Stack protecting method based on program instrumentation and dynamic information verification
A dynamic information and stake insertion technology, applied in the fields of system and software security and computer, can solve the problems of easy cracking, performance loss, poor deployability, etc., to achieve wide applicability, low execution speed loss, and low program performance loss. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
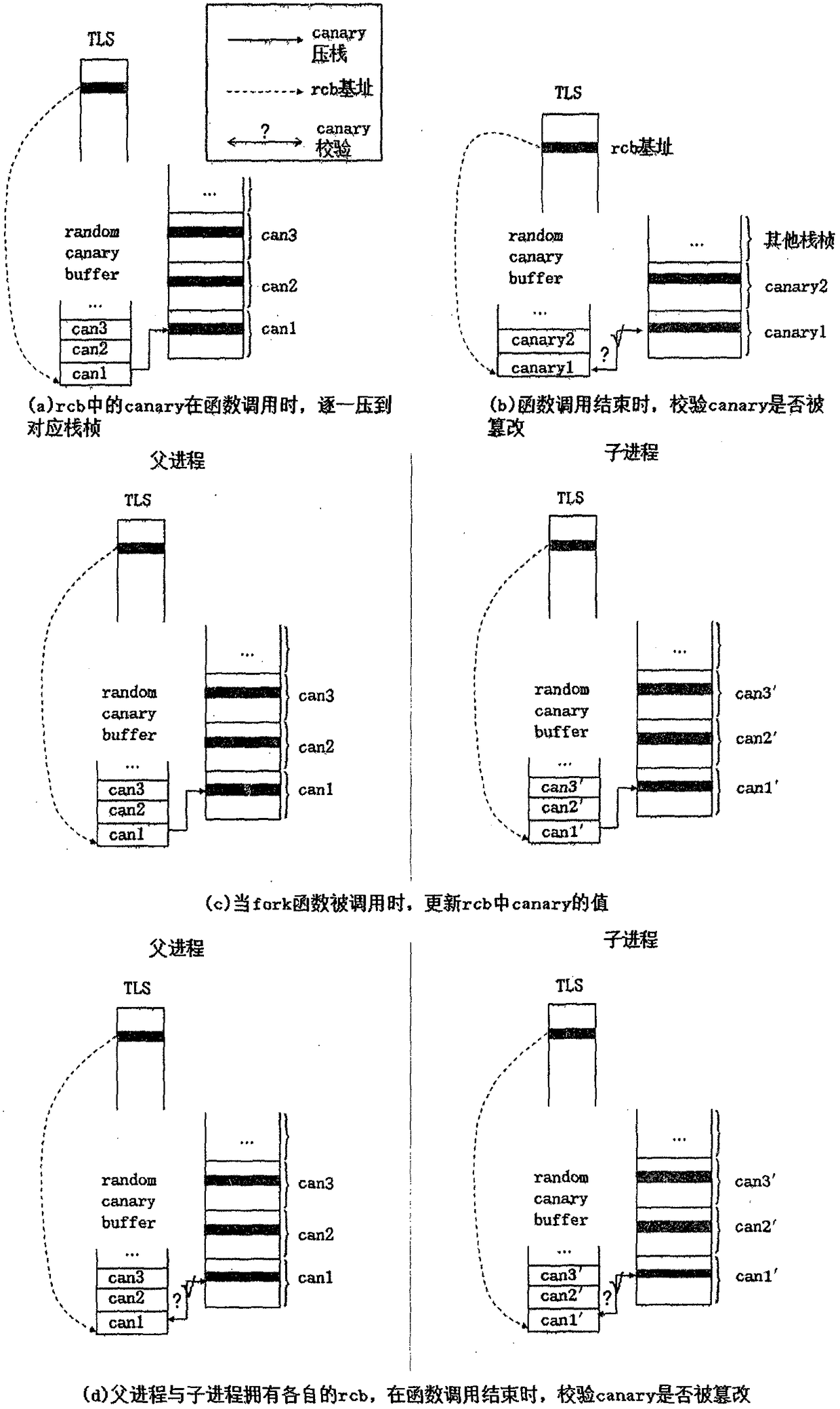
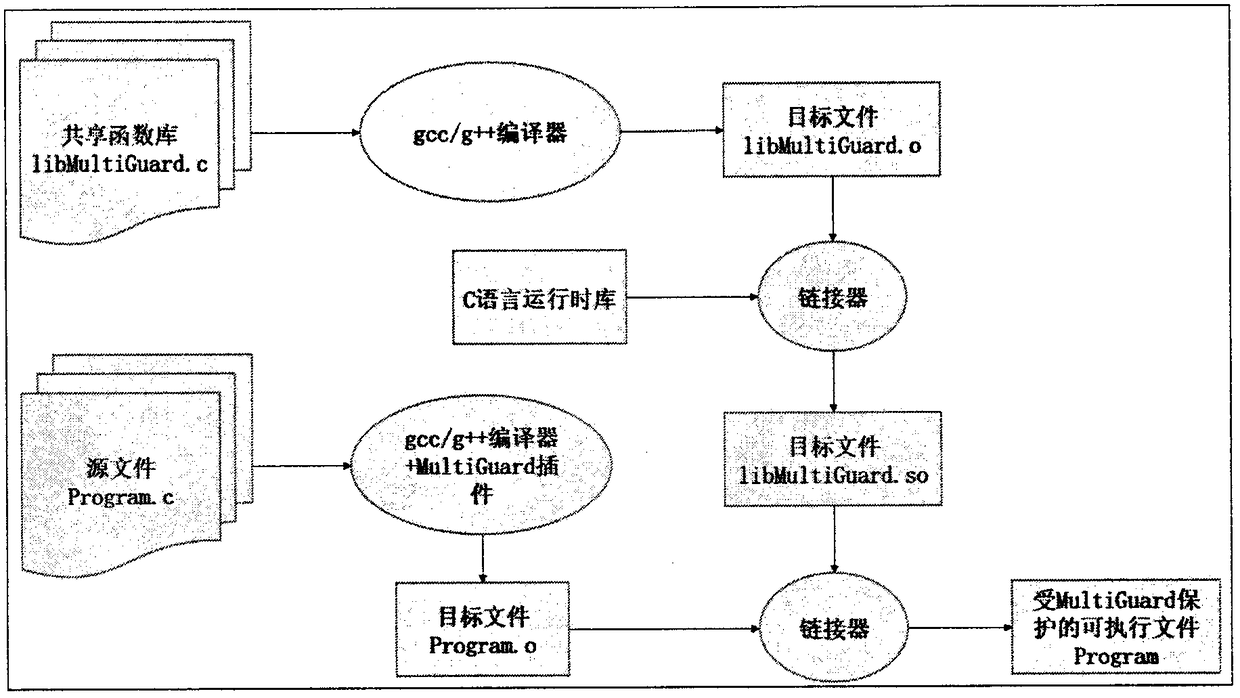
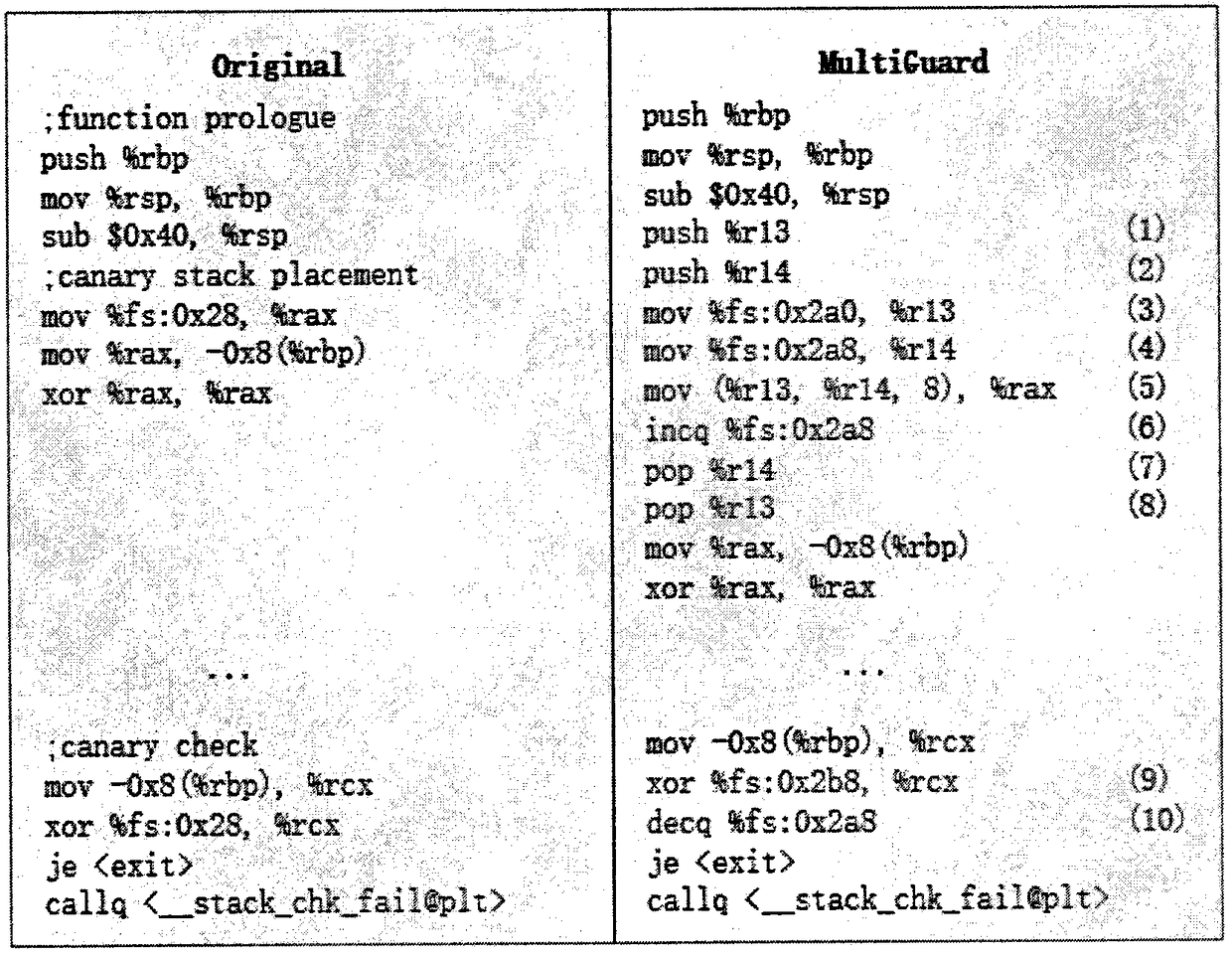
[0029]The method of the invention firstly compiles the dynamic shared library libMultiGuard.so, which contains rewritten library functions and function functions. The purpose of rewriting the library function is to perform additional user-defined behaviors when the function is called. After the pthread_create and fork functions are rewritten, when the process is created, the user-specified canary buffer, the buffer's entry address, The size and index information are stored in TLS; the functions include the generation and placement of canary, and the erasure of canary buffer. Simultaneously, the inventive method has realized a GCC plug-in MultiGuard, is used for inserting and placing, checking canary and the code segment of error handling when compiling source program, when each function takes place calling, gets canary dynamically from canary buffer, and It pushes the stack to 8 bytes before the return address of the function stack frame. When the function call ends, the check...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com