Hybrid searchable encryption method and hybrid searchable encryption system
一种加密方法、混合型的技术,应用在密码学,物联网和云存储安全领域,能够解决边服务器计算与网络资源浪费、使用成本负担、拖慢网络传输时间等问题,达到降低计算量和使用成本、降低使用成本与、提高搜索效率的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
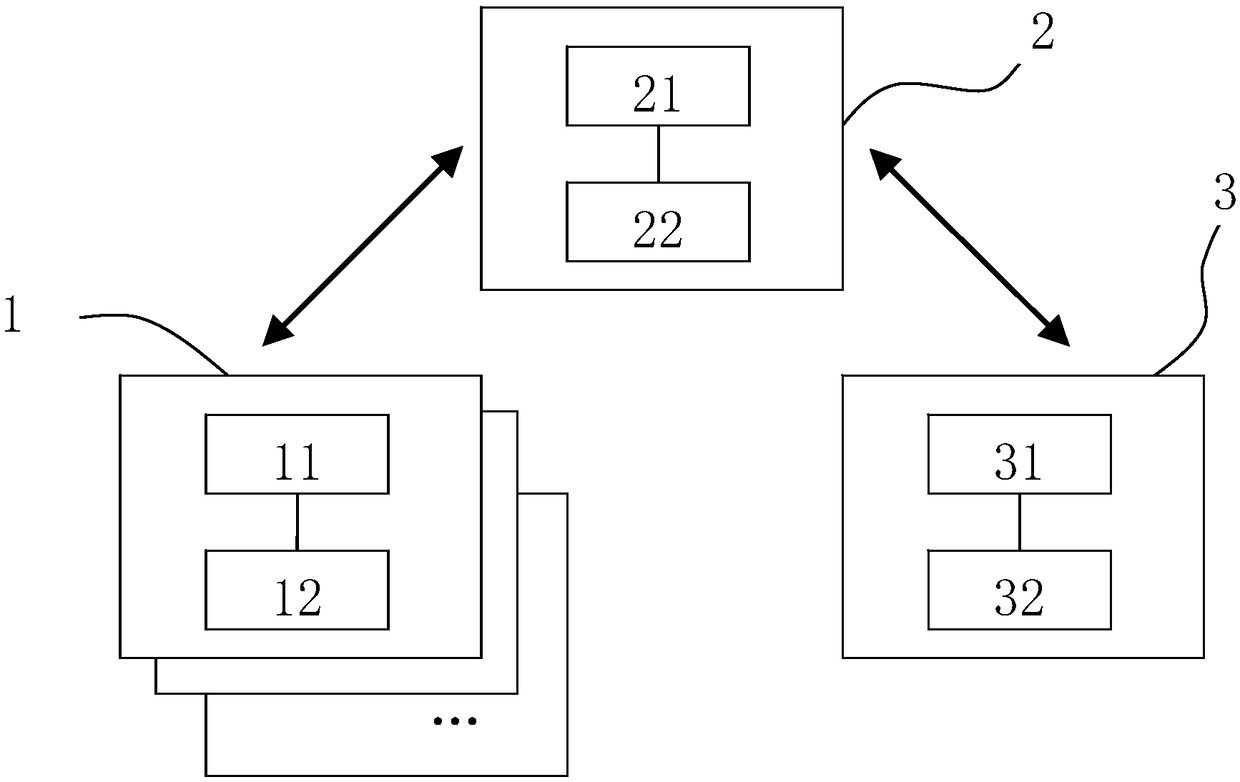
[0065] refer to figure 1 , this embodiment discloses a hybrid searchable encryption method. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0066] This embodiment discloses a hybrid searchable encryption method, including at least one first computing device 1, and the first processor 11 of the first computing device 1 may be configured as:
[0067] Encrypting the data using the first symmetric key to obtain the first ciphertext of the data and encrypting the keywords associated with the data using the second symmetric key to obtain a searchable keyword first ciphertext associated with the first ciphertext of the data, and encrypting the first ciphertext of the data A ciphertext and keywords The first ciphertext is stored in the first memory 12 of the first computing device 1 . The first computing device of the present invention encrypts data with a first symmetric key, and encry...
