Non-current terminal password input method
A password input and terminal technology, which is applied in the field of password input methods, can solve the problems that deposit co-owners cannot supervise and manage funds, cannot provide real-time monitoring means, and cannot provide efficient real-time monitoring means, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The content of the present invention will be described in detail below in conjunction with the accompanying drawings and embodiments of the description:
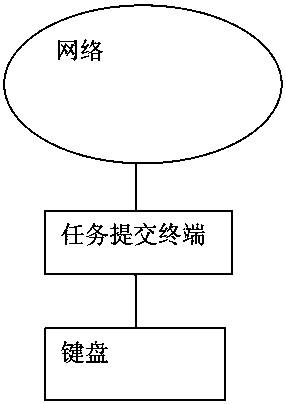
[0023] figure 1 It is a schematic diagram of an existing password input method. No matter what the application is, the process is to submit a task request on this terminal and enter the confirmation password. For the use environment exposed to the Internet where hacking viruses are flying everywhere and various phishing websites are hard to guard against, this password input method has great security risks.
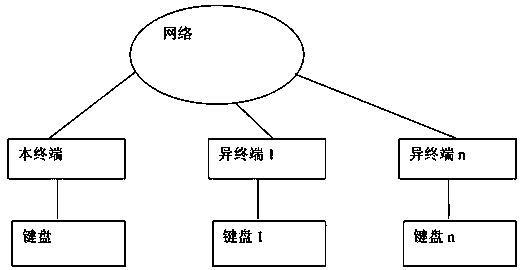
[0024] figure 2 It is a schematic diagram of the password input method of the present invention.
[0025] The technical solution of the present invention is as follows: the confirmation password input of the submitted task needs to be completed on at least one different terminal. The program has the following basic input methods:
[0026] Input
This terminal
different terminal 1
differ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com