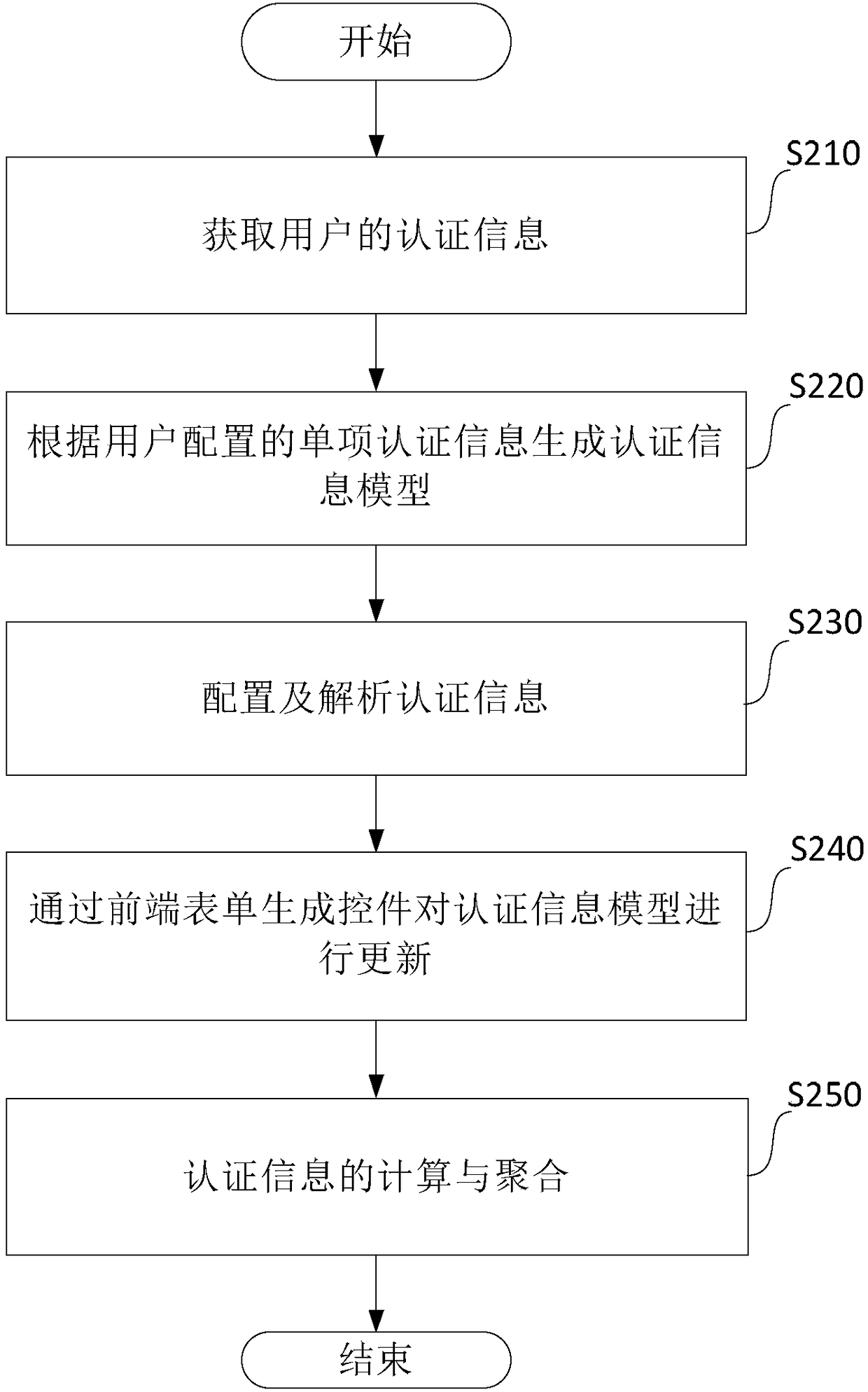
[0059] In this embodiment, another authentication information processing method is proposed, combining figure 2 , including the following steps:
[0060] S210. Obtain authentication information of the user.
[0061] The differentiation of authentication information is mainly reflected in two aspects, one is that the scene determines the authentication content, and the other is the authentication content itself.
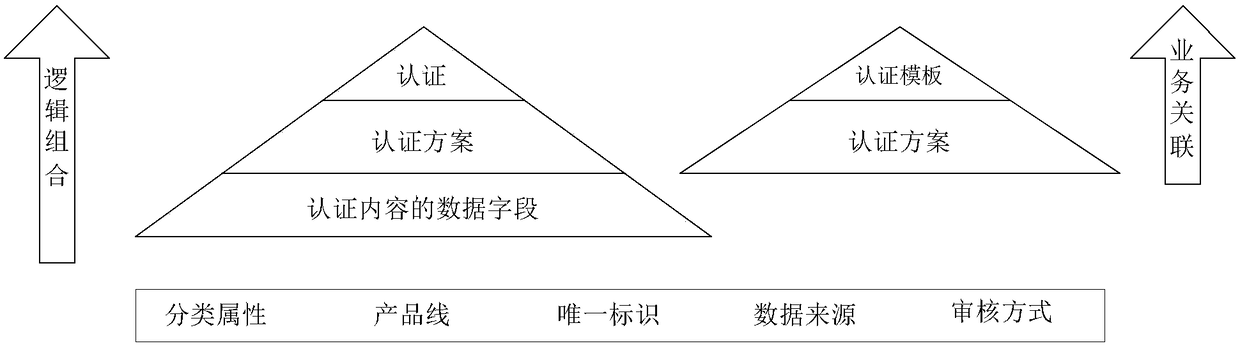
[0062] For scenarios to determine authentication content, for the sake of versatility and scalability, this embodiment can locate a set of authentication information from the following dimensions for specific business scenarios:
[0063] (1), product line ID: between each product line, authentication information can include multiple copies;
[0064] (2), unique identification ID: within the product line, the same type of certification information can include multiple copies;
[0065] (3), authentication object ID: usually refers to the user's account, and can also...
Embodiment 2
[0095] In this embodiment, another authentication information processing method is proposed, combining Figure 7 , including the following steps:
[0096] S710. Acquire authentication information of the user.
[0097] In order to unify the storage form of all authentication information, combine Figure 8 As shown, this embodiment summarizes all authentication data.
[0098] First, divide the basic types of data fields according to the data form:
[0099] Text: usually includes plain text information, which may have regular restrictions, sensitive word restrictions, etc.;
[0100]Multiple choice: configurable setting options, as well as the business meaning of each option, and the processing logic of the corresponding business;
[0101] Image: You can control the number and size of uploads, support online preview, asynchronous multi-scale compression, etc.;
[0102] Time: Support time points or time periods, and configure time-triggered business processes;
[0103] Addres...
Embodiment 3
[0153] In this embodiment, another authentication information processing device is proposed, combining Figure 10 As shown in , including the following devices:
[0154] A device for obtaining authentication information of a user (hereinafter referred to as "information obtaining device") 1010;
[0155] A device for generating an authentication information model (hereinafter referred to as "generating device") 1020 according to the single item of authentication information configured by the user;
[0156]A device for configuring and analyzing authentication information (hereinafter referred to as "parsing device") 1030;
[0157] A device for updating the authentication information model through the front-end form generation control (hereinafter referred to as "updating device") 1040;
[0158] A device for computing and aggregating authentication information (hereinafter referred to as "information computing device") 1050 .
[0159] The differentiation of authentication info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com