Online protocol format inference method based on multiple sequence alignment
A protocol format and multi-sequence technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems that cannot meet the needs of online protocol analysis and take a long time, and achieve the effect of meeting the time requirement and ensuring the effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
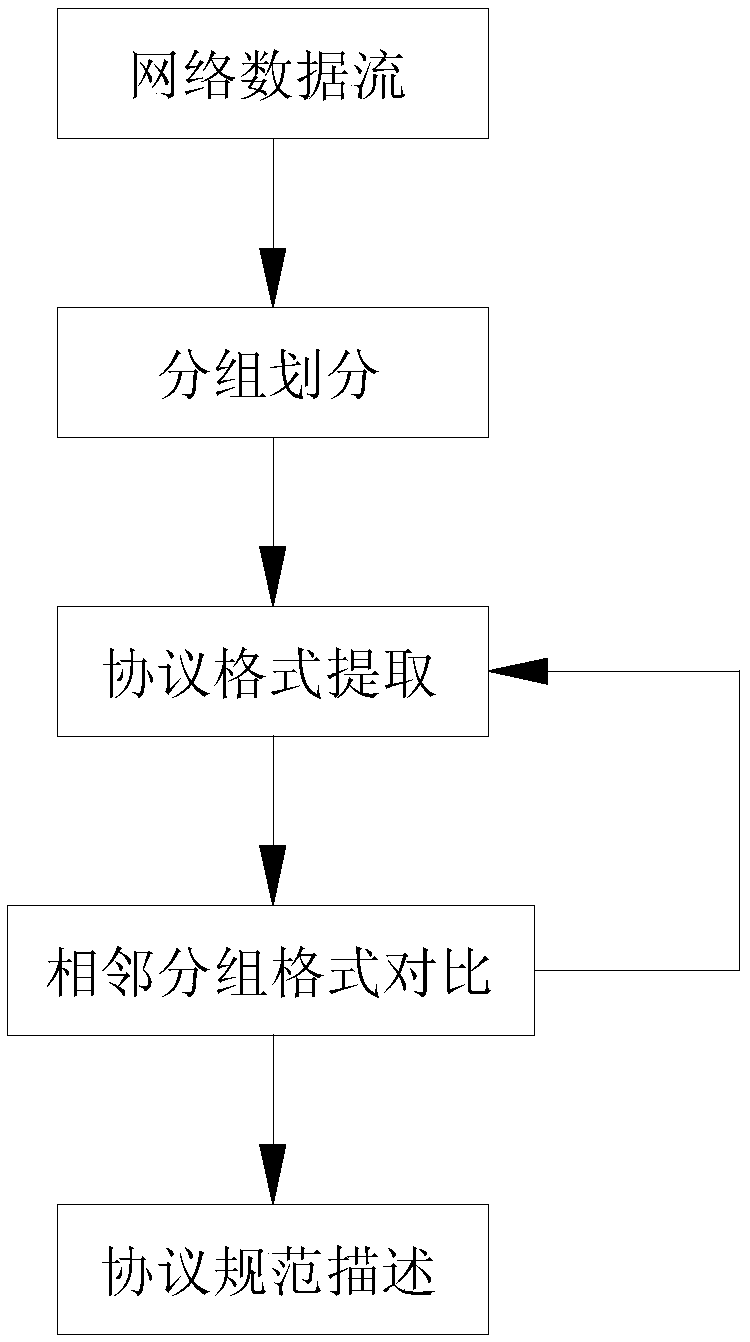
[0042] Include the following steps:
[0043] Step S1: Network traffic acquisition and division into different groups
[0044] Obtain traffic from the network through wireshark or pcap, and then use the first N packets as a subflow according to the packet acceptance order, and set N to 500 in order to ensure the response time.
[0045] flow0= (1)
[0046] Step S2: Perform multiple sequence alignment
[0047] Taking the http protocol as an example, the three groups before and after are respectively,
[0048] Among them, p0={GET / cgi-bin / whois.pl HTTP / 1.0 Host: arin.net User-Agent:Opera Accept: text / xml}, p1={GET / index.html HTTP / 1.0 Host: www.yahoo .comUser-Agent: Mozilla / 5.0 Accept: text / xml}, p2={GET / HTTP / 1.0 Host: www.google.com User-Agent: IE4.0 Accept: text / xml}.
[0049] After sequence comparison, the result is GET / ############ HTTP / 1.0 Host: ############# User-Agent: ########## Accept: text / xml.
[0050] Simultaneous record processing time was 60 seconds.
[005...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com