Embodiment 2
[0101] This embodiment is a further improvement on Embodiment 1, and repeated content will not be repeated here. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0102] refer again figure 1 , the present invention also discloses a hybrid searchable encryption system, which is suitable for executing each method step described in the present invention, so as to achieve the expected technical effect.
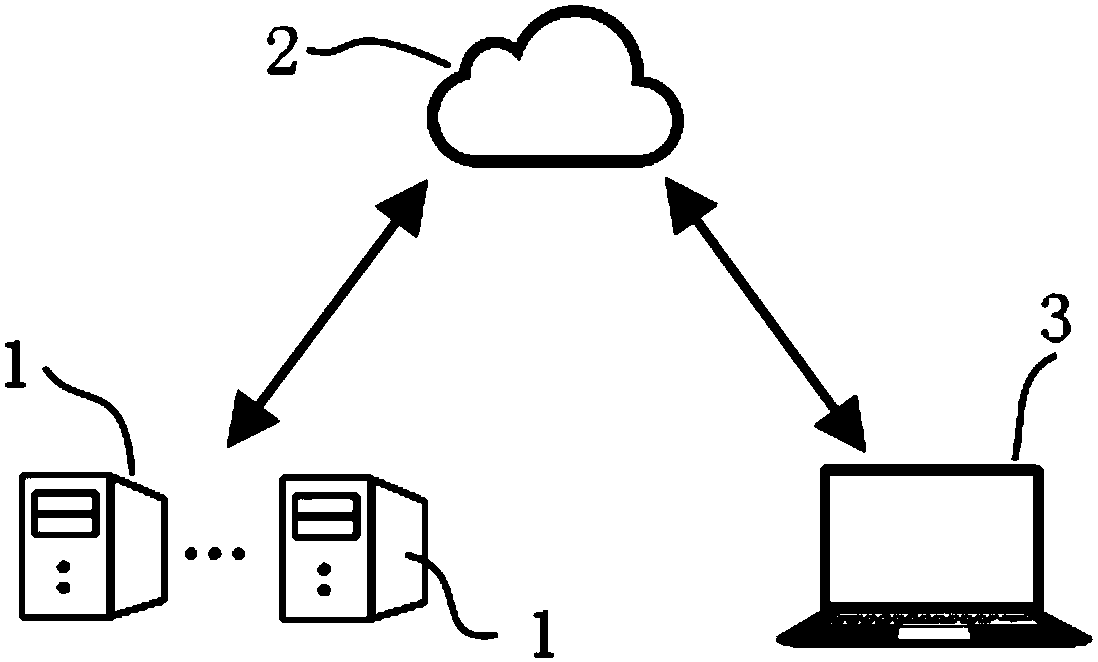
[0103] According to a preferred embodiment, the system may include a first computing device 1 , a second computing device 2 and a third computing device 3 . The system may comprise at least one first computing device 1 . The first processor 11 of the first computing device 1 may be configured to:
[0104] Encrypting the data using the first symmetric key to obtain the first ciphertext of the data and encrypting the keywords associated with the data using the second symmetric key to o...
Embodiment 3
[0108]This embodiment is a further improvement on Embodiments 1 and 2 or their combination, and repeated content will not be repeated here. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0109] This embodiment discloses a hybrid searchable encryption method.
