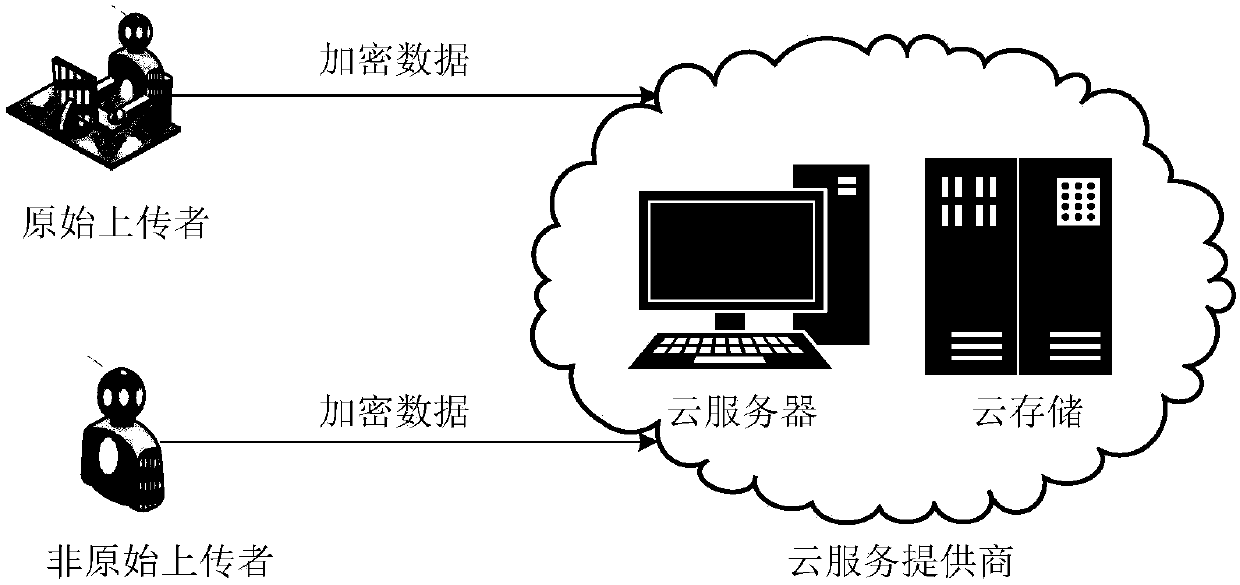
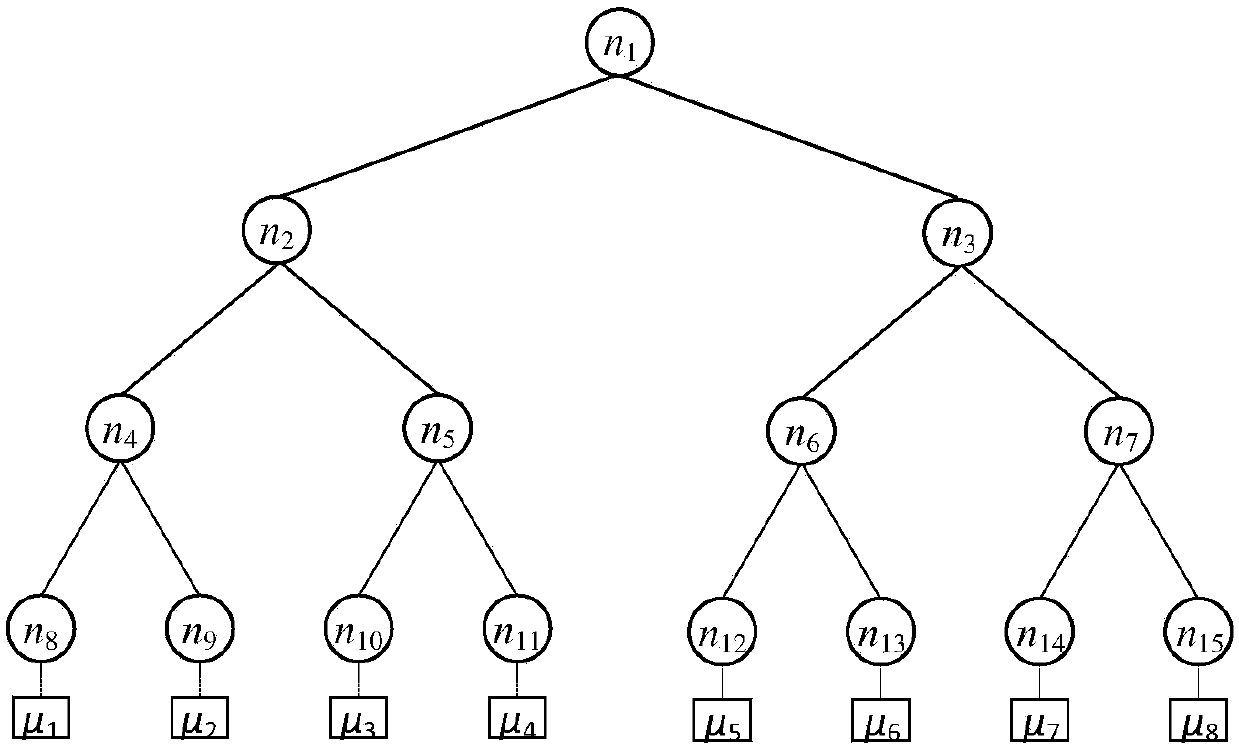
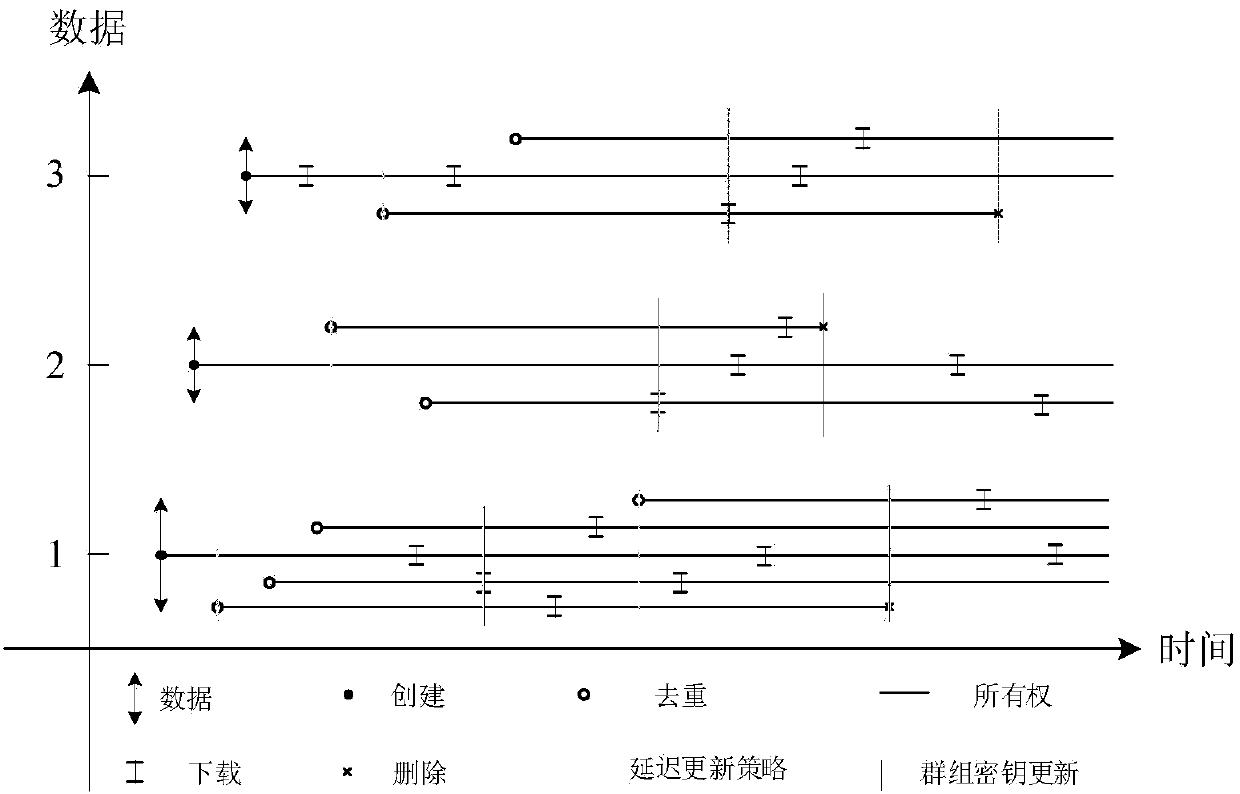
Data deduplication system with ownership management for cloud ciphertext storage and data deduplication method thereof
A technology of ownership and cloud storage, applied in transmission systems, electrical digital data processing, special data processing applications, etc., can solve the problems of repeated forgery attacks, ciphertext substitution attacks, fraudulent server trust, large communication overheads, and computational overheads
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0128] In order to evaluate the performance of the present invention, the implementation of the following example is compared with the performance of the existing security deduplication scheme at different stages.
[0129] In this embodiment, the parameters are set as follows: b=16, s=100, l=8, n=16; the file sizes are 16MB, 64MB, 256MB and 1024MB respectively.
[0130] Embodiment performance evaluation is as follows:
[0131] 1) Convergent key generation: such as Figure 4 As shown in , this section evaluates the computational overhead of different schemes in the stage of generating converged encryption keys. It can be seen that the key generation time grows linearly with the file size.
[0132] 2) Data upload: Figure 5(a) is an evaluation of the computational overhead of the original uploader during the data upload phase. It can be seen that the calculation overhead of the present invention is superior to other schemes, and supports single-user data block-level data dedup...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com