Program protection method and device
A program protection and program technology, applied in the field of program protection methods and devices, can solve problems such as inability to effectively prevent hooks, fail to identify hook types, and hidden safety hazards, and achieve the effects of reducing computational complexity, reducing waste, and improving operating speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
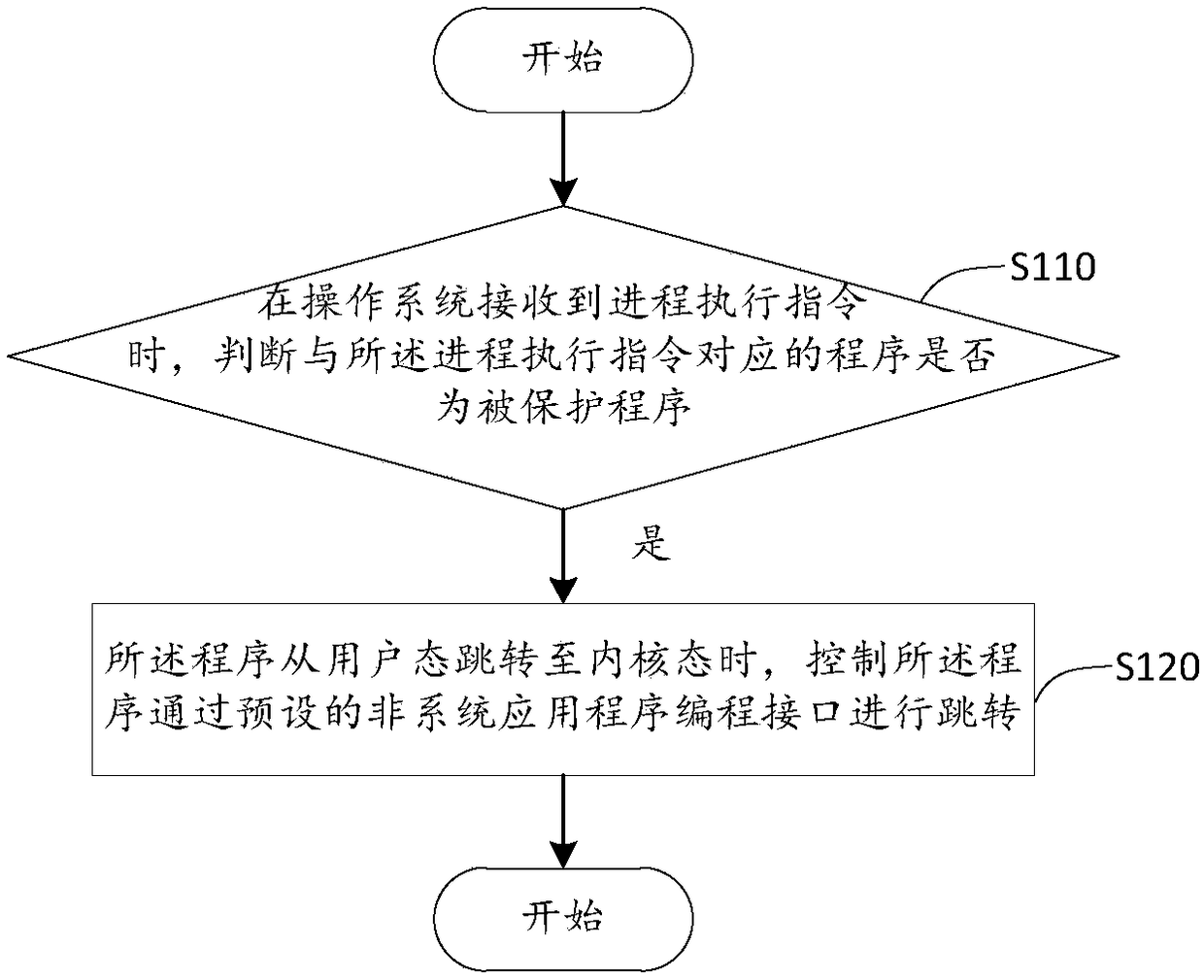
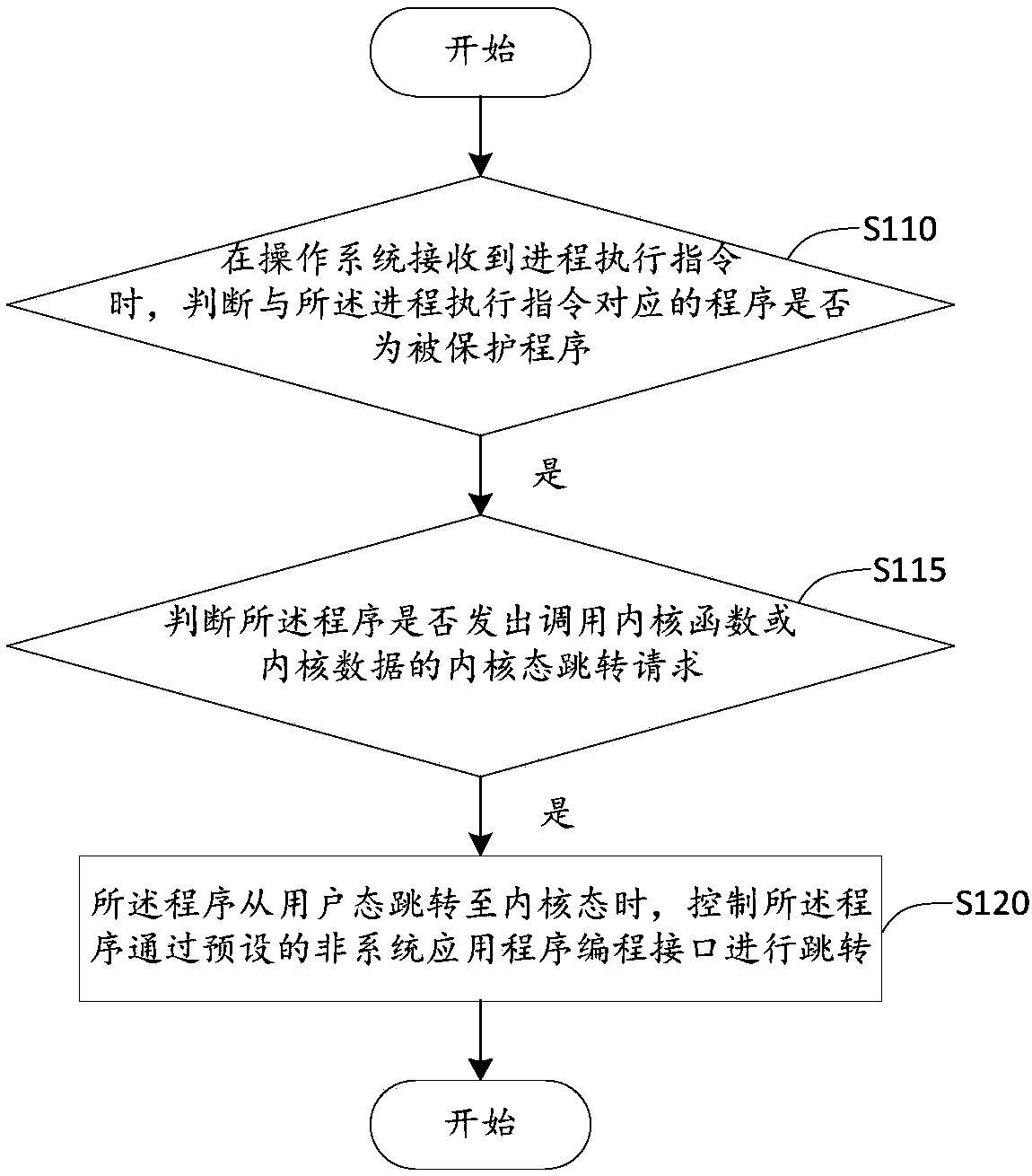
[0027]The applicant's research has found that with the development and popularization of computer and network technologies, more and more malicious programs make the normal programs jump to the malicious programs by hooking the normal programs that are running normally, and serious Threat to data security and network security. Among them, HOOK is a system mechanism provided in Windows to replace the "interrupt" under DOS, which is translated into "hook" or "hook" in Chinese. After hooking a specific system event, once a Hooked event occurs, the program that hooks the event will receive a notification from the system, and the program can respond to the event at the first time; use another In this way, HOOK is actually a program segment for processing messages, which is hooked into the system through system calls. Whenever a specific message is sent, before reaching the destination window, the hook program first captures the message, that is, the hook function first obtains con...