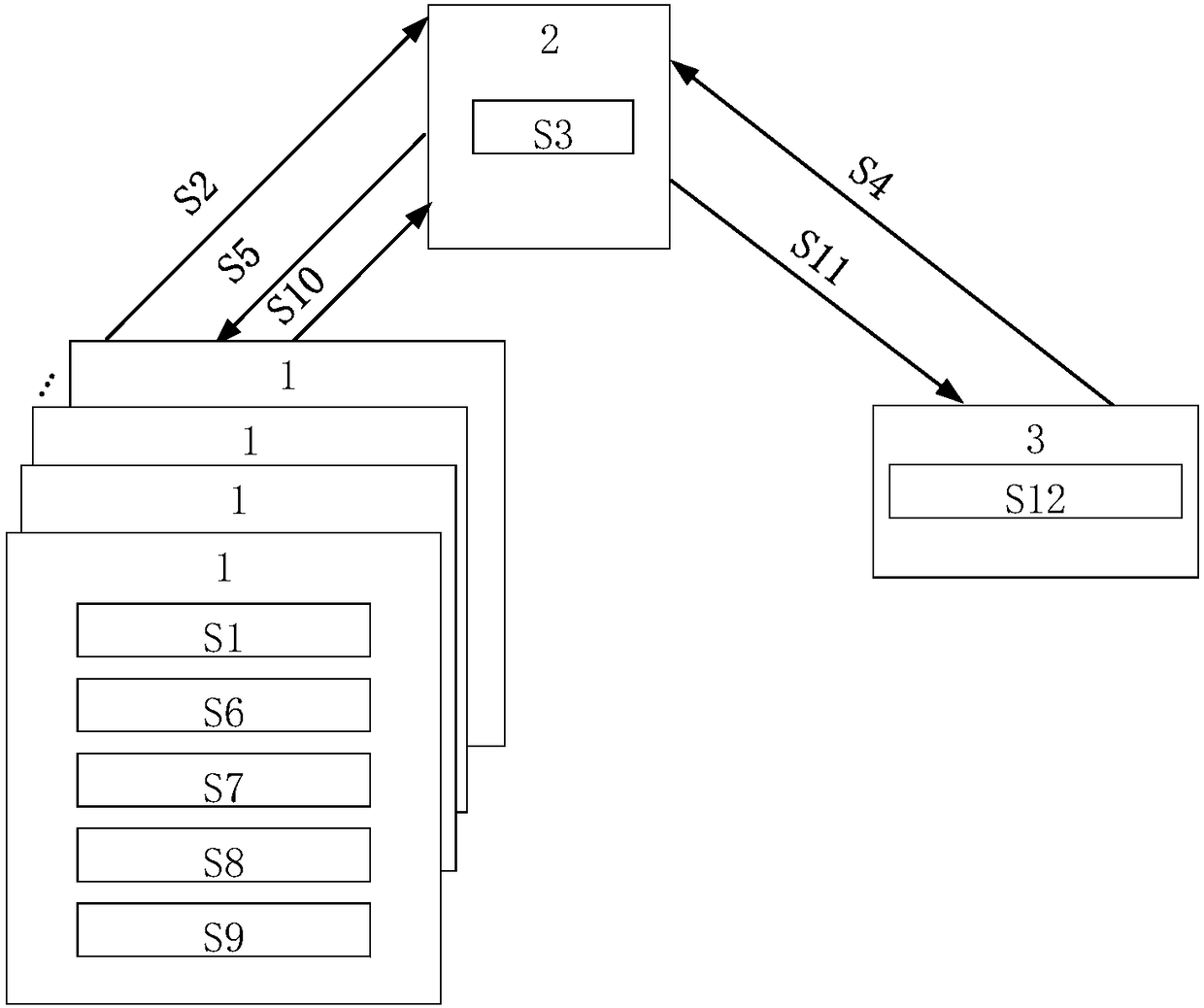
[0110] According to a preferred embodiment, the method of the present invention may include: the side server uses the user public key Pk to encrypt the keyword W, and outputs the PEKS ciphertext C of the keyword W W And upload it to the cloud server in the way it is associated with the side server.
[0111] According to a preferred embodiment, the method of the present invention may also include: the cloud server passes the PEKS ciphertext C when the user uses the keyword W to initiate a search request W Find the corresponding edge server uploading the keyword W and forward the search request to the corresponding edge ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com