no. 2 example
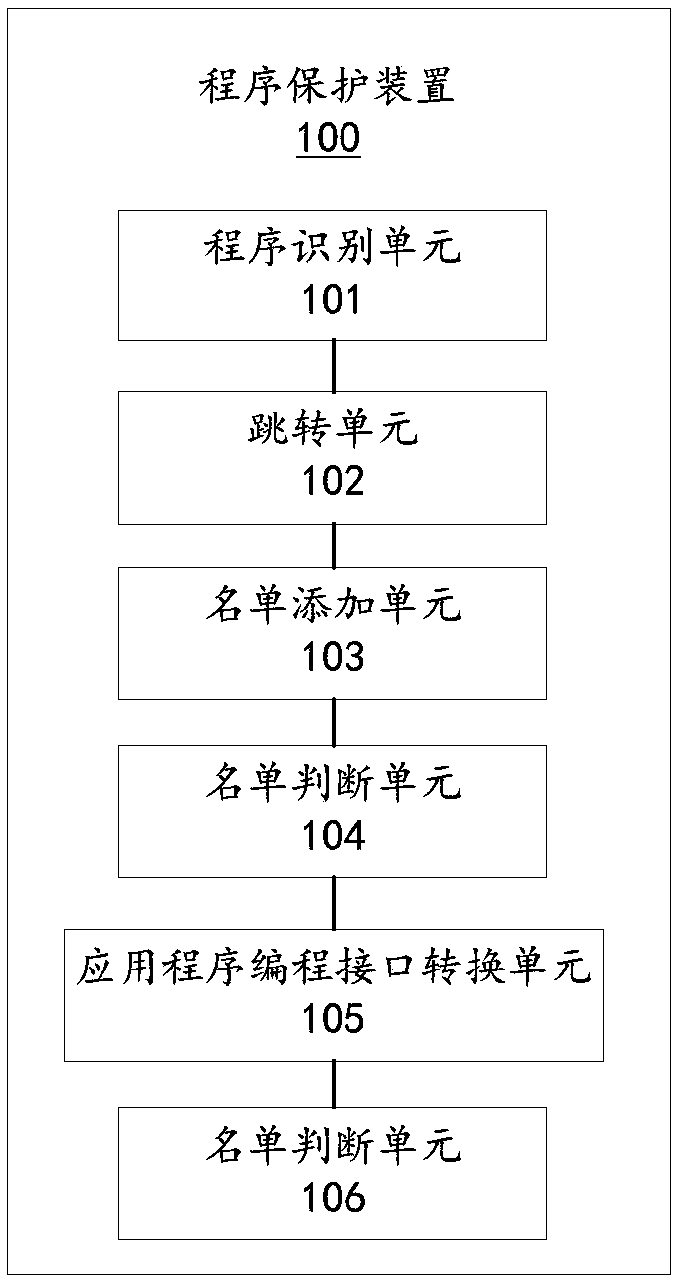
[0037] In order to better implement the above program protection method, the second embodiment of the present invention provides a program protection device 100, please refer to image 3 , image 3 A block diagram of a program protection device provided in this embodiment.
[0038] The program protection device 100 includes a program identification unit 101 and a jump unit 102 . The program identification unit 101 is configured to determine whether the program corresponding to the process execution instruction is a protected program when the operating system receives the process execution instruction. The jump unit 102 is configured to control the program to jump through a preset non-system application programming interface when the program is a protected program and the program jumps from the user state to the kernel state.
[0039] The program protection device 100 also includes a list adding unit 103 and a list judging unit 104 . The list adding unit 103 is used for addi...
no. 3 example
[0043] Please refer to Figure 4 , Figure 4 A structural block diagram of an electronic device 200 applicable to the embodiment of the present application is shown. The electronic device 200 may include a program protection device 100 , a memory 201 , a storage controller 202 , a processor 203 , a peripheral interface 204 , an input and output unit 205 , an audio unit 206 , and a display unit 207 .
[0044] The memory 201, storage controller 202, processor 203, peripheral interface 204, input and output unit 205, audio unit 206, and display unit 207 are electrically connected to each other directly or indirectly to realize data transmission or interact. For example, these components can be electrically connected to each other through one or more communication buses or signal lines. The program protection device 100 includes at least one software function module that can be stored in the memory 201 in the form of software or firmware (firmware) or solidified in an operating...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com